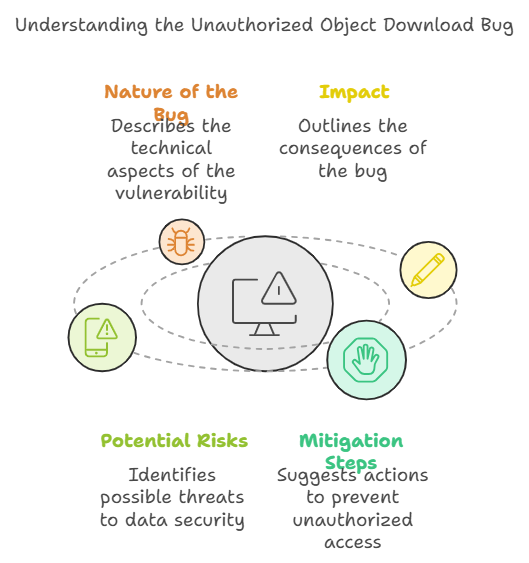
This document outlines the critical security vulnerability identified as the Unauthorized Object Download Bug. It describes the nature of the bug, its impact, potential risks, and the necessary mitigation steps to prevent unauthorized access to sensitive data. The findings emphasize the importance of robust security measures to protect customer information and maintain compliance with data privacy laws.
Description
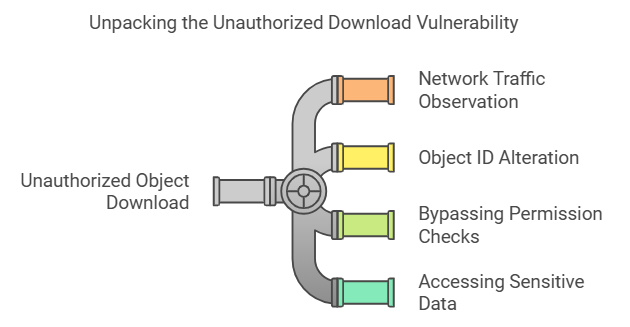
Users could download any object by observing network traffic, altering the object ID, and resending the request. This bypassed permission checks entirely, allowing unauthorized access to potentially sensitive data.
Impact
Severity: High
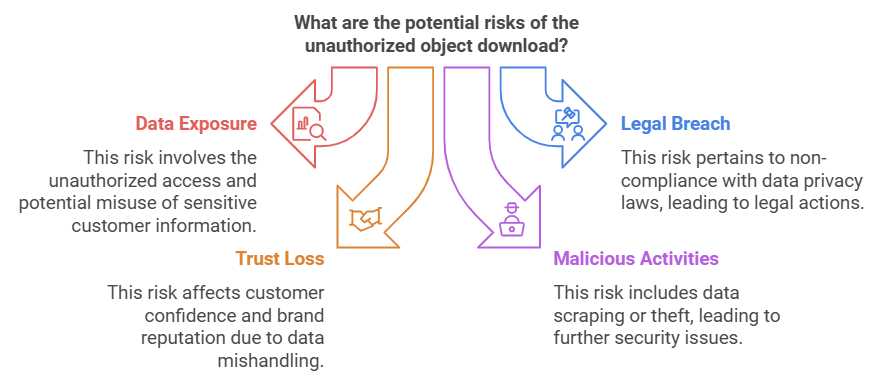
Potential Risks:
- Exposure of sensitive customer data.
- Breach of data privacy laws (e.g., GDPR, CCPA), leading to legal consequences.
- Loss of customer trust and reputation damage.
- Potential for data scraping, intellectual property theft, or other malicious activities.
Likelihood of Exploitation:
High, as the exploit required minimal technical expertise and tools.
Time to Discovery:
2 years after being reported internally.
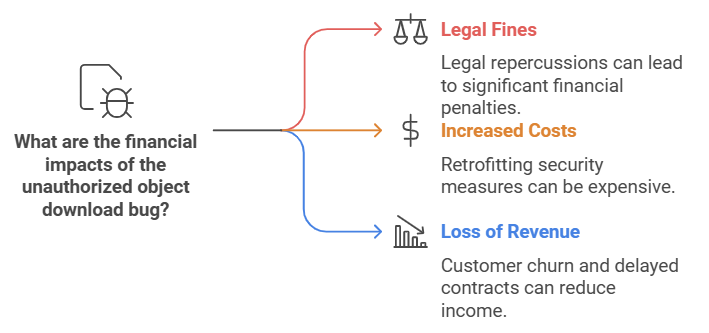
Financial Impact:
- Legal fines and penalties.
- Increased costs to patch and secure the system retroactively.
- Loss of revenue due to churned customers or delayed contracts.
Root Cause:
- Lack of proper authorization checks on object download requests.
- Poor endpoint validation logic.
Mitigation Steps:
- Implement endpoint-level access controls and authorization checks.
- Use secure tokens for request validation.
- Add logging and monitoring for anomalous download patterns.

By addressing these issues, organizations can significantly reduce the risk of unauthorized access and protect sensitive data from potential exploitation.
Want to read more Bug Case Studies? Click here.