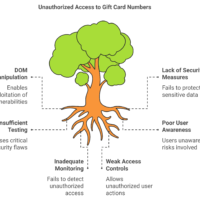
This document outlines the critical security vulnerability identified as the Unauthorized Object Download Bug. It describes the nature of the bug, its impact, potential risks, and the necessary mitigation steps to prevent unauthorized access to sensitive data. The findings emphasize the importance of robust security measures to protect customer information and maintain compliance with data privacy laws.
Description
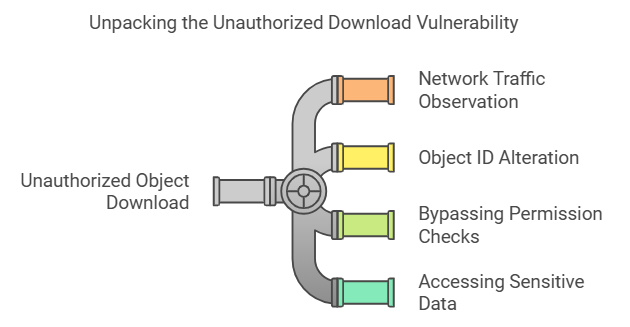
Users could download any object by observing network traffic, altering the object ID, and resending the request. This bypassed permission checks entirely, allowing unauthorized access to potentially sensitive data.
Impact
Severity: High
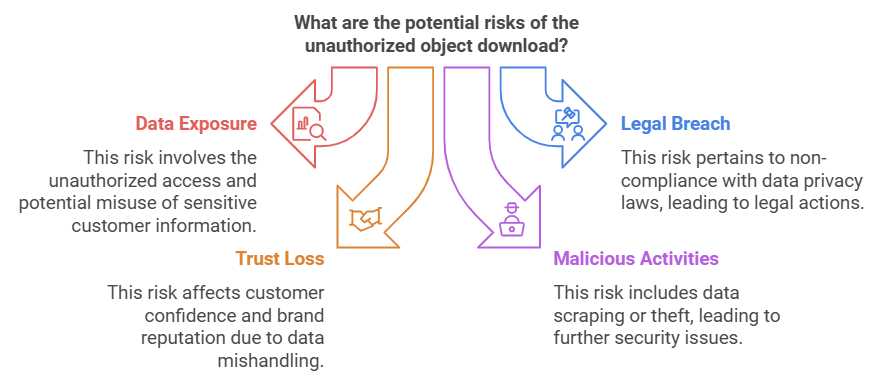
Potential Risks:
- Exposure of sensitive customer data.
- Breach of data privacy laws (e.g., GDPR, CCPA), leading to legal consequences.
- Loss of customer trust and reputation damage.
- Potential for data scraping, intellectual property theft, or other malicious activities.
Likelihood of Exploitation:
High, as the exploit required minimal technical expertise and tools.
Time to Discovery:
2 years after being reported internally.
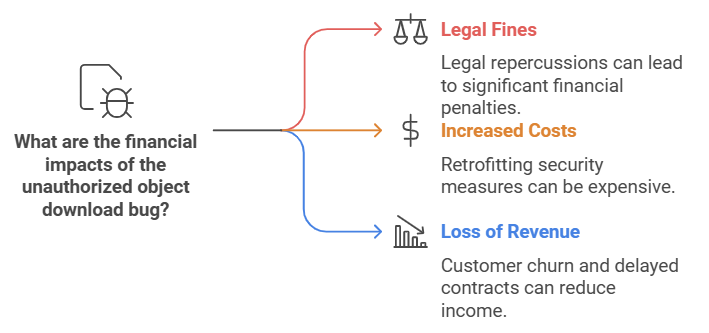
Financial Impact:
- Legal fines and penalties.
- Increased costs to patch and secure the system retroactively.
- Loss of revenue due to churned customers or delayed contracts.
Root Cause:
- Lack of proper authorization checks on object download requests.
- Poor endpoint validation logic.
Mitigation Steps:
- Implement endpoint-level access controls and authorization checks.
- Use secure tokens for request validation.
- Add logging and monitoring for anomalous download patterns.

By addressing these issues, organizations can significantly reduce the risk of unauthorized access and protect sensitive data from potential exploitation.
Want to read more Bug Case Studies? Click here.






Проститутки Тюмени
Для снятия алкогольной интоксикации врач проводит детоксикационную терапию, которая включает внутривенные инфузии с растворами для выведения токсинов, поддерживающие препараты для печени, сердечно-сосудистой системы и нервной системы. В некоторых случаях назначаются седативные средства, нормализующие эмоциональное состояние пациента.
Углубиться в тему – [url=https://narcolog-na-dom-v-irkutske00.ru/]вызов нарколога на дом иркутск[/url]
¡Saludos, exploradores de oportunidades !
Casinos sin licencia espaГ±ola sin necesidad de ID – http://casinossinlicenciaenespana.es/ casino online sin licencia espaГ±a
¡Que vivas recompensas únicas !
недорогой интернет санкт-петербург
inernetvkvartiru-spb003.ru
узнать провайдера по адресу санкт-петербург
Основные показания для вызова нарколога:
Ознакомиться с деталями – https://narcolog-na-dom-v-irkutske00.ru/vyzov-narkologa-na-dom-irkutsk/
После прибытия врач проводит осмотр пациента, оценивает его состояние, измеряет давление, пульс, уровень кислорода и выявляет возможные противопоказания. Затем разрабатывается индивидуальный план лечения, направленный на стабилизацию состояния.
Изучить вопрос глубже – http://
отслеживание блокчейн
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Подробнее – http://angarsk-goradm.ru/info/prodazha-prav-arendy
Основные показания для вызова нарколога:
Подробнее тут – [url=https://narcolog-na-dom-v-irkutske00.ru/]нарколог на дом в иркутске[/url]
Городской портал Черкассы https://u-misti.cherkasy.ua новости, обзоры, события Черкасс и области
Как подчёркивает врач-нарколог клиники «Крылья Надежды» Андрей Кузьмин: «Своевременное обращение к специалистам гарантирует не только быстрое восстановление, но и предупреждает развитие тяжёлых осложнений, которые могут навсегда изменить жизнь пациента».
Выяснить больше – https://vyvod-iz-zapoya-korolev2.ru/
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Изучить вопрос глубже – https://www.suarasumselnews.co.id/2018/02/19/ini-dia-hubungan-partai-garuda-dengan-gerindra
Клиника «АнтиАлко» предлагает экстренную медицинскую помощь на дому в Новосибирске и Новосибирской области для тех, кто столкнулся с запоем. Если вы или ваш близкий оказались в состоянии длительной алкогольной интоксикации, наши специалисты готовы оперативно приехать к вам, провести комплексную детоксикацию и купировать симптомы абстинентного синдрома. Мы гарантируем высокий уровень безопасности, полную анонимность и индивидуальный подход к каждому пациенту.
Изучить вопрос глубже – [url=https://vyvod-iz-zapoya-novosibirsk00.ru/]вывод из запоя цена новосибирск[/url]
банкротство физлиц [url=www.bankrotstvo-grajdan.ru/]www.bankrotstvo-grajdan.ru/[/url] .
“Sst bahisseverler!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > …”
интернет по адресу дома
inernetvkvartiru-ufa001.ru
провайдер по адресу
Avoid health risks and AC breakdowns with scheduled duct cleaning in Dubai: how much does it cost to clean ac vents
Перед началом процедуры врач проводит осмотр, измеряет давление, пульс, уровень кислорода в крови, оценивает степень интоксикации и наличие сопутствующих заболеваний. После этого подбирается состав капельницы. В большинстве случаев она включает:
Подробнее тут – [url=https://kapelnica-ot-zapoya-moskva2.ru/]капельница от запоя[/url]
¡Hola, usuarios de sitios de juego !
Casinossinlicenciaespana.es – Lo Гєltimo en juegos – https://casinossinlicenciaespana.es/# casinos sin licencia en EspaГ±ola
¡Que experimentes giros memorables !
Эта разъяснительная статья содержит простые и доступные разъяснения по актуальным вопросам. Мы стремимся сделать информацию понятной для широкой аудитории, чтобы каждый смог разобраться в предмете и извлечь из него максимум пользы.
Изучить вопрос глубже – https://www.gtrust.co.za/hello-world
AC ducts in Dubai can accumulate sand and dust — regular cleaning is essential for your health https://ac-cleaning-dubai.ae/
После поступления вызова наш нарколог выезжает к пациенту в кратчайшие сроки, прибывая по адресу в пределах 30–60 минут. Специалист начинает процедуру с подробного осмотра и диагностики, измеряя ключевые показатели организма: артериальное давление, частоту пульса, насыщенность кислородом и собирая подробный анамнез.
Исследовать вопрос подробнее – [url=https://narcolog-na-dom-novosibirsk00.ru/]вызов нарколога на дом новосибирская область[/url]
Проблемы с алкоголем или наркотиками могут застать врасплох и привести к серьезным последствиям для организма, психического состояния и жизни пациента. Самостоятельные попытки выйти из запоя или преодолеть абстинентный синдром без медицинской поддержки редко оказываются эффективными и могут представлять реальную опасность для здоровья. Именно в таких ситуациях клиника «АльфаНаркология» предлагает услугу вызова нарколога на дом в Санкт-Петербурге и Ленинградской области. Наши специалисты оперативно реагируют на обращение, оказывают квалифицированную помощь и обеспечивают полную конфиденциальность лечения.
Исследовать вопрос подробнее – [url=https://narcolog-na-dom-sankt-peterburg000.ru/]вызов нарколога на дом санкт-петербург[/url]
Вся процедура проходит под полным контролем врача и занимает от 40 минут до 2 часов. Пациенту и его родственникам даются рекомендации по дальнейшему лечению и профилактике повторных запоев.
Получить больше информации – http://kapelnica-ot-zapoya-moskva00.ru/
¡Saludos, exploradores de la suerte !
Casino online extranjero sin restricciones de depГіsito – https://casinosextranjerosenespana.es/# п»їcasinos online extranjeros
¡Que vivas increíbles instantes inolvidables !
какие провайдеры по адресу
inernetvkvartiru-krasnodar003.ru
узнать провайдера по адресу краснодар
Портал города Черновцы https://u-misti.chernivtsi.ua последние новости, события, обзоры
узнать интернет по адресу
inernetvkvartiru-ufa002.ru
провайдеры интернета в уфе по адресу проверить
После поступления вызова нарколог клиники «АльфаНаркология» оперативно выезжает по указанному адресу. На месте врач проводит первичную диагностику, оценивая степень интоксикации, физическое и психологическое состояние пациента. По результатам осмотра врач подбирает индивидуальный комплекс лечебных процедур, в который входит постановка капельницы с растворами для детоксикации, препараты для стабилизации работы органов и нормализации психического состояния.
Получить больше информации – http://narcolog-na-dom-sankt-peterburg000.ru/
Запой — одно из самых опасных проявлений алкогольной зависимости. Он сопровождается глубокой интоксикацией организма, нарушением работы сердца, печени, головного мозга и других жизненно важных систем. Когда человек не может остановиться самостоятельно, а организм больше не справляется с нагрузкой, требуется медицинская помощь. В наркологической клинике «Спасение» в Мытищах мы проводим экстренные процедуры инфузионной терапии, позволяющие эффективно и безопасно вывести пациента из состояния запоя. Капельница — это первый шаг на пути к восстановлению здоровья и возвращению к нормальной жизни.
Получить дополнительную информацию – https://kapelnica-ot-zapoya-moskva2.ru/kapelnicy-ot-zapoya-na-domu-v-mytishchah
После прибытия врач проводит осмотр пациента, оценивает его состояние, измеряет давление, пульс, уровень кислорода и выявляет возможные противопоказания. Затем разрабатывается индивидуальный план лечения, направленный на стабилизацию состояния.
Получить дополнительные сведения – [url=https://narcolog-na-dom-v-irkutske00.ru/]вызов нарколога на дом в иркутске[/url]
¡Saludos, apostadores apasionados !
Casinosextranjerosenespana.es – ВЎBonos que valen la pena! – https://casinosextranjerosenespana.es/# casino online extranjero
¡Que vivas increíbles victorias épicas !
Мы понимаем, что в момент кризиса важна не только медицинская помощь, но и финансовая доступность. Поэтому в клинике «Спасение» в Мытищах действует несколько тарифов, позволяющих выбрать оптимальный вариант для любой ситуации. Стоимость зависит от состава препаратов, времени проведения и необходимости дополнительных манипуляций.
Исследовать вопрос подробнее – http://
Вызывать нарколога на дом рекомендуется при следующих состояниях:
Получить больше информации – [url=https://narcolog-na-dom-sankt-peterburg000.ru/]нарколог на дом цена в санкт-петербурге[/url]
нарколог на домв нижнем новгороде вызвать врача нарколога
закодироваться от алкоголя в нижнем закодироваться от алкоголя
Вся процедура проходит под полным контролем врача и занимает от 40 минут до 2 часов. Пациенту и его родственникам даются рекомендации по дальнейшему лечению и профилактике повторных запоев.
Подробнее тут – [url=https://kapelnica-ot-zapoya-moskva00.ru/]капельница от запоя наркология в москве[/url]
лечение алкоголизма в нижнем https://alko-info.ru
выведение из запоя дома вывод из запоя нижегородский
Вызов нарколога на дом в Иркутске и Иркутской области — это удобное и безопасное решение, позволяющее получить неотложную помощь в привычной обстановке. Врачи клиники «ЧистоЖизнь» выезжают круглосуточно, приезжают в течение 30–60 минут и проводят комплексное лечение, направленное на стабилизацию состояния пациента и предотвращение осложнений.
Углубиться в тему – https://narcolog-na-dom-v-irkutske00.ru/vrach-narkolog-na-dom-irkutsk/
Вся процедура проходит под полным контролем врача и занимает от 40 минут до 2 часов. Пациенту и его родственникам даются рекомендации по дальнейшему лечению и профилактике повторных запоев.
Изучить вопрос глубже – [url=https://kapelnica-ot-zapoya-moskva00.ru/]капельница от запоя цена в москве[/url]
Перед началом процедуры врач проводит осмотр, измеряет давление, пульс, уровень кислорода в крови, оценивает степень интоксикации и наличие сопутствующих заболеваний. После этого подбирается состав капельницы. В большинстве случаев она включает:
Исследовать вопрос подробнее – [url=https://kapelnica-ot-zapoya-moskva2.ru/]поставить капельницу от запоя[/url]
Вызов нарколога на дом в Иркутске и Иркутской области — это удобное и безопасное решение, позволяющее получить неотложную помощь в привычной обстановке. Врачи клиники «ЧистоЖизнь» выезжают круглосуточно, приезжают в течение 30–60 минут и проводят комплексное лечение, направленное на стабилизацию состояния пациента и предотвращение осложнений.
Подробнее тут – [url=https://narcolog-na-dom-v-irkutske00.ru/]вызов нарколога цена в иркутске[/url]
проверить интернет по адресу
inernetvkvartiru-ufa003.ru
провайдеры по адресу уфа
Вызывать нарколога на дом рекомендуется при следующих состояниях:
Получить больше информации – [url=https://narcolog-na-dom-sankt-peterburg000.ru/]нарколог на дом круглосуточно в санкт-петербурге[/url]
Защитите свои права! Воспользуйтесь бесплатной юридической консультацией. Опытные юристы помогут разобраться в сложных правовых вопросах по телефону. Первый шаг к решению вашей проблемы – бесплатная юридическая консультация по телефону круглосуточно
Новинний сайт Житомира https://faine-misto.zt.ua новости Житомира сегодня
Пациенты выбирают нашу клинику для срочного вызова врача-нарколога благодаря следующим важным преимуществам:
Исследовать вопрос подробнее – http://narcolog-na-dom-novosibirsk00.ru
Врачи клиники «ЗдравЦентр» рекомендуют не откладывать вызов нарколога, чтобы избежать серьезных последствий, таких как судорожные припадки, инсульт или алкогольный психоз.
