Employees often turn to unauthorized software and tools, termed Shadow IT, to streamline their workflow. Though it can boost productivity, it also poses significant risks—particularly in software testing. These tools bypass standard IT checks, exposing companies to compliance, security, and integration challenges that software testers often have to untangle.
“Technology, like art, is a soaring exercise of the human imagination.” — Daniel Bell
This guide walks through the impacts of Shadow IT on software testing, with practical strategies, mind maps, and expert perspectives. 🧩
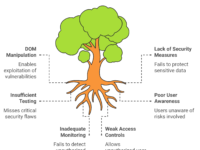
🖼️ Visualizing Shadow IT in Software Testing
Here’s a mind map to quickly capture how Shadow IT impacts testing processes, from integration challenges to security risks.
What is Shadow IT?
Shadow IT includes any unsanctioned software, services, or devices employees use without approval from the IT department. While often driven by immediate need, Shadow IT tools lack oversight, posing risks to both IT governance and testing practices.
💼 Real-World Example: Shadow IT Impact on a Financial Firm
In one case, a financial institution’s analytics team started using an unapproved app to visualize financial trends. When their IT department discovered this, they found serious data leaks and several integration failures, which took months to fix. Their testing team had to step in to identify all data dependencies, perform compatibility checks, and run security audits—a costly, time-intensive process.
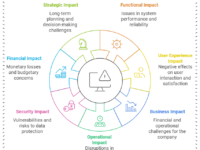
Risks of Shadow IT on Software Testing: A Closer Look
| Risk | Impact on Testing | Examples |
|---|---|---|
| Security Risks | Data leaks, compliance gaps, and unauthorized access | Personal Dropbox accounts for data storage |
| Integration Issues | Compatibility, database inconsistencies, testing delays | Slack vs. Microsoft Teams interactions |
| Documentation Lacks | Hinders testing and validation | Unvetted apps missing support documentation |
| Maintenance Hurdles | Increases technical debt and system complexities | Custom scripts lacking update support |
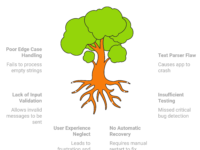
🔍 The Testing Bottlenecks Shadow IT Creates
1. Security Challenges: Data Leakage & Unauthorized Access 🔐
Without proper vetting, Shadow IT tools can expose sensitive data to breaches. Unauthorized cloud storage, messaging apps, or collaborative platforms can jeopardize the security of critical information.
“The only truly secure system is one that is powered off, cast in a block of concrete and sealed in a lead-lined room with armed guards.” — Gene Spafford
Example:
In one incident, a healthcare provider unknowingly allowed patient data to be accessed via an unapproved analytics app. Testing teams later discovered this and initiated a security review, adding both delay and remediation costs.
2. Integration Challenges: Compatibility and Documentation Issues ⚙️
Shadow IT tools often lack integration capabilities, causing compatibility issues. This becomes an even bigger problem when the tools lack documentation, making it difficult for testers to build robust integration tests.
Practical Bottleneck:
A retail company’s marketing team adopted a standalone CRM solution without IT’s knowledge. The lack of API documentation made it challenging to validate the tool’s data exchange with core systems, complicating the testing process.
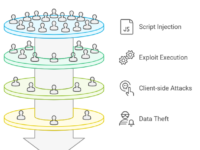
📊 Workflow: Managing Shadow IT in Software Testing
Here’s a simplified workflow for managing Shadow IT risks during software testing.
This workflow provides a roadmap for testers and IT teams, guiding them through the process of identifying, evaluating, and securing Shadow IT solutions.
Proactive Tools for Testing in a Shadow IT Environment
Managing Shadow IT requires a proactive approach. Here are key tools to streamline testing and monitoring efforts:
| Tool | Purpose | Description |
|---|---|---|
| Splunk | Risk Analysis | Scans network for unapproved tools |
| Selenium | Automated Testing | Ensures compliance in web apps |
| AppDynamics | Real-time Monitoring | Tracks system interactions |
| Fortinet Security | Network Security | Flags unauthorized access |
Best Practices for Software Testing in Shadow IT
- Leverage a Sandbox Environment 🧪
Testing unapproved tools in a sandbox minimizes risk to the production environment while allowing for detailed compatibility and security assessments. - Collaborate with Security Teams 🛡️
Maintain close alignment with IT and security departments to flag risks early and create better mitigation strategies. - Document All Findings 📑
Even when tools are unapproved, maintaining documentation on testing and risk analysis helps create a knowledge base and informs future decisions. - Involve End-Users in Testing 🧑💻
Users often know unvetted tools best, so involve them in testing to understand their purpose and ensure functionality while assessing risks.
📹 Video Walkthrough: Implementing Security Testing for Shadow IT
Explore a practical demonstration on implementing sandbox security testing for unauthorized tools, covering common vulnerabilities and compliance checks.
Key Takeaways
While Shadow IT can enhance agility, it creates substantial challenges for testing teams who must juggle security, integration, and compliance. Balancing flexibility with control is critical. By following best practices, maintaining detailed documentation, and collaborating with IT departments, testers can mitigate risks associated with Shadow IT and better safeguard their organizations.
“It takes 20 years to build a reputation and a few minutes of cyber-incident to ruin it.” — Stephane Nappo
Additional Resources & Further Reading
- Risks and benefits of shadow IT: Visit here.
- IT Governance Best Practices to Manage Shadow IT
Shadow IT will continue to challenge traditional testing frameworks. But with a structured approach and the right tools, testers can turn this challenge into an opportunity to strengthen their organizations’ tech environments.