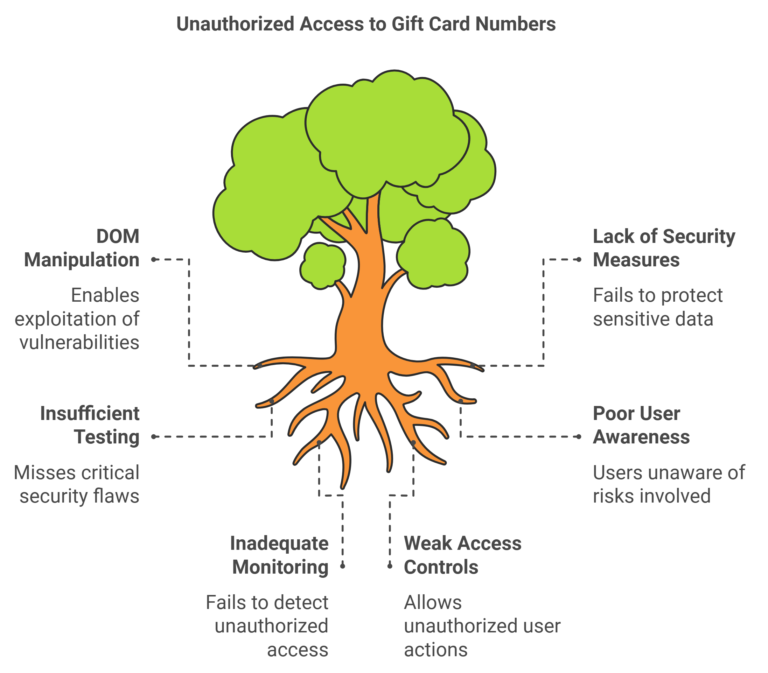
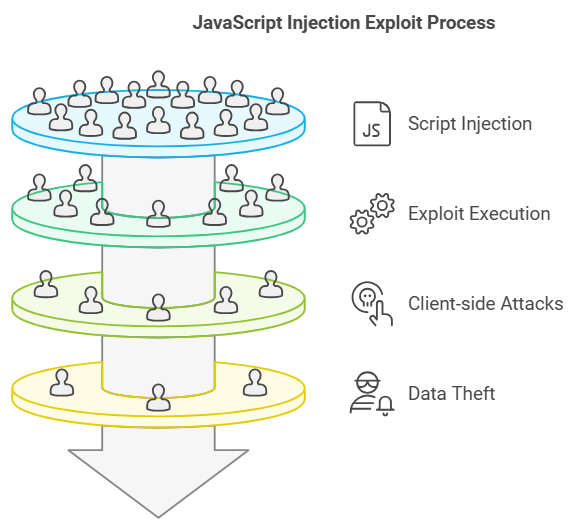
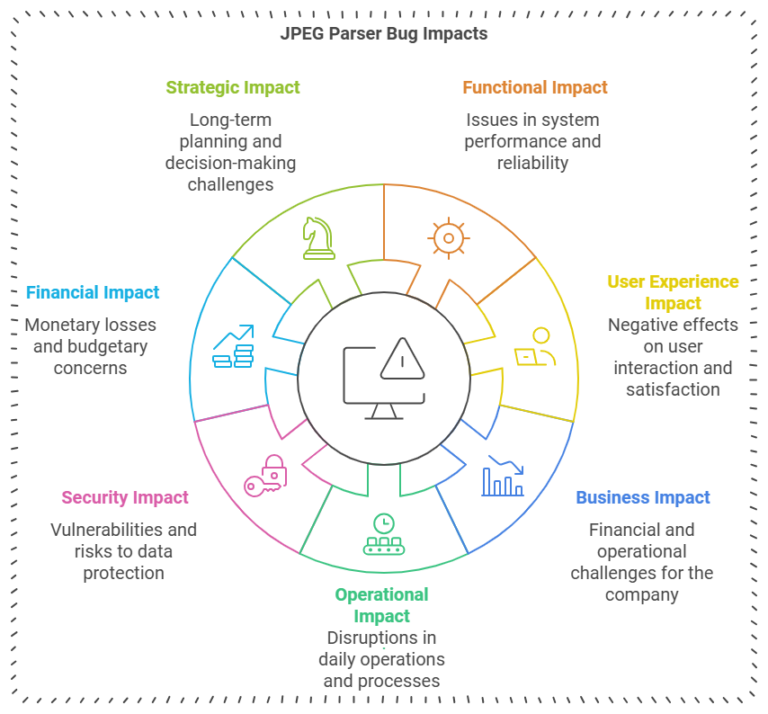
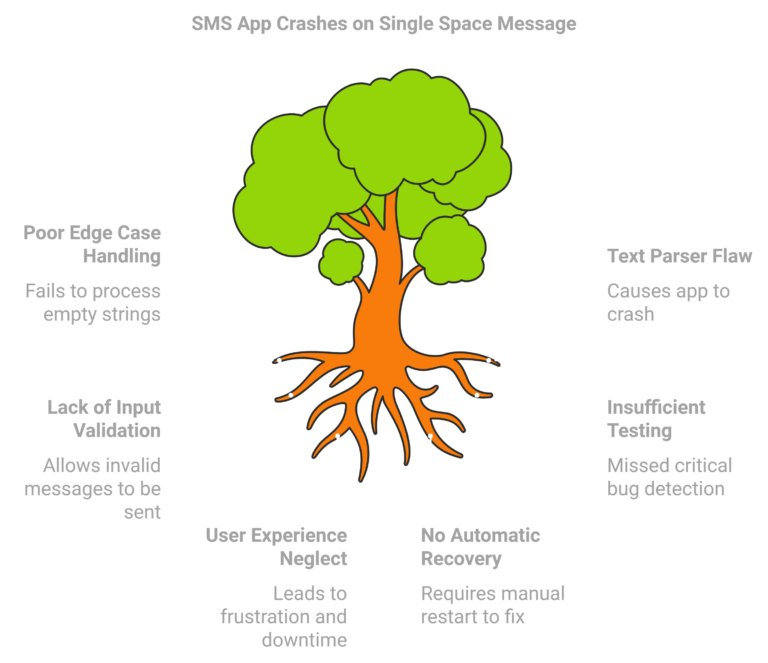
How A System Failed: Unauthorized Object Download Bug

This document outlines the critical security vulnerability identified as the Unauthorized Object Download Bug. It describes the nature of the bug, its impact, potential risks, and the necessary mitigation steps to prevent unauthorized access to sensitive data. The findings emphasize…