Выяснить больше – [url=https://kapelnica-ot-zapoya-moskva00.ru/]postavit-kapelniczu-ot-zapoya moskva[/url]
Праздничная продукция https://prazdnik-x.ru для любого повода: шары, гирлянды, декор, упаковка, сувениры. Всё для дня рождения, свадьбы, выпускного и корпоративов.
оценка компании оценка активов предприятия
лечение наркомании клиника https://narco-info.ru
Всё для строительства https://d20.com.ua и ремонта: инструкции, обзоры, экспертизы, калькуляторы. Профессиональные советы, новинки рынка, база строительных компаний.
casino enjoy antofagasta
интернет провайдер омск
inernetvkvartiru-volgograd001.ru
провайдеры омск
Клиника предлагает индивидуальный подход к каждому пациенту. Лечение начинается с детальной диагностики состояния здоровья, что позволяет врачу подобрать наиболее эффективную схему терапии.
Подробнее тут – [url=https://vyvod-iz-zapoya-korolev2.ru/]vyvod iz zapoya na domu kruglosutochno[/url]
пластиковые окна rehau [url=http://okna177.ru]пластиковые окна rehau[/url] .
“Merhaba forum ahalisi!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://jojobetorijinal.com/]jojobetorijinal.com[/url]”
Строительный журнал https://garant-jitlo.com.ua всё о технологиях, материалах, архитектуре, ремонте и дизайне. Интервью с экспертами, кейсы, тренды рынка.
Онлайн-журнал https://inox.com.ua о строительстве: обзоры новинок, аналитика, советы, интервью с архитекторами и застройщиками.
Современный строительный https://interiordesign.kyiv.ua журнал: идеи, решения, технологии, тенденции. Всё о ремонте, стройке, дизайне и инженерных системах.
Лечение проводится в комфортных домашних условиях, что снижает стресс и помогает быстрее восстановиться.
Выяснить больше – https://vyvod-iz-zapoya-novosibirsk00.ru/vyvod-iz-zapoya-czena-novosibirsk
Основные показания для вызова нарколога:
Детальнее – https://narcolog-na-dom-v-irkutske00.ru/narkolog-na-dom-czena-irkutsk/
Информационный журнал https://newhouse.kyiv.ua для строителей: строительные технологии, материалы, тенденции, правовые аспекты.
Как отмечает нарколог Олег Васильев, «чем раньше пациент получает квалифицированную медицинскую помощь, тем меньше риск серьезных осложнений».
Получить дополнительную информацию – http://
Некоторые состояния требуют немедленного вмешательства специалиста. Если алкогольное отравление или запойное состояние не купируется вовремя, это может привести к тяжелым последствиям для здоровья.
Подробнее – [url=https://narcolog-na-dom-v-irkutske00.ru/]нарколог на дом цены иркутск[/url]
провайдеры по адресу краснодар
inernetvkvartiru-krasnodar003.ru
интернет по адресу
После поступления вызова наш нарколог выезжает к пациенту в кратчайшие сроки, прибывая по адресу в пределах 30–60 минут. Специалист начинает процедуру с подробного осмотра и диагностики, измеряя ключевые показатели организма: артериальное давление, частоту пульса, насыщенность кислородом и собирая подробный анамнез.
Подробнее тут – https://narcolog-na-dom-novosibirsk00.ru/narkolog-na-dom-kruglosutochno-novosibirsk/
Защитите свои права! Воспользуйтесь бесплатной юридической консультацией. Опытные юристы помогут разобраться в сложных правовых вопросах по телефону. Первый шаг к решению вашей проблемы: бесплатная консультация юриста по телефону круглосуточно
провайдеры домашнего интернета омск
inernetvkvartiru-volgograd002.ru
домашний интернет тарифы омск
Основные показания для вызова нарколога:
Получить дополнительные сведения – https://narcolog-na-dom-v-irkutske00.ru/vyzov-narkologa-na-dom-irkutsk
Проблемы с алкоголем или наркотиками могут застать врасплох и привести к серьезным последствиям для организма, психического состояния и жизни пациента. Самостоятельные попытки выйти из запоя или преодолеть абстинентный синдром без медицинской поддержки редко оказываются эффективными и могут представлять реальную опасность для здоровья. Именно в таких ситуациях клиника «АльфаНаркология» предлагает услугу вызова нарколога на дом в Санкт-Петербурге и Ленинградской области. Наши специалисты оперативно реагируют на обращение, оказывают квалифицированную помощь и обеспечивают полную конфиденциальность лечения.
Подробнее тут – [url=https://narcolog-na-dom-sankt-peterburg000.ru/]vyzov-narkologa-na-dom sankt-peterburg[/url]
Проблемы с алкоголем или наркотиками могут застать врасплох и привести к серьезным последствиям для организма, психического состояния и жизни пациента. Самостоятельные попытки выйти из запоя или преодолеть абстинентный синдром без медицинской поддержки редко оказываются эффективными и могут представлять реальную опасность для здоровья. Именно в таких ситуациях клиника «АльфаНаркология» предлагает услугу вызова нарколога на дом в Санкт-Петербурге и Ленинградской области. Наши специалисты оперативно реагируют на обращение, оказывают квалифицированную помощь и обеспечивают полную конфиденциальность лечения.
Получить больше информации – [url=https://narcolog-na-dom-sankt-peterburg000.ru/]нарколог на дом цена[/url]
Как отмечает нарколог Олег Васильев, «чем раньше пациент получает квалифицированную медицинскую помощь, тем меньше риск серьезных осложнений».
Ознакомиться с деталями – [url=https://narcolog-na-dom-v-irkutske00.ru/]нарколог на дом в иркутске[/url]
провайдеры интернета в краснодаре по адресу
inernetvkvartiru-krasnodar003.ru
провайдеры интернета в краснодаре по адресу проверить
Основные показания для вызова нарколога:
Подробнее можно узнать тут – http://narcolog-na-dom-v-irkutske00.ru/vrach-narkolog-na-dom-irkutsk/
подключить интернет тарифы омск
inernetvkvartiru-volgograd003.ru
тарифы интернет и телевидение омск
В этой публикации мы сосредоточимся на интересных аспектах одной из самых актуальных тем современности. Совмещая факты и мнения экспертов, мы создадим полное представление о предмете, которое будет полезно как новичкам, так и тем, кто глубоко изучает вопрос.
Ознакомиться с деталями – https://www.cempi2.it/start-romagna
В обзорной статье вы найдете собрание важных фактов и аналитики по самым разнообразным темам. Мы рассматриваем как современные исследования, так и исторические контексты, чтобы вы могли получить полное представление о предмете. Погрузитесь в мир знаний и сделайте шаг к пониманию!
Получить дополнительные сведения – https://coaatburgos.es/2013/10/23/xvi-jornadas-tecnicas-de-construccion-rehabilitacion-energetica-en-la-edificacion
В клинике «Воздух Свободы» процедура вывода из запоя в Люберцах начинается с комплексной диагностики. Врач проводит первичный осмотр, измеряет жизненные показатели и подбирает препараты, которые быстро снимают симптомы интоксикации. В зависимости от состояния пациента, лечение может проходить дома или в стационаре клиники.
Подробнее – https://vyvod-iz-zapoya-lyubertsy2.ru/vyvod-iz-zapoya-anonimno
Сирийский врач, пытавший людей, приговорен к пожизненному заключению немецким судом
https://x.com/kiselev_igr/status/1934861946425131280
Dusty AC ducts can impact your energy bill — our Dubai cleaning services help you save https://ac-cleaning-dubai.ae/
Наркологическая клиника «МедЛайн» предоставляет профессиональные услуги врача-нарколога с выездом на дом в Новосибирске и Новосибирской области. Мы оперативно помогаем пациентам справиться с тяжелыми состояниями при алкогольной и наркотической зависимости. Экстренный выезд наших специалистов доступен круглосуточно, а лечение проводится с применением проверенных методик и препаратов, что гарантирует безопасность и конфиденциальность каждому пациенту.
Изучить вопрос глубже – https://narcolog-na-dom-novosibirsk00.ru/narkolog-na-dom-czena-novosibirsk/
Этот информативный текст выделяется своими захватывающими аспектами, которые делают сложные темы доступными и понятными. Мы стремимся предложить читателям глубину знаний вместе с разнообразием интересных фактов. Откройте новые горизонты и развивайте свои способности познавать мир!
Изучить вопрос глубже – https://bgcompanyinc.com/2024/07/28/hello-world
домашний интернет воронеж
inernetvkvartiru-voronezh001.ru
подключить проводной интернет воронеж
https://www.worldwomen2016.com/
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Узнать больше – https://www.casabalamcancun.com/relax-zone
Пациенты выбирают нашу клинику для срочного вызова врача-нарколога благодаря следующим важным преимуществам:
Получить дополнительные сведения – http://
Строительный журнал https://poradnik.com.ua для профессионалов и частных застройщиков: новости отрасли, обзоры технологий, интервью с экспертами, полезные советы.
Всё о строительстве https://stroyportal.kyiv.ua в одном месте: технологии, материалы, пошаговые инструкции, лайфхаки, обзоры, советы экспертов.
Журнал о строительстве https://sovetik.in.ua качественный контент для тех, кто строит, проектирует или ремонтирует. Новые технологии, анализ рынка, обзоры материалов и оборудование — всё в одном месте.
Полезный сайт https://vasha-opora.com.ua для тех, кто строит: от фундамента до крыши. Советы, инструкции, сравнение материалов, идеи для ремонта и дизайна.
Regular AC duct cleaning in Dubai keeps your system running smoothly and your air fresh https://ac-cleaning-dubai.ae/
Этот информативный текст выделяется своими захватывающими аспектами, которые делают сложные темы доступными и понятными. Мы стремимся предложить читателям глубину знаний вместе с разнообразием интересных фактов. Откройте новые горизонты и развивайте свои способности познавать мир!
Исследовать вопрос подробнее – https://press.et/arabic/?p=4984
Предлагаем вашему вниманию интересную справочную статью, в которой собраны ключевые моменты и нюансы по актуальным вопросам. Эта информация будет полезна как для профессионалов, так и для тех, кто только начинает изучать тему. Узнайте ответы на важные вопросы и расширьте свои знания!
Изучить вопрос глубже – https://soundboardguy.com/sounds/where-did-you-go
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Подробнее можно узнать тут – https://bvi50plus.com/buchtipp-das-kann-gut-werden-dtalk-mit-autorin-bettina-musall
В этом обзорном материале представлены увлекательные детали, которые находят отражение в различных аспектах жизни. Мы исследуем непонятные и интересные моменты, позволяя читателю увидеть картину целиком. Погрузитесь в мир знаний и удивительных открытий!
Изучить вопрос глубже – https://siritaikoto.com/2024/02/18/royal-mutch
Когда следует немедленно обращаться за помощью:
Узнать больше – https://narcolog-na-dom-novokuznetsk0.ru/narkolog-na-dom-czena-novokuzneczk
интернет провайдер воронеж
inernetvkvartiru-voronezh002.ru
домашний интернет тарифы
Алкогольная и наркотическая зависимость требуют незамедлительного и комплексного вмешательства для предотвращения серьезных осложнений и сохранения здоровья пациента. В Уфе, Республика Башкортостан, опытные наркологи выезжают на дом 24 часа в сутки, предоставляя оперативную помощь при запоях и в случаях наркотической интоксикации. Такой формат лечения позволяет начать детоксикацию в комфортной, привычной обстановке, обеспечивая максимальную конфиденциальность и индивидуальный подход к каждому пациенту.
Подробнее – https://narcolog-na-dom-ufa000.ru/narkolog-na-dom-czena-ufa/
В нашей клинике применяются различные техники кодирования, которые подбираются с учётом медицинских показаний, психологического состояния и пожеланий пациента.
Углубиться в тему – https://kodirovanie-ot-alkogolizma-odintsovo2.ru/kodirovanie-ot-alkogolizma-na-domu
Новости Полтава https://u-misti.poltava.ua городской портал, последние события Полтавы и области
“Hey bahisseverler!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://marsbahisgiris2025.org/]marsbahisgiris2025.org[/url]”
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Получить дополнительные сведения – https://churchofhope.com/golfclassic
Процедура начинается с врачебного осмотра. Специалист оценивает общее состояние, артериальное давление, пульс, сатурацию, уровень обезвоживания, жалобы пациента. При необходимости проводятся экспресс-анализы. Далее индивидуально подбирается состав инфузионной терапии. В большинстве случаев капельница включает:
Получить дополнительные сведения – [url=https://kapelnica-ot-zapoya-moskva3.ru/]капельницы от запоя на дому[/url]
Предлагаем вашему вниманию интересную справочную статью, в которой собраны ключевые моменты и нюансы по актуальным вопросам. Эта информация будет полезна как для профессионалов, так и для тех, кто только начинает изучать тему. Узнайте ответы на важные вопросы и расширьте свои знания!
Узнать больше – https://consultoresyadministradores.com.gt/business-school-objectives
Пиратские сокровища – 5 крупнейших кладов в истории
https://x.com/kiselev_igr/status/1934952832429330693
Откройте для себя свежие идеи о стиле, здоровье и красоте на сайте https://jornalwomen.ru/. Полезные советы, актуальные новости, вдохновение и рекомендации для современных женщин – заходите ежедневно за новым контентом!
Кулинарный портал https://vagon-restoran.kiev.ua с тысячами проверенных рецептов на каждый день и для особых случаев. Пошаговые инструкции, фото, видео, советы шефов.
Мужской журнал https://hand-spin.com.ua о стиле, спорте, отношениях, здоровье, технике и бизнесе. Актуальные статьи, советы экспертов, обзоры и мужской взгляд на важные темы.
Журнал для мужчин https://swiss-watches.com.ua которые ценят успех, свободу и стиль. Практичные советы, мотивация, интервью, спорт, отношения, технологии.
Когда запой превращается в угрозу для жизни, оперативное вмешательство становится критически важным. В Тюмени, Тюменская область, опытные наркологи предлагают услугу установки капельницы от запоя прямо на дому. Такой метод позволяет начать детоксикацию с использованием современных медикаментов, что способствует быстрому выведению токсинов, восстановлению обменных процессов и нормализации работы внутренних органов. Лечение на дому обеспечивает комфортную обстановку, полную конфиденциальность и индивидуальный подход к каждому пациенту.
Изучить вопрос глубже – http://kapelnica-ot-zapoya-tyumen00.ru
Читайте мужской https://zlochinec.kyiv.ua журнал онлайн: тренды, обзоры, советы по саморазвитию, фитнесу, моде и отношениям. Всё о том, как быть уверенным, успешным и сильным — каждый день.
Одновременно с медикаментозной детоксикацией начинается работа по снижению эмоционального напряжения. Психотерапевтическая помощь помогает пациенту осознать причины зависимости и выработать стратегии для предотвращения рецидивов, что является важным аспектом успешного лечения.
Углубиться в тему – [url=https://vyvod-iz-zapoya-volgograd00.ru/]наркология вывод из запоя в волгограде[/url]
Сомневаетесь в своих правах? Наша бесплатная консультация юристов по телефону поможет вам. Разъясним сложные моменты законодательства и подскажем, как действовать дальше – телефон юриста
подключить интернет воронеж
inernetvkvartiru-voronezh003.ru
провайдеры домашнего интернета воронеж
Клиника «НаркоЩит» предоставляет возможность безопасного вывода из запоя на дому в Нижнем Новгороде и Нижегородской области с помощью установки капельницы. Наши опытные специалисты оперативно приезжают для проведения детоксикации, снятия симптомов алкогольной интоксикации и стабилизации состояния пациента. Мы гарантируем круглосуточный выезд, соблюдение конфиденциальности и высокий уровень профессионального обслуживания.
Изучить вопрос глубже – http://kapelnica-ot-zapoya-nizhniy-novgorod00.ru
В этих случаях вызов нарколога на дом не только оправдан, но и жизненно необходим для предотвращения опасных осложнений и стабилизации здоровья пациента.
Узнать больше – [url=https://narcolog-na-dom-voronezh00.ru/]выезд нарколога на дом воронеж[/url]
Процедура вывода из запоя начинается с тщательной диагностики состояния пациента, чтобы определить, какие методы лечения будут наиболее эффективными. Мы применяем индивидуальный подход и комбинируем медикаментозное лечение с психотерапевтической поддержкой, что даёт лучший результат.
Ознакомиться с деталями – http://
Запой сопровождается быстрым накоплением токсинов, что может привести к нарушению работы сердца, печени и почек. Использование капельничного метода позволяет оперативно ввести современные препараты для детоксикации, что способствует быстрому восстановлению обменных процессов и нормализации работы внутренних органов. Оперативное лечение на дому особенно актуально, когда каждая минута имеет значение для спасения здоровья.
Разобраться лучше – https://kapelnica-ot-zapoya-tyumen0.ru/kapelnicza-ot-zapoya-na-domu-tyumen
Оперативное лечение организовано по четкому алгоритму, который позволяет быстро стабилизировать состояние пациента и обеспечить эффективную терапию. Каждый этап направлен на комплексное восстановление организма.
Подробнее тут – https://vyvod-iz-zapoya-volgograd000.ru/vyvod-iz-zapoya-na-domu-volgograd/
Алкогольная и наркотическая зависимость требуют незамедлительного и комплексного вмешательства для предотвращения серьезных осложнений и сохранения здоровья пациента. В Уфе, Республика Башкортостан, опытные наркологи выезжают на дом 24 часа в сутки, предоставляя оперативную помощь при запоях и в случаях наркотической интоксикации. Такой формат лечения позволяет начать детоксикацию в комфортной, привычной обстановке, обеспечивая максимальную конфиденциальность и индивидуальный подход к каждому пациенту.
Подробнее можно узнать тут – http://narcolog-na-dom-ufa000.ru
Срочное вмешательство врача необходимо при появлении следующих симптомов:
Узнать больше – http://
ИнфоКиев https://infosite.kyiv.ua события, новости обзоры в Киеве и области.
Процесс вывода из запоя капельничным методом организован по строгой схеме, позволяющей обеспечить максимальную эффективность терапии. Каждая стадия направлена на комплексное восстановление организма и минимизацию риска осложнений.
Изучить вопрос глубже – http://kapelnica-ot-zapoya-tyumen0.ru
Когда запой превращается в угрозу для жизни, оперативное вмешательство становится критически важным. В Тюмени, Тюменская область, опытные наркологи предлагают услугу установки капельницы от запоя прямо на дому. Такой метод позволяет начать детоксикацию с использованием современных медикаментов, что способствует быстрому выведению токсинов, восстановлению обменных процессов и нормализации работы внутренних органов. Лечение на дому обеспечивает комфортную обстановку, полную конфиденциальность и индивидуальный подход к каждому пациенту.
Разобраться лучше – https://kapelnica-ot-zapoya-tyumen00.ru/postavit-kapelniczu-ot-zapoya-tyumen/
Первичный этап терапии направлен на оперативное выведение токсинов из организма. Врач-нарколог назначает индивидуальную схему медикаментозного вмешательства, что позволяет снизить уровень алкоголя в крови и восстановить обмен веществ.
Подробнее тут – [url=https://vyvod-iz-zapoya-volgograd00.ru/]вывод из запоя в стационаре[/url]
https://blstone.ru/
Запой сопровождается быстрым накоплением токсинов, что может привести к нарушению работы сердца, печени и почек. Использование капельничного метода позволяет оперативно ввести современные препараты для детоксикации, что способствует быстрому восстановлению обменных процессов и нормализации работы внутренних органов. Оперативное лечение на дому особенно актуально, когда каждая минута имеет значение для спасения здоровья.
Узнать больше – http://kapelnica-ot-zapoya-tyumen0.ru
провайдеры по адресу
inernetvkvartiru-krasnodar003.ru
узнать провайдера по адресу краснодар
Лечение на дому основывается на комплексном подходе, который включает медикаментозную детоксикацию и психологическую поддержку. Каждая терапевтическая процедура подбирается индивидуально с учетом клинической картины пациента, что позволяет добиться максимальной эффективности и безопасности лечения.
Ознакомиться с деталями – [url=https://vyvod-iz-zapoya-volgograd00.ru/]vyvod-iz-zapoya-na-domu volgograd[/url]
Наши специалисты используют проверенные и сертифицированные медикаменты, которые подбираются индивидуально для каждого пациента:
Детальнее – https://kapelnica-ot-zapoya-nizhniy-novgorod00.ru/kapelnicza-ot-zapoya-czena-nizhnij-novgorod/
Оперативное лечение организовано по четкому алгоритму, который позволяет быстро стабилизировать состояние пациента и обеспечить эффективную терапию. Каждый этап направлен на комплексное восстановление организма.
Углубиться в тему – [url=https://vyvod-iz-zapoya-volgograd000.ru/]вывод из запоя[/url]
Запой может быть не только физически тяжёлым, но и психологически разрушительным. Поэтому важно вовремя обратиться за помощью. Вывод из запоя в Нижнем Новгороде — это необходимая медицинская процедура, которая помогает победить алкогольную зависимость и восстановить здоровье. Мы в клинике «АнтиЗависимость» предлагаем круглосуточную помощь в комфортных условиях — на дому или в стационаре.
Получить дополнительные сведения – [url=https://narcolog-na-dom-novokuznetsk0.ru/]вызов врача нарколога на дом новокузнецк[/url]
Срочное вмешательство врача необходимо при появлении следующих симптомов:
Подробнее можно узнать тут – [url=https://vyvod-iz-zapoya-korolev2.ru/]vyvod iz zapoya na domu[/url]
Процесс вывода из запоя капельничным методом организован по строгой схеме, позволяющей обеспечить максимальную эффективность терапии. Каждая стадия направлена на комплексное восстановление организма и минимизацию риска осложнений.
Получить дополнительную информацию – https://kapelnica-ot-zapoya-tyumen0.ru/kapelnicza-ot-zapoya-na-domu-tyumen
Обращаясь за помощью в клинику «НаркоЩит», пациенты получают комплексное лечение, которое отличается следующими преимуществами:
Углубиться в тему – https://kapelnica-ot-zapoya-nizhniy-novgorod00.ru/vyzvat-kapelniczu-ot-zapoya-nizhnij-novgorod/
При поступлении вызова нарколог незамедлительно приезжает на дом для проведения тщательного осмотра. На этом этапе специалист измеряет жизненно важные показатели, собирает подробный анамнез и определяет степень интоксикации. Эти данные являются ключевыми для составления индивидуального плана лечения.
Получить больше информации – [url=https://kapelnica-ot-zapoya-tyumen00.ru/]капельницу от запоя в тюмени[/url]
Лечение зависимости требует не только физической детоксикации, но и работы с психоэмоциональным состоянием пациента. Психотерапевтическая поддержка помогает выявить глубинные причины зависимости, снизить уровень стресса и сформировать устойчивые навыки самоконтроля, что существенно снижает риск рецидивов.
Подробнее тут – [url=https://narcolog-na-dom-ufa000.ru/]частный нарколог на дом в уфе[/url]
Монтаж систем видеонаблюдения позволит безопасность территории в режиме 24/7.
Современные технологии гарантируют надежный обзор даже в ночных условиях.
Мы предлагаем широкий выбор устройств, идеальных для дома.
videonablyudeniemoskva.ru
Профессиональная установка и сервисное обслуживание делают процесс максимально удобным для любых задач.
Обратитесь сегодня, чтобы получить персональную консультацию в сфере безопасности.
Незамедлительно после вызова нарколог прибывает на место для проведения первичной диагностики. На этом этапе осуществляется сбор анамнеза, измерение жизненно важных показателей и оценка степени интоксикации, что является основой для составления индивидуального плана лечения.
Получить дополнительную информацию – http://vyvod-iz-zapoya-volgograd000.ru/vyvod-iz-zapoya-na-domu-volgograd/
Лечение на дому основывается на комплексном подходе, который включает медикаментозную детоксикацию и психологическую поддержку. Каждая терапевтическая процедура подбирается индивидуально с учетом клинической картины пациента, что позволяет добиться максимальной эффективности и безопасности лечения.
Исследовать вопрос подробнее – https://vyvod-iz-zapoya-volgograd00.ru/
Как подчёркивает врач-нарколог клиники «Крылья Надежды» Андрей Кузьмин: «Своевременное обращение к специалистам гарантирует не только быстрое восстановление, но и предупреждает развитие тяжёлых осложнений, которые могут навсегда изменить жизнь пациента».
Углубиться в тему – https://vyvod-iz-zapoya-korolev2.ru/vyvod-iz-zapoya-kruglosutochno/
Все новинки https://helikon.com.ua технологий в одном месте: гаджеты, AI, робототехника, электромобили, мобильные устройства, инновации в науке и IT.
Портал о ремонте https://as-el.com.ua и строительстве: от черновых работ до отделки. Статьи, обзоры, идеи, лайфхаки.
Ремонт без стресса https://odessajs.org.ua вместе с нами! Полезные статьи, лайфхаки, дизайн-проекты, калькуляторы и обзоры.
Сайт о строительстве https://selma.com.ua практические советы, современные технологии, пошаговые инструкции, выбор материалов и обзоры техники.
¡Hola, seguidores de la emoción !
Casino online fuera de EspaГ±a sin comisiones ocultas – https://www.casinoonlinefueradeespanol.xyz/ casinos fuera de espaГ±a
¡Que disfrutes de asombrosas conquistas legendarias !
Наши специалисты используют проверенные и сертифицированные медикаменты, которые подбираются индивидуально для каждого пациента:
Подробнее тут – https://kapelnica-ot-zapoya-nizhniy-novgorod00.ru/kapelnicza-ot-zapoya-na-domu-nizhnij-novgorod/
При длительном запое в организме накапливаются вредные токсины, что ведёт к нарушениям работы сердца, печени, почек и других жизненно важных органов. Чем быстрее начинается терапия, тем выше шансы избежать серьёзных осложнений и обеспечить качественное восстановление. Метод капельничного лечения позволяет оперативно начать детоксикацию, что особенно важно для спасения жизни и предупреждения хронических последствий злоупотребления алкоголем.
Изучить вопрос глубже – http://kapelnica-ot-zapoya-tyumen00.ru
Запой может быть не только физически тяжёлым, но и психологически разрушительным. Поэтому важно вовремя обратиться за помощью. Вывод из запоя в Нижнем Новгороде — это необходимая медицинская процедура, которая помогает победить алкогольную зависимость и восстановить здоровье. Мы в клинике «АнтиЗависимость» предлагаем круглосуточную помощь в комфортных условиях — на дому или в стационаре.
Выяснить больше – [url=https://narcolog-na-dom-novokuznetsk0.ru/]нарколог на дом недорого в новокузнецке[/url]
При длительном запое в организме накапливаются вредные токсины, что ведёт к нарушениям работы сердца, печени, почек и других жизненно важных органов. Чем быстрее начинается терапия, тем выше шансы избежать серьёзных осложнений и обеспечить качественное восстановление. Метод капельничного лечения позволяет оперативно начать детоксикацию, что особенно важно для спасения жизни и предупреждения хронических последствий злоупотребления алкоголем.
Получить дополнительные сведения – [url=https://kapelnica-ot-zapoya-tyumen00.ru/]капельница от запоя на дому в тюмени[/url]
диплом техникума купить [url=https://arus-diplom6.ru/]https://arus-diplom6.ru/[/url] .
Комплексная терапия при выводе из запоя на дому включает в себя два основных направления: медикаментозную детоксикацию и психологическую поддержку. Такой подход позволяет добиться быстрого и устойчивого эффекта, минимизируя риск осложнений и обеспечивая долгосрочную ремиссию.
Выяснить больше – https://narcolog-na-dom-ufa000.ru/narkolog-na-dom-czena-ufa/
Запой может быть не только физически тяжёлым, но и психологически разрушительным. Поэтому важно вовремя обратиться за помощью. Вывод из запоя в Нижнем Новгороде — это необходимая медицинская процедура, которая помогает победить алкогольную зависимость и восстановить здоровье. Мы в клинике «АнтиЗависимость» предлагаем круглосуточную помощь в комфортных условиях — на дому или в стационаре.
Получить больше информации – [url=https://narcolog-na-dom-novokuznetsk0.ru/]нарколог на дом кемеровская область[/url]
Запой — это не просто несколько дней бесконтрольного употребления алкоголя. Это тяжёлое патологическое состояние, при котором организм человека накапливает токсические продукты распада этанола, теряет жизненно важные электролиты, обезвоживается и выходит из равновесия. На фоне этого нарушается работа сердца, мозга, печени и других систем. Чем дольше длится запой, тем тяжелее последствия и выше риск развития осложнений, вплоть до алкогольного психоза или инсульта. В такой ситуации незаменимым методом экстренной помощи становится капельница от запоя — процедура, позволяющая быстро и безопасно вывести токсины, стабилизировать жизненно важные функции и вернуть человеку контроль над собой.
Исследовать вопрос подробнее – [url=https://kapelnica-ot-zapoya-moskva3.ru/]врач на дом капельница от запоя[/url]
Автоматизированные системы дозирования обеспечивают точное введение лекарственных средств, что минимизирует риск передозировки и побочных эффектов. Постоянный мониторинг жизненных показателей позволяет оперативно корректировать терапию в режиме реального времени, обеспечивая максимальную безопасность процедуры.
Получить дополнительные сведения – [url=https://narcolog-na-dom-ufa000.ru/]вызов нарколога на дом цена уфа[/url]
Игорь Стоунберг экстрасенс Его дар – это дар свыше.
Запой — это тяжёлое состояние, характеризующееся длительным употреблением алкоголя, при котором человек не в силах самостоятельно прекратить пить. Алкогольная интоксикация при длительных запоях вызывает нарушения в работе всех органов и систем, приводя к серьёзным последствиям, таким как инфаркты, инсульты, психозы и даже летальный исход. В такой ситуации единственным надёжным решением становится обращение за профессиональной помощью.
Подробнее можно узнать тут – [url=https://vyvod-iz-zapoya-korolev2.ru/]vyvod iz zapoya korolev[/url]
Специалист уточняет продолжительность запоя, характер симптоматики и наличие хронических заболеваний, проводит измерения пульса, давления и температуры, что позволяет оперативно скорректировать терапию.
Получить дополнительную информацию – http://vyvod-iz-zapoya-volgograd000.ru/vyvod-iz-zapoya-na-domu-volgograd/
новости ICO криптовалют Топ токенов роста демонстрируют устойчивую динамику и потенциал для дальнейшего увеличения стоимости.
подключить интернет тарифы челябинск
inernetvkvartiru-chelyabinsk001.ru
недорогой интернет челябинск
Процесс вывода из запоя капельничным методом организован по строгой схеме, позволяющей обеспечить максимальную эффективность терапии. Каждая стадия направлена на комплексное восстановление организма и минимизацию риска осложнений.
Подробнее можно узнать тут – [url=https://kapelnica-ot-zapoya-tyumen0.ru/]kapelnica-ot-zapoya-tyumen0.ru/[/url]
деньги под птс автомобиля екатеринбург
24avtolombard-pts65.ru/ekb.html
займ под птс без посещения офиса
кредит под птс спецтехники
24avtolombard-pts65.ru/ekb.html
кредит под залог птс автомобиля
При длительном запое в организме накапливаются вредные токсины, что ведёт к нарушениям работы сердца, печени, почек и других жизненно важных органов. Чем быстрее начинается терапия, тем выше шансы избежать серьёзных осложнений и обеспечить качественное восстановление. Метод капельничного лечения позволяет оперативно начать детоксикацию, что особенно важно для спасения жизни и предупреждения хронических последствий злоупотребления алкоголем.
Детальнее – http://kapelnica-ot-zapoya-tyumen00.ru
Когда запой превращается в угрозу для жизни, оперативное вмешательство становится критически важным. В Тюмени, Тюменская область, опытные наркологи предлагают услугу установки капельницы от запоя прямо на дому. Такой метод позволяет начать детоксикацию с использованием современных медикаментов, что способствует быстрому выведению токсинов, восстановлению обменных процессов и нормализации работы внутренних органов. Лечение на дому обеспечивает комфортную обстановку, полную конфиденциальность и индивидуальный подход к каждому пациенту.
Исследовать вопрос подробнее – [url=https://kapelnica-ot-zapoya-tyumen00.ru/]капельницы от запоя в тюмени[/url]
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me. https://accounts.binance.com/sk/register?ref=OMM3XK51
Запой может быть не только физически тяжёлым, но и психологически разрушительным. Поэтому важно вовремя обратиться за помощью. Вывод из запоя в Нижнем Новгороде — это необходимая медицинская процедура, которая помогает победить алкогольную зависимость и восстановить здоровье. Мы в клинике «АнтиЗависимость» предлагаем круглосуточную помощь в комфортных условиях — на дому или в стационаре.
Углубиться в тему – https://narcolog-na-dom-novokuznetsk0.ru/narkolog-na-dom-klinika-novokuzneczk/
После первичной диагностики начинается активная фаза детоксикации. Современные препараты вводятся капельничным методом, что позволяет быстро вывести токсины и восстановить нормальные обменные процессы. Этот этап критически важен для стабилизации работы печени, почек и сердечно-сосудистой системы.
Выяснить больше – https://kapelnica-ot-zapoya-tyumen0.ru/kapelnicza-ot-zapoya-na-domu-tyumen/
Запой может быть не только физически тяжёлым, но и психологически разрушительным. Поэтому важно вовремя обратиться за помощью. Вывод из запоя в Нижнем Новгороде — это необходимая медицинская процедура, которая помогает победить алкогольную зависимость и восстановить здоровье. Мы в клинике «АнтиЗависимость» предлагаем круглосуточную помощь в комфортных условиях — на дому или в стационаре.
Узнать больше – http://narcolog-na-dom-novokuznetsk0.ru/narkolog-lechenie-na-domu-novokuzneczk/
Услуга “Нарколог на дом” в Уфе охватывает широкий спектр лечебных мероприятий, направленных как на устранение токсической нагрузки, так и на работу с психоэмоциональным состоянием пациента. Комплексная терапия включает в себя медикаментозную детоксикацию, корректировку обменных процессов, а также психотерапевтическую поддержку, что позволяет не только вывести пациента из состояния запоя, но и помочь ему справиться с наркотической зависимостью.
Разобраться лучше – [url=https://narcolog-na-dom-ufa000.ru/]нарколог на дом цены в уфе[/url]
Алкогольная и наркотическая зависимость требуют незамедлительного и комплексного вмешательства для предотвращения серьезных осложнений и сохранения здоровья пациента. В Уфе, Республика Башкортостан, опытные наркологи выезжают на дом 24 часа в сутки, предоставляя оперативную помощь при запоях и в случаях наркотической интоксикации. Такой формат лечения позволяет начать детоксикацию в комфортной, привычной обстановке, обеспечивая максимальную конфиденциальность и индивидуальный подход к каждому пациенту.
Углубиться в тему – https://narcolog-na-dom-ufa000.ru/narkolog-na-dom-czena-ufa
автоломбард в казани круглосуточно
24avtolombard-pts65.ru/kazan.html
взять кредит под залог автомобиля
займ птс
24avtolombard-pts65.ru/kazan.html
машина под залог
¡Hola, aventureros de la fortuna !
Casino por fuera con mГ©todos de pago locales – https://casinoonlinefueradeespanol.xyz/# п»їп»їcasino fuera de espaГ±a
¡Que disfrutes de asombrosas premios extraordinarios !
Городской портал Винницы https://u-misti.vinnica.ua новости, события и обзоры Винницы и области
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Подробнее тут – https://amarinstructor.com/ome-tv-alternatives
Раскрыта тайна предсмертных видений
https://x.com/kiselev_igr/status/1935229425135530469
Эта статья сочетает познавательный и занимательный контент, что делает ее идеальной для любителей глубоких исследований. Мы рассмотрим увлекательные аспекты различных тем и предоставим вам новые знания, которые могут оказаться полезными в будущем.
Разобраться лучше – https://triple-sconstructionidaho.com/hello-world
Эта статья для ознакомления предлагает читателям общее представление об актуальной теме. Мы стремимся представить ключевые факты и идеи, которые помогут читателям получить представление о предмете и решить, стоит ли углубляться в изучение.
Разобраться лучше – https://crjanitorialservices.ca/2021/06/office-cleaning-company-near-me
Этот информационный материал привлекает внимание множеством интересных деталей и необычных ракурсов. Мы предлагаем уникальные взгляды на привычные вещи и рассматриваем вопросы, которые волнуют общество. Будьте в курсе актуальных тем и расширяйте свои знания!
Узнать больше – https://adzbusiness.com/wer-einen-anderen-totet-ist-mit-freiheitsstrafe-von-zehn-bis-zu-zwanzig-jahren-oder-mit-lebenslanger-freiheitsstrafe-zu-bestrafen
¡Saludos, fanáticos del entretenimiento !
casinosextranjero.es – ideal para nuevos jugadores – https://www.casinosextranjero.es/ casinos extranjeros
¡Que vivas increíbles instantes inolvidables !
Profitez d’une abonnement IPTV exceptionnelle en 2025 avec le meilleur fournisseur Smart IPTV France ! Regardez plus de 63 000 chaînes HD & 4K, accédez à plus de 86 000 films et séries en VOD, et profitez d’une stabilité à 100 % sans interruptions. Regardez vos contenus préférés où que vous soyez, à tout moment et sur n’importe quel appareil : Smart TV, PC, mobile, tablette et plus encore ! Ne manquez plus aucun match, film ou série – optez pour la qualité et la performance d’un smart IPTV premium !
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Получить дополнительную информацию – https://astml.com/download/data-sheet-06-110
автоломбард в кемерово круглосуточно
24avtolombard-pts65.ru/kemerovo.html
автоломбард залог машины
Пять знаков Зодиака получат особенный подарок от судьбы до конца недели
https://x.com/kiselev_igr/status/1935256567458447599
“Merhaba kazanc avc?lar?!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://betpark2025.net/]betpark[/url]”
¡Saludos, seguidores del triunfo !
GuГa legal de uso para casino online extranjero – https://casinoextranjerosenespana.es/# п»їcasinos online extranjeros
¡Que disfrutes de triunfos épicos !
¡Saludos, visitantes de plataformas de apuestas !
Apuesta sin riesgo en casinos online extranjeros – https://www.casinoextranjerosenespana.es/# mejores casinos online extranjeros
¡Que disfrutes de oportunidades exclusivas !
Эта медицинская заметка содержит сжатую информацию о новых находках и методах в области здравоохранения. Мы предлагаем читателям свежие данные о заболеваниях, профилактике и лечении. Наша цель — быстро и доступно донести важную информацию, которая поможет в повседневной жизни и понимании здоровья.
Узнать больше – [url=https://narkolog-na-dom-krasnodar15.ru/]запой нарколог на дом[/url]
Портал Львів https://u-misti.lviv.ua останні новини Львова и области.
Свежие новости https://ktm.org.ua Украины и мира: политика, экономика, происшествия, культура, спорт. Оперативно, объективно, без фейков.
Сайт о строительстве https://solution-ltd.com.ua и дизайне: как построить, отремонтировать и оформить дом со вкусом.
деньги под залог птс круглосуточно
24avtolombard-pts65.ru
кредит под птс грузового
Авто портал https://real-voice.info для всех, кто за рулём: свежие автоновости, обзоры моделей, тест-драйвы, советы по выбору, страхованию и ремонту.
Учёные выяснили, зачем кошки следят за хозяевами, и это потрясающе
https://x.com/kiselev_igr/status/1935280417076068378
сервис займов под залог авто
24avtolombard-pts65.ru/ekb.html
кредит под залог автомобиля екатеринбург
Ученые раскрыли секрет странной формы Марса
https://x.com/kiselev_igr/status/1935334480073605459
Эта публикация исследует взаимосвязь зависимости и психологии. Мы обсудим, как психологические аспекты влияют на появление зависимостей и процесс выздоровления. Читатели смогут понять важность профессиональной поддержки и применения научных подходов в терапии.
Подробнее тут – [url=https://narkolog-na-dom-krasnodar12.ru/]запой нарколог на дом[/url]
Покупка дипломов ВУЗов в Москве — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы гарантируем, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 2580 клиентов воспользовались услугой — теперь ваша очередь.
[url=https://spbrcom1.ru/]Купить диплом о среднем образовании[/url] — ответим быстро, без лишних формальностей.
Мы предлагаем оформление дипломов ВУЗов в Москве — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы даем гарантию, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 2045 клиентов воспользовались услугой — теперь ваша очередь.
[url=https://spbrcom2.ru/]Купить диплом нового образца[/url] — ответим быстро, без лишних формальностей.
Мы предлагаем оформление дипломов ВУЗов по всей России и СНГ — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы гарантируем, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 4711 клиентов воспользовались услугой — теперь ваша очередь.
[url=https://inforepetitor1.ru/]Мы поможем[/url] — ответим быстро, без лишних формальностей.
Строительный портал https://apis-togo.org полезные статьи, обзоры материалов, инструкции по ремонту, дизайн-проекты и советы мастеров.
Комплексный строительный https://ko-online.com.ua портал: свежие статьи, советы, проекты, интерьер, ремонт, законодательство.
Всё о строительстве https://furbero.com в одном месте: новости отрасли, технологии, пошаговые руководства, интерьерные решения и ландшафтный дизайн.
Новини Львів https://faine-misto.lviv.ua последние новости и события – Файне Львов
кредит под птс
24avtolombard-pts65.ru/kemerovo.html
займ под птс кемерово
В этом обзоре мы обсудим современные методы борьбы с зависимостями, включая медикаментозную терапию и психотерапию. Мы представим последние исследования и их результаты, чтобы читатели могли быть в курсе наиболее эффективных подходов к лечению и поддержке.
Подробнее тут – [url=https://narkolog-na-dom-krasnodar15.ru/]нарколог на дом вывод[/url]
автоломбард залог машины
24avtolombard-pts65.ru/kazan.html
займ под птс автомобиля
Комплексное лечение на дому организовано по четкой схеме, состоящей из последовательных этапов. Каждый из них направлен на быстрое восстановление нормального функционирования организма.
Исследовать вопрос подробнее – http://vyvod-iz-zapoya-vladimir0.ru/srochnyj-vyvod-iz-zapoya-vladimir/
Когда запой начинает угрожать здоровью, оперативное вмешательство становится жизненно необходимым. В Туле опытные специалисты оказывают помощь на дому, позволяя начать лечение сразу же в комфортной обстановке. Такой формат терапии обеспечивает оперативную детоксикацию, восстановление нормального обмена веществ и стабилизацию работы внутренних органов, что особенно важно для пациентов, желающих избежать лишнего стресса и сохранить конфиденциальность.
Ознакомиться с деталями – https://vyvod-iz-zapoya-tula0.ru/vyvod-iz-zapoya-na-domu-tula
¡Saludos, participantes del juego !
casinos extranjeros sin lГmites de apuestas – п»їhttps://casinosextranjero.es/ casino online extranjero
¡Que vivas increíbles giros exitosos !
«В первые часы после окончания запоя организм наиболее уязвим, и своевременное вмешательство значительно снижает риски осложнений», — подчёркивает заведующая отделением наркологической реанимации Елена Морозова.
Получить дополнительные сведения – https://vyvod-iz-zapoya-krasnogorsk2.ru/vyvod-iz-zapoya-cena
Онлайн-портал https://leif.com.ua для женщин: мода, психология, рецепты, карьера, дети и любовь. Читай, вдохновляйся, общайся, развивайся!
кредит на карту без отказа [url=http://kredit-bez-otkaza-1.ru]кредит на карту без отказа[/url] .
Современный женский https://prowoman.kyiv.ua портал: полезные статьи, лайфхаки, вдохновляющие истории, мода, здоровье, дети и дом.
Мы предлагаем оформление дипломов ВУЗов по всей России и СНГ — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы даем гарантию, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 1779 клиентов воспользовались услугой — теперь ваша очередь.
[url=https://spbrcom2.ru/]На этой странице[/url] — ответим быстро, без лишних формальностей.
В этой заметке мы представляем шаги, которые помогут в процессе преодоления зависимостей. Рассматриваются стратегии поддержки и чек-листы для тех, кто хочет сделать первый шаг к выздоровлению. Наша цель — вдохновить читателей на положительные изменения и поддержать их в трудных моментах.
Узнать больше – [url=https://narkolog-na-dom-krasnodar11.ru/]нарколог на дом[/url]
Портал о маркетинге https://reklamspilka.org.ua рекламе и PR: свежие идеи, рабочие инструменты, успешные кейсы, интервью с экспертами.
кредит под птс кемерово
24avtolombard-pts65.ru/kemerovo.html
займ под залог авто
В этой публикации мы предложим ряд рекомендаций по избавлению от зависимостей и успешному восстановлению. Мы обсудим методы привлечения поддержки и важность самосознания. Эти советы помогут людям вернуться к нормальной жизни и стать на путь выздоровления.
Получить дополнительные сведения – [url=https://narkolog-na-dom-krasnodar11.ru/]выезд нарколога на дом[/url]
где взять деньги под залог авто
24avtolombard-pts65.ru
деньги под птс без машины
Очень советую https://krystacamea.com/screen-shot-2015-09-08-at-1-00-33-am/
Длительный запой может привести к серьезным осложнениям, таким как повреждение печени, почек, сердечно-сосудистые нарушения и нервные расстройства. Чем быстрее начинается вывод из запоя, тем ниже риск развития хронических заболеваний. Срочный вызов нарколога на дом позволяет в первые часы кризиса начать детоксикацию, что существенно повышает шансы на полное восстановление организма. В условиях экстренной ситуации каждая минута имеет решающее значение, и своевременная помощь становится ключом к сохранению здоровья и жизни.
Подробнее – https://vyvod-iz-zapoya-tula00.ru/vyvod-iz-zapoya-anonimno-tula
Эта информационная публикация освещает широкий спектр тем из мира медицины. Мы предлагаем читателям ясные и понятные объяснения современных заболеваний, методов профилактики и лечения. Информация будет полезна как пациентам, так и медицинским работникам, желающим поддержать уровень своих знаний.
Выяснить больше – [url=https://narkolog-na-dom-krasnodar11.ru/]вызов нарколога на дом[/url]
Предлагаю http://majoramitbansal.com/articles/opinion-thalaivar-is-coming-now-politicians-in-tamil-nadu-should-worry/
“Hey kazanc avc?lar?!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://damabet2025.com/]yeni uyelere freebet[/url]
Rulet masas? yuksek oranl?.
VPN’siz erisim, tek t?kla kay?t > 20 saniyede haz?r.
Bol sans!”
Комплексное лечение на дому организовано по четкой схеме, состоящей из последовательных этапов. Каждый из них направлен на быстрое восстановление нормального функционирования организма.
Подробнее – [url=https://vyvod-iz-zapoya-vladimir0.ru/]вывести из запоя[/url]
Профессиональный подход к лечению запоя на дому включает в себя несколько последовательных этапов, которые гарантируют комплексное восстановление организма. Такой системный метод помогает не только вывести токсичные вещества, но и обеспечить психологическую поддержку, необходимую для формирования устойчивых навыков самоконтроля и предотвращения повторных эпизодов зависимости.
Выяснить больше – [url=https://narcolog-na-dom-ryazan0.ru/]врач нарколог на дом рязанская область[/url]
В данном обзоре представлены основные направления и тренды в области медицины. Мы обсудим актуальные проблемы здравоохранения, свежие открытия и новые подходы, которые меняют представление о лечении и профилактике заболеваний. Эта информация будет полезна как специалистам, так и широкой публике.
Выяснить больше – [url=https://narkolog-na-dom-krasnodar11.ru/]врач нарколог на дом[/url]
Семейный портал https://stepandstep.com.ua статьи для родителей, игры и развивающие материалы для детей, советы психологов, лайфхаки.
Клуб родителей https://entertainment.com.ua пространство поддержки, общения и обмена опытом.
Туристический портал https://aliana.com.ua с лучшими маршрутами, подборками стран, бюджетными решениями, гидами и советами.
Всё о спорте https://beachsoccer.com.ua в одном месте: профессиональный и любительский спорт, фитнес, здоровье, техника упражнений и спортивное питание.
взять деньги под птс
24avtolombard-pts65.ru
автоломбард кредит под залог птс
При поступлении вызова нарколог незамедлительно приезжает на дом для проведения детального первичного осмотра. Врач собирает краткий анамнез, измеряет жизненно важные показатели — пульс, артериальное давление, температуру — и оценивает степень алкогольной интоксикации. Эти данные являются основой для разработки индивидуального плана лечения, позволяющего подобрать наиболее эффективные методы детоксикации.
Разобраться лучше – http://vyvod-iz-zapoya-tula00.ru
Специалист уточняет, сколько времени продолжается запой, какой тип алкоголя употребляется, а также наличие сопутствующих заболеваний. Тщательный анализ этих данных помогает определить оптимальные методы детоксикации и скорректировать терапевтическую стратегию для минимизации риска осложнений.
Исследовать вопрос подробнее – https://narcolog-na-dom-ryazan0.ru/vyzov-narkologa-na-dom-ryazan/
Запой – это критическое состояние, при котором организм подвергается сильной алкогольной интоксикации, что может привести к накоплению токсинов, нарушению обменных процессов и повреждению жизненно важных органов. В Туле, благодаря профессиональной помощи нарколога на дому, возможно оперативно начать лечение, не прибегая к госпитализации. Такой подход позволяет пациенту получить качественную терапию в комфортных условиях, сохраняя полную конфиденциальность и минимизируя стресс, связанный с посещением стационара.
Подробнее можно узнать тут – [url=https://vyvod-iz-zapoya-tula00.ru/]вывод из запоя круглосуточно тула[/url]
займ залог птс автомобиля
24avtolombard-pts65.ru/nsk.html
деньги под залог автомобиля авто остается
Системы автоматизированного дозирования обеспечивают точное введение медикаментов, что минимизирует риск побочных эффектов. Постоянный мониторинг жизненно важных показателей позволяет врачу корректировать терапию в режиме реального времени, гарантируя безопасность процедуры.
Подробнее тут – [url=https://vyvod-iz-zapoya-vladimir0.ru/]вывод из запоя недорого владимир[/url]
После первичной диагностики начинается активная фаза медикаментозного вмешательства. Современные препараты вводятся капельничным методом, что позволяет оперативно снизить концентрацию токсинов в крови и восстановить нормальные обменные процессы. Этот этап критически важен для стабилизации работы внутренних органов, таких как печень, почки и сердце.
Исследовать вопрос подробнее – https://narcolog-na-dom-ryazan0.ru/vyzov-narkologa-na-dom-ryazan
Крайне советую http://sarebangem.com/product/%da%af%d9%88%d9%87%d8%b1-%d8%b4%d9%86%d8%a7%d8%b3%db%8c/comment-page-13/
When exchanges freeze, Trezor gives you instant access to your funds anytime, anywhere.
https://trezour-site-web.com/
кредит под залог автомобиля
24avtolombard-pts65.ru/nsk.html
деньги под птс новосибирск
При поступлении вызова нарколог незамедлительно приезжает на дом для проведения детального первичного осмотра. Врач собирает краткий анамнез, измеряет жизненно важные показатели — пульс, артериальное давление, температуру — и оценивает степень алкогольной интоксикации. Эти данные являются основой для разработки индивидуального плана лечения, позволяющего подобрать наиболее эффективные методы детоксикации.
Ознакомиться с деталями – [url=https://vyvod-iz-zapoya-tula00.ru/]вывод из запоя анонимно[/url]
Этот документ охватывает важные аспекты медицинской науки, сосредотачиваясь на ключевых вопросах, касающихся здоровья населения. Мы рассматриваем свежие исследования, клинические рекомендации и лучшие практики, которые помогут улучшить качество лечения и профилактики заболеваний. Читатели получат возможность углубиться в различные медицинские дисциплины.
Подробнее – [url=https://narkolog-na-dom-krasnodar15.ru/]vrach-narkolog-na-dom[/url]
Эта статья подробно расскажет о процессе выздоровления, который включает в себя эмоциональную, физическую и психологическую реабилитацию. Мы обсуждаем значимость поддержки и наличие профессиональных программ. Читатели узнают, как строить новую жизнь и не возвращаться к старым привычкам.
Подробнее можно узнать тут – [url=https://narkolog-na-dom-krasnodar11.ru/]вызов нарколога на дом[/url]
Этот обзор сосредоточен на различных подходах к избавлению от зависимости. Мы изучим традиционные и альтернативные методы, а также их сочетание для достижения максимальной эффективности. Читатели смогут открыть для себя новые стратегии и подходы, которые помогут в их борьбе с зависимостями.
Получить дополнительные сведения – [url=https://narkolog-na-dom-krasnodar11.ru/]врач нарколог на дом[/url]
Эта доказательная статья представляет собой глубокое погружение в успехи и вызовы лечения зависимостей. Мы обращаемся к научным исследованиям и опыте специалистов, чтобы предоставить читателям надежные данные об эффективности различных методик. Изучите, что работает лучше всего, и получите информацию от экспертов.
Подробнее можно узнать тут – [url=https://narkolog-na-dom-krasnodar11.ru/]нарколог на дом круглосуточно[/url]
займ под птс
avtolombard-pts65.ru/ekb.html
взять займ под залог машины
Гороскоп на 19 июня 2025 года: Кому сегодня улыбнётся удача?
https://x.com/kiselev_igr/status/1935569425278566881
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Выяснить больше – https://hoteldemontaulbain.fr/en/welcome-to-the-hotel-of-montaulbain-to-verdun/facebook-icon-preview-1-400×400
Специалист уточняет, сколько времени продолжается запой, какой тип алкоголя употребляется, а также наличие сопутствующих заболеваний. Тщательный анализ этих данных помогает определить оптимальные методы детоксикации и скорректировать терапевтическую стратегию для минимизации риска осложнений.
Подробнее тут – [url=https://narcolog-na-dom-ryazan0.ru/]вызов нарколога на дом[/url]
займ залог птс
avtolombard-pts65.ru/ekb.html
взять займ под залог машины
В этом обзорном материале представлены увлекательные детали, которые находят отражение в различных аспектах жизни. Мы исследуем непонятные и интересные моменты, позволяя читателю увидеть картину целиком. Погрузитесь в мир знаний и удивительных открытий!
Изучить вопрос глубже – https://tnn-development.com/gew
События Днепр https://u-misti.dp.ua последние новости Днепра и области, обзоры и самое интересное
После поступления в клинику проводится осмотр, измеряется давление, оценивается общее состояние. При необходимости проводятся экспресс-анализы на содержание веществ и ЭКГ.
Разобраться лучше – [url=https://narkologicheskaya-klinika-voronezh9.ru/]chastnaya narkologicheskaya klinika voronezh[/url]
Новости Украины https://useti.org.ua в реальном времени. Всё важное — от официальных заявлений до мнений экспертов.
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Получить дополнительные сведения – https://www.clauskc.dk/blog.php/=https:/www.binance.com/pt-PT/blog/blog/vr-motors.ru?n=485
Информационный портал https://comart.com.ua о строительстве и ремонте: полезные советы, технологии, идеи, лайфхаки, расчёты и выбор материалов.
Архитектурный портал https://skol.if.ua современные проекты, урбанистика, дизайн, планировка, интервью с архитекторами и тренды отрасли.
Всё о строительстве https://ukrainianpages.com.ua просто и по делу. Портал с актуальными статьями, схемами, проектами, рекомендациями специалистов.
автоломбард залог птс
avtolombard-pts65.ru/kazan.html
кредит под птс казань
“Selam forum ahalisi!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://klasbahis2025.com]klasbahisTR[/url]”
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Подробнее можно узнать тут – https://influencerism.com/2023/08/03/hello-world
Новости Украины https://hansaray.org.ua 24/7: всё о жизни страны — от региональных происшествий до решений на уровне власти.
Всё об автомобилях https://autoclub.kyiv.ua в одном месте. Обзоры, новости, инструкции по уходу, автоистории и реальные тесты.
кредит под птс
avtolombard-pts65.ru/kazan.html
автоломбард в казани под залог птс
Единственный знак зодиака, который является тайной для астрологии
https://x.com/kiselev_igr/status/1935653424621641954
Строительный журнал https://dsmu.com.ua идеи, технологии, материалы, дизайн, проекты, советы и обзоры. Всё о строительстве, ремонте и интерьере
Новостной портал Одесса https://u-misti.odesa.ua последние события города и области. Обзоры и много интресного о жизни в Одессе.
Портал о строительстве https://tozak.org.ua от идеи до готового дома. Проекты, сметы, выбор материалов, ошибки и их решения.
Want lower fees? Jupiter’s aggregator cuts your cost across multiple Solana DEXs.
Jupiter login
Swap tokens through Ledger-integrated DEXs without compromising private key safety.
Ledger Wallet Crypto
автомобиль под залог
avtolombard-pts65.ru/kemerovo.html
залог под птс авто
Зависимость от психоактивных веществ — серьёзная проблема, которая становится всё актуальнее в современном мире. Алкоголизм, наркомания и игромания представляют угрозу как для здоровья отдельного человека, так и для общества в целом. В условиях растущей нагрузки на систему здравоохранения Наркологическая клиника “Возрождение” предлагает комплексные решения для тех, кто страдает от различных видов зависимости. Мы придерживаемся индивидуального подхода, что позволяет достигать высоких результатов в лечении и реабилитации.
Узнать больше – https://медицина-вывод-из-запоя.рф/vyvod-iz-zapoya-cena-v-nizhnem-novgoroge.xn--p1ai/
Покупка дипломов ВУЗов по всей России и СНГ — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы гарантируем, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 4492 клиентов воспользовались услугой — теперь ваша очередь.
[url=https://spbrcom2.ru/]Ознакомиться здесь[/url] — ответим быстро, без лишних формальностей.
Мы создаем благоприятные условия для полного выздоровления и восстановления личности каждого пациента. Наша команда разрабатывает индивидуальные программы терапии, учитывая особенности здоровья и психического состояния человека. Лечение строится на научно обоснованных методах, что позволяет нам добиваться высоких результатов.
Изучить вопрос глубже – http://быстро-вывод-из-запоя.рф/
В нашей клинике работают врачи-наркологи, психологи и психиатры с многолетним опытом в лечении зависимостей. Все специалисты регулярно повышают свою квалификацию, участвуя в семинарах и конференциях, чтобы обеспечивать своим пациентам наиболее современное и качественное лечение.
Подробнее – http://быстро-вывод-из-запоя.рф/
Прямо здесь можно получить мессенджер-бот “Глаз Бога”, позволяющий найти данные о человеке из открытых источников.
Бот активно ищет по номеру телефона, анализируя доступные данные в Рунете. Через бота доступны 5 бесплатных проверок и глубокий сбор по имени.
Сервис актуален согласно последним данным и поддерживает мультимедийные данные. Глаз Бога гарантирует узнать данные в соцсетях и отобразит информацию мгновенно.
телеграм бот глаз бога проверка
Такой инструмент — выбор в анализе персон удаленно.
Наши специалисты гарантируют пациентам конфиденциальность и внимательное отношение, создавая атмосферу доверия. Врач сопровождает пациента на каждом этапе лечения, отслеживая его состояние и корректируя терапию по мере необходимости. Профессионализм и забота наших специалистов являются основой успешной реабилитации.
Получить дополнительную информацию – https://быстро-вывод-из-запоя.рф/vyvod-iz-zapoya-v-kruglosutochno-v-volgograde.xn--p1ai/
Городской портал Одессы https://faine-misto.od.ua последние новости и происшествия в городе и области
Мы также уделяем большое внимание социальной адаптации. Пациенты учатся восстанавливать навыки общения и обретать уверенность в себе, что помогает в будущем избежать рецидивов и успешно вернуться к полноценной жизни, будь то работа или учеба.
Получить дополнительные сведения – https://быстро-вывод-из-запоя.рф/vyvod-iz-zapoya-anonimno-v-volgograde.xn--p1ai/
На данном сайте вы найдете мессенджер-бот “Глаз Бога”, что проверить всю информацию о человеке по публичным данным.
Сервис функционирует по ФИО, обрабатывая актуальные базы онлайн. Благодаря ему осуществляется бесплатный поиск и детальный анализ по фото.
Сервис актуален на 2025 год и включает фото и видео. Бот поможет найти профили в открытых базах и отобразит сведения в режиме реального времени.
глаз бога сайт
Это бот — идеальное решение при поиске персон через Telegram.
деньги срочно под залог авто
avtolombard-pts65.ru
кредит под залог грузового авто
Особое внимание в клинике уделяется профилактике рецидивов. Мы обучаем пациентов навыкам управления стрессом, контролю эмоций и принципам здорового образа жизни. Наша цель — обеспечить длительное восстановление и снизить риск возврата к зависимости.
Подробнее – http://срочно-вывод-из-запоя.рф
Наш подход охватывает все аспекты реабилитации, помогая пациентам справиться с зависимостями и вернуться к полноценной жизни.
Изучить вопрос глубже – http://медицина-вывод-из-запоя.рф/vyvod-iz-zapoya-v-stacionare-v-nizhnem-novgoroge.xn--p1ai/https://медицина-вывод-из-запоя.рф
автоломбард под залог
avtolombard-pts65.ru
кредит по залог авто
Информационный портал https://dailynews.kyiv.ua актуальные новости, аналитика, интервью и спецтемы.
Новостной портал https://news24.in.ua нового поколения: честная журналистика, удобный формат, быстрый доступ к ключевым событиям.
Портал для женщин https://a-k-b.com.ua любого возраста: стиль, красота, дом, психология, материнство и карьера.
Онлайн-новости https://arguments.kyiv.ua без лишнего: коротко, по делу, достоверно. Политика, бизнес, происшествия, спорт, лайфстайл.
¡Hola, fanáticos del riesgo !
Casinos online extranjeros sin lГmites geogrГЎficos – https://www.casinoextranjero.es/ casinoextranjero.es
¡Que vivas jugadas asombrosas !
Мы предлагаем оформление дипломов ВУЗов по всей России и СНГ — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы даем гарантию, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 3828 клиентов воспользовались услугой — теперь ваша очередь.
[url=https://inforepetitor1.ru/]Мы поможем[/url] — ответим быстро, без лишних формальностей.
Мы предлагаем оформление дипломов ВУЗов в Москве — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы даем гарантию, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 4958 клиентов воспользовались услугой — теперь ваша очередь.
[url=https://spbrcom2.ru/]Сайт компании[/url] — ответим быстро, без лишних формальностей.
Команда врачей клиники “Чистый Путь” состоит из квалифицированных специалистов в области наркологии с обширным опытом работы. Каждый врач обладает глубокими знаниями в фармакологии, психофармакологии и психотерапии, регулярно повышает свою квалификацию на профильных конференциях и семинарах, чтобы использовать в своей практике самые современные и эффективные методы лечения.
Исследовать вопрос подробнее – http://срочно-вывод-из-запоя.рф
¡Hola, estrategas del azar !
Mejores estrategias para casinos online extranjeros – https://casinoextranjero.es/# casinos extranjeros
¡Que vivas éxitos notables !
Миссия клиники — оказание комплексной помощи людям с зависимостями. Основные задачи, которые мы ставим перед собой:
Углубиться в тему – https://медицина-вывод-из-запоя.рф/vyvod-iz-zapoya-cena-v-nizhnem-novgoroge.xn--p1ai
выгодный кредит под залог авто
avtolombard-pts65.ru/nsk.html
где лучше взять кредит под залог авто
Мы уделяем особое внимание индивидуальному подходу к каждому пациенту, понимая, что причины и проявления зависимости у всех разные. Тщательная диагностика позволяет учитывать медицинские, психологические и социальные аспекты каждого случая, на основе чего разрабатываются персонализированные программы лечения. Они включают медикаментозную терапию, психотерапевтические методы и мероприятия по социальной адаптации.
Подробнее – http://срочно-вывод-из-запоя.рф/vyvod-iz-zapoya-v-kruglosutochno-v-chelyabinske.xn--p1ai/
“Hey kazanc avc?lar?!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://lunabet2025.com/]lunabet[/url]”
оформить займ под залог птс
avtolombard-pts65.ru/nsk.html
займ залог авто
Мировые новости https://ua-novosti.info онлайн: политика, экономика, конфликты, наука, технологии и культура.
Только главное https://ua-vestnik.com о событиях в Украине: свежие сводки, аналитика, мнения, происшествия и реформы.
Женский портал https://woman24.kyiv.ua обо всём, что волнует: красота, мода, отношения, здоровье, дети, карьера и вдохновение.
защитный герметичный кейс plastcase
¡Bienvenidos, apostadores dedicados !
Casino fuera de EspaГ±a sin verificaciГіn obligatoria – https://casinoporfuera.guru/# casinoporfuera
¡Que disfrutes de maravillosas botes impresionantes!
Мы создаем благоприятные условия для полного выздоровления и восстановления личности каждого пациента. Наша команда разрабатывает индивидуальные программы терапии, учитывая особенности здоровья и психического состояния человека. Лечение строится на научно обоснованных методах, что позволяет нам добиваться высоких результатов.
Выяснить больше – https://быстро-вывод-из-запоя.рф/vyvod-iz-zapoya-v-kruglosutochno-v-volgograde.xn--p1ai/
Советую https://www.rubin-nightclub.de/rubin_nightclub_logo/
iko сертификат кайтсерфинг Кайт школа СПБ предлагает обучение кайтингу и кайтсёрфингу в живописных местах. Здесь работают опытные инструкторы, которые помогут вам быстро освоить необходимые навыки и уверенно чувствовать себя на воде.
Мы создаем благоприятные условия для полного выздоровления и восстановления личности каждого пациента. Наша команда разрабатывает индивидуальные программы терапии, учитывая особенности здоровья и психического состояния человека. Лечение строится на научно обоснованных методах, что позволяет нам добиваться высоких результатов.
Узнать больше – https://быстро-вывод-из-запоя.рф/vyvod-iz-zapoya-cena-v-volgograde.xn--p1ai/
получить деньги под залог машины
e-avtolombard-pts65.ru/ekb.html
кредит залог авто
кредит под птс екатеринбург
e-avtolombard-pts65.ru/ekb.html
кредиты под залог машины с правом вождения
Офисная мебель https://officepro54.ru в Новосибирске купить недорого от производителя
Онлайн займ денег взять займ онлайн
Republic window and door selection, offered.
Update your home, with windows and doors.
Cleanliness and style, Republic.
Quality installation.
Optimal interior solutions, with Republic windows and doors.
Update your home, by Republic.
Energy-efficient solutions, from Republic company.
A range that inspires, with Republic windows and doors.
Reliable windows and doors, at affordable prices.
Beautiful and functional.
Doors and windows for any style, with Republic products.
A choice that will make your home better, by Republic.
Buy quality windows and doors with a discount, from Republic.
Doors and windows that will transform your home, with Republic.
Modern window technologies, for comfortable living.
Don’t settle for less, by Republic company.
Cut heating costs, with products.
Every corner of your home matters, by Republic company.
Experts in windows and doors, by Republic.
double glazing melbourne [url=http://wearehoist.com/double-glazed-melbourne/]http://wearehoist.com/double-glazed-melbourne/[/url] .
Миссия клиники — оказание комплексной помощи людям с зависимостями. Основные задачи, которые мы ставим перед собой:
Выяснить больше – http://медицина-вывод-из-запоя.рф/vyvod-iz-zapoya-anonimno-v-nizhnem-novgoroge.xn--p1ai/
Наши специалисты гарантируют пациентам конфиденциальность и внимательное отношение, создавая атмосферу доверия. Врач сопровождает пациента на каждом этапе лечения, отслеживая его состояние и корректируя терапию по мере необходимости. Профессионализм и забота наших специалистов являются основой успешной реабилитации.
Подробнее тут – https://быстро-вывод-из-запоя.рф/vyvod-iz-zapoya-v-kruglosutochno-v-volgograde.xn--p1ai
Оформиление дипломов ВУЗов в Москве — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы гарантируем, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 4251 клиентов воспользовались услугой — теперь ваша очередь.
[url=https://inforepetitor1.ru/]Купить диплом вуза[/url] — ответим быстро, без лишних формальностей.
Команда врачей клиники “Чистый Путь” состоит из квалифицированных специалистов в области наркологии с обширным опытом работы. Каждый врач обладает глубокими знаниями в фармакологии, психофармакологии и психотерапии, регулярно повышает свою квалификацию на профильных конференциях и семинарах, чтобы использовать в своей практике самые современные и эффективные методы лечения.
Получить дополнительную информацию – https://срочно-вывод-из-запоя.рф/vyvod-iz-zapoya-v-kruglosutochno-v-chelyabinske.xn--p1ai/
Klavier mit noten noten auf dem klavier
Миссия клиники — оказание комплексной помощи людям с зависимостями. Основные задачи, которые мы ставим перед собой:
Выяснить больше – http://
автоломбард казань
e-avtolombard-pts65.ru/kazan.html
автоломбард в казани под залог птс
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Подробнее тут – https://serinfondemo2.com.es/2022/01/29/decisions-for-building-flexible-components-devtools-browser-3
Этот документ охватывает важные аспекты медицинской науки, сосредотачиваясь на ключевых вопросах, касающихся здоровья населения. Мы рассматриваем свежие исследования, клинические рекомендации и лучшие практики, которые помогут улучшить качество лечения и профилактики заболеваний. Читатели получат возможность углубиться в различные медицинские дисциплины.
Разобраться лучше – https://pro-analiz.ru/protsedury/posledstviya-chrezmernogo-upotrebleniya-alkogolya-ponimanie-riskov-dlya-zdorovya-i-blagopoluchiya.html
Эта доказательная статья представляет собой глубокое погружение в успехи и вызовы лечения зависимостей. Мы обращаемся к научным исследованиям и опыте специалистов, чтобы предоставить читателям надежные данные об эффективности различных методик. Изучите, что работает лучше всего, и получите информацию от экспертов.
Разобраться лучше – https://vrachi-na-domu.ru/uuslugi-narkologa-na-domu-vygodno-i-udobno
В этой публикации мы рассматриваем важную тему борьбы с зависимостями, включая алкогольную и наркотическую зависимости. Мы обсудим методы лечения, реабилитации и поддержку, которые могут помочь людям, столкнувшимся с этой проблемой. Читатели узнают о перспективах выздоровления и важности комплексного подхода.
Детальнее – https://medtechnika-nt.ru/lechenie-podrostkovogo-alkogolizma-v-rostovenadonu-uslugi-chastnoy-skoroy-pomoschi–1.html
кайтсёрфинг сертификат Кайтсерфинг Хургада предлагает отличные условия для катания. Здесь можно найти множество школ и станций, где можно арендовать оборудование и пройти обучение.
Хмельницький новини https://u-misti.khmelnytskyi.ua огляди, новини, сайт Хмельницького
Предсказавшая COVID-19 “новая Ванга” назвала ближайшую дату Судного дня
https://x.com/kiselev_igr/status/1935957113026539690
Заказать диплом университета!
Приобретение диплома через надежную компанию дарит множество преимуществ для покупателя. Заказать диплом университета у надежной организации: [url=http://doks-v-gorode-penza-58.ru/]doks-v-gorode-penza-58.ru[/url]
“Selam bahisseverler!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://betzula2025.net/]betzula2025.net[/url]”
В этой информационной статье вы найдете интересное содержание, которое поможет вам расширить свои знания. Мы предлагаем увлекательный подход и уникальные взгляды на обсуждаемые темы, побуждая пользователей к активному мышлению и критическому анализу!
Выяснить больше – https://alnica-internacional.com/product/barrels-of-oil
Этот информационный материал привлекает внимание множеством интересных деталей и необычных ракурсов. Мы предлагаем уникальные взгляды на привычные вещи и рассматриваем вопросы, которые волнуют общество. Будьте в курсе актуальных тем и расширяйте свои знания!
Подробнее тут – https://admin.dnn.mn/wp/gamshigt-tesvertei-ulaanbaatar-tusliig-niisleliin-9
AntiNarcoForum — форум помощи при зависимостях, обеспечивающий анонимность и поддержку каждому участнику. Здесь доступны проверенные методики лечения, реальные истории выздоровления и профессиональные рекомендации специалистов для эффективного преодоления зависимости.
Детальнее – [url=https://antinarcoforum.ru/alkogolizm/zhenskij-alkogolizm-osobennosti-techeniya-i-lecheniya/]про женский алкоголизм[/url]
ломбард займ под птс
e-avtolombard-pts65.ru/kemerovo.html
кредит под залог автомобиля кемерово
¡Bienvenidos, fanáticos del azar !
Casino fuera de EspaГ±a sin necesidad de validar datos – https://casinoporfuera.guru/# casino online fuera de espaГ±a
¡Que disfrutes de maravillosas botes impresionantes!
заказать отчет по практике недорого купить отчет по производственной практике
На Солнце произошла мощная вспышка: ученые оценили ее влияние на Землю
https://x.com/kiselev_igr/status/1936005213556523327
сколько стоит реферат купить реферат цена
написание дипломов на заказ https://diplomsdayu.ru
Экстренная установка капельницы необходима, если пациент находится в состоянии запоя более 2–3 дней или испытывает симптомы тяжелой интоксикации алкоголем:
Подробнее можно узнать тут – http://kapelnica-ot-zapoya-sochi00.ru/kapelnicza-ot-zapoya-detoks-sochi/
Алкогольная и наркотическая зависимость являются серьёзными заболеваниями, требующими оперативного и квалифицированного вмешательства. Когда речь идёт о критическом состоянии пациента, особенно после длительного употребления алкоголя или наркотических веществ, время играет ключевую роль. Клиника «РеабилитАльянс» в Краснодаре предлагает услугу нарколога на дом, обеспечивая пациентам необходимую помощь в любой момент дня и ночи. Наши специалисты готовы оперативно выехать по указанному адресу и предоставить все необходимые медицинские процедуры на месте.
Подробнее тут – [url=https://narcolog-na-dom-krasnodar00.ru/]нарколог на дом вывод краснодар[/url]
5 невероятных совпадений, в которые сложно поверить
https://x.com/kiselev_igr/status/1936028762325274796
Нужен монтаж отопления в Алматы? Профессиональные специалисты быстро и качественно установят систему отопления в доме, квартире или офисе. Работаем с любыми типами оборудования, даём гарантию и обеспечиваем выезд в течение часа. Доступные цены и индивидуальный подход к каждому клиенту: https://montazh-otopleniya.kz/
Медпортал https://medportal.co.ua украинский блог о медициние и здоровье. Новости, статьи, медицинские учреждения
кредит под залог машины не лишаясь ее
e-avtolombard-pts65.ru/nsk.html
займ по залог авто
кредит под залог авто без отказа
e-avtolombard-pts65.ru
автоломбард под автомобиль
Когда запой превращается в угрозу для жизни, оперативное вмешательство становится критически важным. В Тюмени, Тюменская область, опытные наркологи предлагают услугу установки капельницы от запоя прямо на дому. Такой метод позволяет начать детоксикацию с использованием современных медикаментов, что способствует быстрому выведению токсинов, восстановлению обменных процессов и нормализации работы внутренних органов. Лечение на дому обеспечивает комфортную обстановку, полную конфиденциальность и индивидуальный подход к каждому пациенту.
Подробнее можно узнать тут – [url=https://kapelnica-ot-zapoya-tyumen00.ru/]капельница от запоя тюменская область[/url]
AntiNarcoForum — форум помощи при зависимостях, обеспечивающий анонимность и поддержку каждому участнику. Здесь доступны проверенные методики лечения, реальные истории выздоровления и профессиональные рекомендации специалистов для эффективного преодоления зависимости.
Подробнее тут – [url=https://antinarcoforum.ru/alkogolizm/sovremennye-metody-lecheniya-alkogolizma-plyusy-i-minusy/]методы лечения алкоголизма[/url]
Наша миссия заключается в предоставлении качественной помощи людям, страдающим от зависимостей. Мы стремимся создать безопасную и поддерживающую атмосферу, где каждый сможет получить необходимую помощь. Основная цель — восстановление здоровья, психоэмоционального состояния и социальной адаптации.
Ознакомиться с деталями – [url=https://tajnyj-vyvod-iz-zapoya.ru/vyvod-iz-zapoya-anonimno-v-omske.ru/]вывод из запоя омск[/url]
Мы предлагаем оформление дипломов ВУЗов в Москве — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы гарантируем, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 3899 клиентов воспользовались услугой — теперь ваша очередь.
[url=http://inforepetitor5.ru/]Звоните[/url] — ответим быстро, без лишних формальностей.
Выезд врача-нарколога из клиники «ТрезвоПрофи» на дом происходит в любое время суток, включая выходные и праздники. Перед началом детоксикации врач проводит осмотр, измеряет давление, частоту пульса, уровень кислорода в крови и подбирает индивидуальную схему лечения. Сама процедура обычно занимает от 1 до 2 часов и проводится под строгим контролем врача.
Подробнее можно узнать тут – [url=https://kapelnica-ot-zapoya-sochi00.ru/]kapelnicza-ot-zapoya-czena sochi[/url]
Комплексное лечение организовано по строго отлаженной схеме, которая включает несколько последовательных этапов, позволяющих обеспечить оперативное и безопасное восстановление организма.
Изучить вопрос глубже – [url=https://kapelnica-ot-zapoya-tyumen00.ru/]капельницы от запоятюмень[/url]
Здесь доступен сервис “Глаз Бога”, позволяющий собрать всю информацию о гражданине через открытые базы.
Сервис работает по ФИО, анализируя актуальные базы онлайн. Благодаря ему доступны 5 бесплатных проверок и полный отчет по запросу.
Платфор ма проверен согласно последним данным и охватывает фото и видео. Сервис сможет найти профили в соцсетях и отобразит результаты в режиме реального времени.
глаз бога программа для поиска людей бесплатно
Это сервис — помощник в анализе граждан удаленно.
Оформиление дипломов ВУЗов в Москве — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы даем гарантию, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 2185 клиентов воспользовались услугой — теперь ваша очередь.
[url=http://spbrcom6.ru/]Купить диплом вуза[/url] — ответим быстро, без лишних формальностей.
займ под птс
infoavtolombard-pts65.ru/ekb.html
автоломбард под птс в екатеринбурге
https://astv.ru/news/materials/vypusknoj-v-detskom-sadu-kak-sdelat-prazdnik-po-nastoyashemu-krutym
При длительном запое в организме накапливаются вредные токсины, что ведёт к нарушениям работы сердца, печени, почек и других жизненно важных органов. Чем быстрее начинается терапия, тем выше шансы избежать серьёзных осложнений и обеспечить качественное восстановление. Метод капельничного лечения позволяет оперативно начать детоксикацию, что особенно важно для спасения жизни и предупреждения хронических последствий злоупотребления алкоголем.
Получить дополнительные сведения – https://kapelnica-ot-zapoya-tyumen00.ru/kapelnicza-ot-zapoya-na-domu-tyumen
деньги под залог птс круглосуточно
e-avtolombard-pts65.ru/nsk.html
авто под залог
Платформа AntiNarcoForum объединяет людей, нуждающихся в анонимной и квалифицированной помощи при игровой, алкогольной или наркотической зависимости. Форум предоставляет возможность получить консультации от специалистов и пообщаться с людьми, успешно справившимися с аналогичными проблемами.
Детальнее – [url=https://antinarcoforum.ru/narkozavisimost/mify-o-narkomanii-pochemu-zavisimost-ne-slabost-voli/]зависимость это болезнь[/url]
“Sst kazanc avc?lar?!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://XturkaOnline.com/]slot oyunlar? %100[/url]
Canl? bahis 24/7 ac?k.
VPN’siz erisim, tek t?kla kay?t > 15 saniyede haz?r.
Bol sans!”
Файне Винница https://faine-misto.vinnica.ua новости и события Винницы сегодня. Городской портал, обзоры.
Зависимости часто сопровождаются физическими и психологическими нарушениями, требующими комплексного подхода. Мы убеждены, что успешное лечение невозможно без индивидуального подхода, что делает нашу клинику отличным местом для тех, кто нуждается в поддержке.
Подробнее – [url=https://tajnyj-vyvod-iz-zapoya.ru/vyvod-iz-zapoya-v-stacionare-v-omske.ru/]http://tajnyj-vyvod-iz-zapoya.ru/vyvod-iz-zapoya-na-domu-v-omske.ru/[/url]
Выезд врача-нарколога из клиники «ТрезвоПрофи» на дом происходит в любое время суток, включая выходные и праздники. Перед началом детоксикации врач проводит осмотр, измеряет давление, частоту пульса, уровень кислорода в крови и подбирает индивидуальную схему лечения. Сама процедура обычно занимает от 1 до 2 часов и проводится под строгим контролем врача.
Получить дополнительные сведения – [url=https://kapelnica-ot-zapoya-sochi00.ru/]врач на дом капельница от запоя сочи[/url]
В нашем центре доступны следующие виды помощи:
Узнать больше – [url=https://tajnyj-vyvod-iz-zapoya.ru/vyvod-iz-zapoya-v-stacionare-v-omske.ru/]вывод из запоя недорого[/url]
При длительном запое в организме накапливаются вредные токсины, что ведёт к нарушениям работы сердца, печени, почек и других жизненно важных органов. Чем быстрее начинается терапия, тем выше шансы избежать серьёзных осложнений и обеспечить качественное восстановление. Метод капельничного лечения позволяет оперативно начать детоксикацию, что особенно важно для спасения жизни и предупреждения хронических последствий злоупотребления алкоголем.
Исследовать вопрос подробнее – http://
займ онлайн https://zajmy-onlajn.ru
Наша миссия заключается в предоставлении качественной помощи людям, страдающим от зависимостей. Мы стремимся создать безопасную и поддерживающую атмосферу, где каждый сможет получить необходимую помощь. Основная цель — восстановление здоровья, психоэмоционального состояния и социальной адаптации.
Подробнее – [url=https://tajnyj-vyvod-iz-zapoya.ru/vyvod-iz-zapoya-v-stacionare-v-omske.ru/]http://tajnyj-vyvod-iz-zapoya.ru[/url]
Экстренная установка капельницы необходима, если пациент находится в состоянии запоя более 2–3 дней или испытывает симптомы тяжелой интоксикации алкоголем:
Получить дополнительную информацию – [url=https://kapelnica-ot-zapoya-sochi00.ru/]капельница от запоя анонимно[/url]
AntiNarcoForum — анонимное сообщество помощи людям, страдающим от алкогольной, наркотической и игровой зависимости. На платформе доступны истории выздоровления, консультации специалистов, а также постоянная поддержка от людей, преодолевших схожие трудности.
Изучить вопрос глубже – [url=https://antinarcoforum.ru/rodstvenniki-i-blizkie-zavisimyh/sozavisimost-kogda-spasaya-my-teryaem-sebya/]созависимость это в психологии определение[/url]
Как отмечает врач-нарколог клиники «РеабилитАльянс» Павел Сомов, «чем раньше начато лечение, тем выше шансы на скорейшее выздоровление без серьезных последствий для здоровья».
Выяснить больше – [url=https://narcolog-na-dom-krasnodar00.ru/]вызвать нарколога на дом краснодар[/url]
После процедуры пациент чувствует значительное облегчение состояния, улучшение самочувствия и снижение тяги к алкоголю.
Разобраться лучше – https://kapelnica-ot-zapoya-sochi00.ru/
Мы предлагаем оформление дипломов ВУЗов в Москве — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы даем гарантию, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 2939 клиентов воспользовались услугой — теперь ваша очередь.
[url=http://inforepetitor4.ru/]Диплом цена[/url] — ответим быстро, без лишних формальностей.
Оформиление дипломов ВУЗов по всей России и СНГ — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы даем гарантию, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 4032 клиентов воспользовались услугой — теперь ваша очередь.
[url=http://inforepetitor5.ru/]Купить диплом недорого[/url] — ответим быстро, без лишних формальностей.
Платформа AntiNarcoForum объединяет людей, нуждающихся в анонимной и квалифицированной помощи при игровой, алкогольной или наркотической зависимости. Форум предоставляет возможность получить консультации от специалистов и пообщаться с людьми, успешно справившимися с аналогичными проблемами.
Получить больше информации – [url=https://antinarcoforum.ru/narkozavisimost/mozhno-li-vylechit-narkomaniyu-navsegda-mnenie-speczialistov/]как вылечить от наркозависимости[/url]
The demand for balloon delivery in Dubai is rapidly increasing. Various events and celebrations are enhanced by the presence of vibrant balloons, making balloon delivery a sought-after service.
birthday balloons delivery dubai [url=https://www.bestwedding-video.com/product-category/birthday-balloons/]https://www.bestwedding-video.com/product-category/birthday-balloons/[/url] .
https://nbj.ru/publs/kreditovanie_dlya_obsledovaniya_i_lecheniya/69387/
деньги под залог птс круглосуточно
infoavtolombard-pts65.ru
кредит под залог машины
Покупка дипломов ВУЗов в Москве — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы даем гарантию, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 4933 клиентов воспользовались услугой — теперь ваша очередь.
[url=http://spbrcom5.ru/]Смотреть тут[/url] — ответим быстро, без лишних формальностей.
Капельница от запоя — это комплексная процедура, направленная на быстрое выведение токсинов, нормализацию обменных процессов и восстановление жизненно важных функций организма. Врачи-наркологи подбирают индивидуальный состав капельницы, исходя из состояния пациента. В стандартный набор препаратов обычно входят:
Получить больше информации – [url=https://kapelnica-ot-zapoya-sochi00.ru/]вызвать капельницу от запоя на дому[/url]
После процедуры пациент чувствует значительное облегчение состояния, улучшение самочувствия и снижение тяги к алкоголю.
Разобраться лучше – [url=https://kapelnica-ot-zapoya-sochi00.ru/]капельница от запоя на дому краснодарский край[/url]
“Sst kazanc avc?lar?!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://BetturkeyGiris2025.net/]bitcoin ile bahis[/url]
Rulet masas? 24/7 ac?k.
VPN’siz erisim, tek t?kla kay?t > 20 saniyede haz?r.
Kazanmay? dene!”
Форум AntiNarcoForum — место, где зависимые и их близкие могут анонимно получить помощь профессионалов и участников сообщества. Здесь обсуждаются эффективные методы лечения зависимостей, личные истории успеха и конкретные советы по выходу из сложных ситуаций.
Подробнее можно узнать тут – [url=https://antinarcoforum.ru/narkozavisimost/]что такое наркозависимость[/url]
Форум AntiNarcoForum — место, где зависимые и их близкие могут анонимно получить помощь профессионалов и участников сообщества. Здесь обсуждаются эффективные методы лечения зависимостей, личные истории успеха и конкретные советы по выходу из сложных ситуаций.
Получить дополнительные сведения – [url=https://antinarcoforum.ru/narkozavisimost/kak-formiruetsya-narkoticheskaya-zavisimost-razbor-psihologicheskih-i-biologicheskih-mehanizmov/]формирование наркотической зависимости[/url]
автоломбард залог птс
infoavtolombard-pts65.ru/kemerovo.html
займ под птс кемерово
goobet
goobet
автоломбард новосибирск под залог птс в новосибирске
infoavtolombard-pts65.ru/nsk.html
автоломбард залог
goobet
goobet
Врач уточняет продолжительность запоя, характер употребляемого алкоголя и наличие сопутствующих заболеваний. Детальное обследование позволяет оперативно подобрать необходимые медикаменты и минимизировать риск осложнений.
Выяснить больше – [url=https://kapelnica-ot-zapoya-tyumen00.ru/]капельница от запоя стоимость в тюмени[/url]
goobet
После первичной диагностики начинается активная фаза детоксикации. Современные препараты вводятся капельничным методом, что позволяет быстро снизить концентрацию токсинов в крови и восстановить нормальные обменные процессы. Этот этап является основополагающим для стабилизации работы внутренних органов, таких как печень, почки и сердце.
Подробнее можно узнать тут – https://kapelnica-ot-zapoya-tyumen00.ru/postavit-kapelniczu-ot-zapoya-tyumen
Want smarter swaps? Jupiter AI?style routing gives best outcomes.
https://the-jupiter-app.com/
Выезд врача-нарколога из клиники «ТрезвоПрофи» на дом происходит в любое время суток, включая выходные и праздники. Перед началом детоксикации врач проводит осмотр, измеряет давление, частоту пульса, уровень кислорода в крови и подбирает индивидуальную схему лечения. Сама процедура обычно занимает от 1 до 2 часов и проводится под строгим контролем врача.
Получить дополнительные сведения – https://kapelnica-ot-zapoya-sochi00.ru
При длительном запое в организме накапливаются вредные токсины, что ведёт к нарушениям работы сердца, печени, почек и других жизненно важных органов. Чем быстрее начинается терапия, тем выше шансы избежать серьёзных осложнений и обеспечить качественное восстановление. Метод капельничного лечения позволяет оперативно начать детоксикацию, что особенно важно для спасения жизни и предупреждения хронических последствий злоупотребления алкоголем.
Исследовать вопрос подробнее – http://kapelnica-ot-zapoya-tyumen00.ru
goobet
Автогид https://avtogid.in.ua автомобильный украинский портал с новостями, обзорами, советами для автовладельцев
Выезд врача-нарколога из клиники «ТрезвоПрофи» на дом происходит в любое время суток, включая выходные и праздники. Перед началом детоксикации врач проводит осмотр, измеряет давление, частоту пульса, уровень кислорода в крови и подбирает индивидуальную схему лечения. Сама процедура обычно занимает от 1 до 2 часов и проводится под строгим контролем врача.
Углубиться в тему – http://kapelnica-ot-zapoya-sochi00.ru/kapelnicza-ot-zapoya-czena-sochi/
AntiNarcoForum — это онлайн-форум, созданный для тех, кто столкнулся с проблемой алкоголизма или наркомании. Анонимность, индивидуальный подход к каждому пользователю и квалифицированная поддержка делают форум эффективным инструментом в борьбе с зависимостью.
Узнать больше – [url=https://antinarcoforum.ru/reabilitaczionnye-czentry/]наркологическая реабилитация центр[/url]
автоломбард авто
infoavtolombard-pts65.ru
где взять кредит под залог авто
деньги под птс автоломбард
plus-avtolombard-pts65.ru/ekb.html
кредит под залог птс авто
После процедуры пациент чувствует значительное облегчение состояния, улучшение самочувствия и снижение тяги к алкоголю.
Узнать больше – https://kapelnica-ot-zapoya-sochi00.ru/kapelnicza-ot-zapoya-czena-sochi
Алкогольная и наркотическая зависимость являются серьёзными заболеваниями, требующими оперативного и квалифицированного вмешательства. Когда речь идёт о критическом состоянии пациента, особенно после длительного употребления алкоголя или наркотических веществ, время играет ключевую роль. Клиника «РеабилитАльянс» в Краснодаре предлагает услугу нарколога на дом, обеспечивая пациентам необходимую помощь в любой момент дня и ночи. Наши специалисты готовы оперативно выехать по указанному адресу и предоставить все необходимые медицинские процедуры на месте.
Подробнее тут – http://narcolog-na-dom-krasnodar00.ru
AntiNarcoForum — анонимное сообщество помощи людям, страдающим от алкогольной, наркотической и игровой зависимости. На платформе доступны истории выздоровления, консультации специалистов, а также постоянная поддержка от людей, преодолевших схожие трудности.
Подробнее можно узнать тут – [url=https://antinarcoforum.ru/]www.antinarcoforum.ru[/url]
https://nbj.ru/publs/kreditovanie_dlya_obsledovaniya_i_lecheniya/69387/
Платформа AntiNarcoForum объединяет людей, нуждающихся в анонимной и квалифицированной помощи при игровой, алкогольной или наркотической зависимости. Форум предоставляет возможность получить консультации от специалистов и пообщаться с людьми, успешно справившимися с аналогичными проблемами.
Подробнее тут – [url=https://antinarcoforum.ru/rodstvenniki-i-blizkie-zavisimyh/]созависимые отношения это в психологии[/url]
goobet
После процедуры пациент чувствует значительное облегчение состояния, улучшение самочувствия и снижение тяги к алкоголю.
Углубиться в тему – [url=https://kapelnica-ot-zapoya-sochi00.ru/]вызвать капельницу от запоя сочи[/url]
Looking for peer support during detox or rehab? Check out this active recovery forum.
Read more – [url=https://forum4rehab.com/viewforum.php?f=20]anonymous alcohol recovery forum[/url]
бухучет контрольная https://kontrolnyestatistika.ru/
goobet
goobet
Платформа AntiNarcoForum объединяет людей, нуждающихся в анонимной и квалифицированной помощи при игровой, алкогольной или наркотической зависимости. Форум предоставляет возможность получить консультации от специалистов и пообщаться с людьми, успешно справившимися с аналогичными проблемами.
Узнать больше – [url=https://antinarcoforum.ru/rodstvenniki-i-blizkie-zavisimyh/kak-sohranit-semyu-kogda-v-nej-zavisimyj/]влияние алкоголизма на семью[/url]
автоломбард под птс в казани
plus-avtolombard-pts65.ru/kazan.html
деньги под залог авто в казани
деньги под залог авто
infoavtolombard-pts65.ru/nsk.html
кредит под залог авто с плохой кредитной
Families and friends of addicts can share their experiences and find help here.
View details – [url=https://forum4rehab.com/viewforum.php?f=28]co-occurring disorders forum[/url]
“Merhaba forum ahalisi!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://rolletto2025.com/]24/7 canl? destek[/url]
Rulet masas? 24/7 ac?k.
VPN’siz erisim, tek t?kla kay?t > 20 saniyede haz?r.
Simdi dene!”
Капельница от запоя — это комплексная процедура, направленная на быстрое выведение токсинов, нормализацию обменных процессов и восстановление жизненно важных функций организма. Врачи-наркологи подбирают индивидуальный состав капельницы, исходя из состояния пациента. В стандартный набор препаратов обычно входят:
Получить дополнительные сведения – [url=https://kapelnica-ot-zapoya-sochi00.ru/]капельница от запоя наркология[/url]
Рекомендую услуги проверенных хакеров. Обращался, сделали все быстро и качественно – [url=xakervip.com]Программисты хакеры форум[/url] .
goobet
Портал Киева https://u-misti.kyiv.ua новости и события в Киеве сегодня.
goobet
Чем раньше будет проведена процедура детоксикации, тем выше шансы избежать осложнений и быстрее восстановить здоровье пациента. Врачи клиники «ТрезвоПрофи» оперативно реагируют на вызовы, выезжая в любой район Сочи и прилегающие населенные пункты.
Получить дополнительные сведения – [url=https://kapelnica-ot-zapoya-sochi00.ru/]капельница от запоя краснодарский край[/url]
Выбор капельничного метода в условиях домашнего лечения обладает рядом преимуществ:
Углубиться в тему – http://kapelnica-ot-zapoya-tyumen00.ru/kapelnicza-ot-zapoya-na-domu-czena-tyumen/
¡Hola, descubridores de oportunidades !
casinosextranjerosdeespana.es – sin censura – https://casinosextranjerosdeespana.es/# casinos extranjeros
¡Que vivas increíbles instantes únicos !
Как накрутить подписчиков в Likee 2025 [url=https://www.cossa.ru/niksolovov/336871/] Как накрутить подписчиков в Likee[/url]
взять деньги под залог авто
plus-avtolombard-pts65.ru/ekb.html
займ по залог авто
Форум AntiNarcoForum — место, где зависимые и их близкие могут анонимно получить помощь профессионалов и участников сообщества. Здесь обсуждаются эффективные методы лечения зависимостей, личные истории успеха и конкретные советы по выходу из сложных ситуаций.
Подробнее тут – [url=https://antinarcoforum.ru/alkogolizm/sovremennye-metody-lecheniya-alkogolizma-plyusy-i-minusy/]методы лечения алкоголизма[/url]
После процедуры пациент чувствует значительное облегчение состояния, улучшение самочувствия и снижение тяги к алкоголю.
Получить дополнительные сведения – [url=https://kapelnica-ot-zapoya-sochi00.ru/]капельница от запоя цена в сочи[/url]
мп3 новинки [url=https://muzmo-ru.su/]мп3 новинки[/url] .
Оформиление дипломов ВУЗов в Москве — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы даем гарантию, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 4884 клиентов воспользовались услугой — теперь ваша очередь.
[url=http://inforepetitor5.ru/]Мы поможем[/url] — ответим быстро, без лишних формальностей.
Платформа AntiNarcoForum объединяет людей, нуждающихся в анонимной и квалифицированной помощи при игровой, алкогольной или наркотической зависимости. Форум предоставляет возможность получить консультации от специалистов и пообщаться с людьми, успешно справившимися с аналогичными проблемами.
Узнать больше – [url=https://antinarcoforum.ru/reabilitaczionnye-czentry/chto-proishodit-v-czentre-reabilitaczii/]деятельность реабилитационного центра[/url]
машина под залог
plus-avtolombard-pts65.ru
деньги в залог авто
При длительном запое в организме накапливаются вредные токсины, что ведёт к нарушениям работы сердца, печени, почек и других жизненно важных органов. Чем быстрее начинается терапия, тем выше шансы избежать серьёзных осложнений и обеспечить качественное восстановление. Метод капельничного лечения позволяет оперативно начать детоксикацию, что особенно важно для спасения жизни и предупреждения хронических последствий злоупотребления алкоголем.
Ознакомиться с деталями – [url=https://kapelnica-ot-zapoya-tyumen00.ru/]kapelnica ot zapoya tjumen'[/url]
Выезд врача-нарколога из клиники «ТрезвоПрофи» на дом происходит в любое время суток, включая выходные и праздники. Перед началом детоксикации врач проводит осмотр, измеряет давление, частоту пульса, уровень кислорода в крови и подбирает индивидуальную схему лечения. Сама процедура обычно занимает от 1 до 2 часов и проводится под строгим контролем врача.
Ознакомиться с деталями – [url=https://kapelnica-ot-zapoya-sochi00.ru/]врач на дом капельница от запоя[/url]
Рекомендую услуги проверенных хакеров. Обращался, сделали все быстро и качественно – [url=xakervip.com]Как найти настоящих хакеров[/url] .
кредит под залог птс казань
plus-avtolombard-pts65.ru/kazan.html
кредит под птс авто
Когда запой превращается в угрозу для жизни, оперативное вмешательство становится критически важным. В Тюмени, Тюменская область, опытные наркологи предлагают услугу установки капельницы от запоя прямо на дому. Такой метод позволяет начать детоксикацию с использованием современных медикаментов, что способствует быстрому выведению токсинов, восстановлению обменных процессов и нормализации работы внутренних органов. Лечение на дому обеспечивает комфортную обстановку, полную конфиденциальность и индивидуальный подход к каждому пациенту.
Углубиться в тему – http://kapelnica-ot-zapoya-tyumen00.ru/
скачать музыку бесплатно в хорошем качестве без регистрации на телефон с прослушиванием русские все [url=https://muzmo-ru.su/]скачать музыку бесплатно в хорошем качестве без регистрации на телефон с прослушиванием русские все[/url] .
Попробуйте https://www.vrentals.co.za/hello-world-2/
Оформиление дипломов ВУЗов по всей России и СНГ — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы даем гарантию, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 3194 клиентов воспользовались услугой — теперь ваша очередь.
[url=http://spbrcom6.ru/]Доступ по ссылке[/url] — ответим быстро, без лишних формальностей.
займ под залог авто круглосуточно
plus-avtolombard-pts65.ru/nsk.html
займ под залог авто по стс
You’re not alone. Connect with others who understand what addiction recovery really takes.
Get more information – [url=https://forum4rehab.com/viewforum.php?f=30]living with an addict forum[/url]
AntiNarcoForum — это онлайн-форум, созданный для тех, кто столкнулся с проблемой алкоголизма или наркомании. Анонимность, индивидуальный подход к каждому пользователю и квалифицированная поддержка делают форум эффективным инструментом в борьбе с зависимостью.
Выяснить больше – [url=https://antinarcoforum.ru/narkozavisimost/]виды наркотической зависимости[/url]
Комплексное лечение организовано по строго отлаженной схеме, которая включает несколько последовательных этапов, позволяющих обеспечить оперативное и безопасное восстановление организма.
Детальнее – [url=https://kapelnica-ot-zapoya-tyumen00.ru/]капельница от запоя тюменская область[/url]
A helpful resource for anyone facing substance abuse, dual diagnosis, or post-rehab life.
Explore more – [url=https://forum4rehab.com/viewforum.php?f=28]bipolar and drug addiction forum[/url]
контрольные под заказ купить контрольную работу экология
дипломные работы на заказ диплом сделать
сделать отчет по практике на заказ заказать отчет по практике производственной
взять микрозайм https://zajmy-onlajn.ru
Заказывал услуги проверенного хакера. КОНТАКТЫ СПЕЦИАЛИСТА:
Xa*******@********il.com
Рекомендую [url=xakerforum.com/topic/282/page-12]xakerforum.com/topic/282/page-12[/url] .
Когда запой превращается в угрозу для жизни, оперативное вмешательство становится критически важным. В Тюмени, Тюменская область, опытные наркологи предлагают услугу установки капельницы от запоя прямо на дому. Такой метод позволяет начать детоксикацию с использованием современных медикаментов, что способствует быстрому выведению токсинов, восстановлению обменных процессов и нормализации работы внутренних органов. Лечение на дому обеспечивает комфортную обстановку, полную конфиденциальность и индивидуальный подход к каждому пациенту.
Изучить вопрос глубже – https://kapelnica-ot-zapoya-tyumen00.ru/kapelnicza-ot-zapoya-na-domu-czena-tyumen/
После завершения процедур врач дает пациенту и его родственникам подробные рекомендации по дальнейшему восстановлению и профилактике рецидивов.
Ознакомиться с деталями – https://narcolog-na-dom-krasnodar00.ru/vyzov-narkologa-na-dom-krasnodar/
I savor, result in I discovered just what I was having a look for. You have ended my 4 day lengthy hunt! God Bless you man. Have a nice day. Bye
Child Porn
Накрутка подписчиков в Телеграм 2025 [url=https://www.cossa.ru/niksolovov/339510/] Накрутка подписчиков в Телеграм[/url]
Когда запой превращается в угрозу для жизни, оперативное вмешательство становится критически важным. В Тюмени, Тюменская область, опытные наркологи предлагают услугу установки капельницы от запоя прямо на дому. Такой метод позволяет начать детоксикацию с использованием современных медикаментов, что способствует быстрому выведению токсинов, восстановлению обменных процессов и нормализации работы внутренних органов. Лечение на дому обеспечивает комфортную обстановку, полную конфиденциальность и индивидуальный подход к каждому пациенту.
Выяснить больше – [url=https://kapelnica-ot-zapoya-tyumen00.ru/]капельница от запоя в тюмени[/url]
“Dikkat kazanc avc?lar?!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://radissonbet2025.com/]simdi dene[/url]
Canl? bahis yuksek oranl?.
VPN’siz erisim, tek t?kla kay?t > 20 saniyede haz?r.
Sans?n? art?r!”
Алкогольная и наркотическая зависимость являются серьёзными заболеваниями, требующими оперативного и квалифицированного вмешательства. Когда речь идёт о критическом состоянии пациента, особенно после длительного употребления алкоголя или наркотических веществ, время играет ключевую роль. Клиника «РеабилитАльянс» в Краснодаре предлагает услугу нарколога на дом, обеспечивая пациентам необходимую помощь в любой момент дня и ночи. Наши специалисты готовы оперативно выехать по указанному адресу и предоставить все необходимые медицинские процедуры на месте.
Получить дополнительные сведения – [url=https://narcolog-na-dom-krasnodar00.ru/]нарколог на дом в краснодаре[/url]
После процедуры пациент чувствует значительное облегчение состояния, улучшение самочувствия и снижение тяги к алкоголю.
Получить дополнительную информацию – [url=https://kapelnica-ot-zapoya-sochi00.ru/]капельница от запоя клиника в сочи[/url]
кредит под птс с плохой кредитной историей
plus-avtolombard-pts65.ru
быстро деньги под птс
¡Saludos, descubridores de tesoros!
casino online fuera de EspaГ±a sin KYC obligatorio – https://www.casinosonlinefueraespanol.xyz/# casino por fuera
¡Que disfrutes de recompensas asombrosas !
AntiNarcoForum — форум помощи при зависимостях, обеспечивающий анонимность и поддержку каждому участнику. Здесь доступны проверенные методики лечения, реальные истории выздоровления и профессиональные рекомендации специалистов для эффективного преодоления зависимости.
Подробнее тут – [url=https://antinarcoforum.ru/rodstvenniki-i-blizkie-zavisimyh/sozavisimost-kogda-spasaya-my-teryaem-sebya/]зависимость и созависимость это[/url]
Экстренная установка капельницы необходима, если пациент находится в состоянии запоя более 2–3 дней или испытывает симптомы тяжелой интоксикации алкоголем:
Выяснить больше – http://
Попробуйте https://www.glamuroes.ch/1501165_vk-1/
займ под птс авто
proavtolombard-pts65.ru/kemerovo.html
кредит под птс автомобиля
Book affordable and professional AC duct cleaning services in Dubai for your villa or apartment https://ac-cleaning-dubai.ae/
рулонные шторы Римские шторы – это элегантность и изысканность в каждой складке. Они идеально подходят для небольших помещений, где важен каждый сантиметр пространства. Пластиковые шторы
Заказывал услуги проверенного хакера. КОНТАКТЫ СПЕЦИАЛИСТА:
Xa*******@********il.com
Рекомендую [url=xakerforum.com/topic/282/page-2]xakerforum.com/topic/282/page-2[/url] .
При длительном запое в организме накапливаются вредные токсины, что ведёт к нарушениям работы сердца, печени, почек и других жизненно важных органов. Чем быстрее начинается терапия, тем выше шансы избежать серьёзных осложнений и обеспечить качественное восстановление. Метод капельничного лечения позволяет оперативно начать детоксикацию, что особенно важно для спасения жизни и предупреждения хронических последствий злоупотребления алкоголем.
Подробнее – http://kapelnica-ot-zapoya-tyumen00.ru/
Форум AntiNarcoForum — место, где зависимые и их близкие могут анонимно получить помощь профессионалов и участников сообщества. Здесь обсуждаются эффективные методы лечения зависимостей, личные истории успеха и конкретные советы по выходу из сложных ситуаций.
Подробнее – [url=https://antinarcoforum.ru/rodstvenniki-i-blizkie-zavisimyh/nuzhno-li-stavit-ultimatum-sovety-psihologov/]советы психолога что делать[/url]
займ под птс без авто
proavtolombard-pts65.ru
займ под залог птс москва
После процедуры пациент чувствует значительное облегчение состояния, улучшение самочувствия и снижение тяги к алкоголю.
Получить дополнительные сведения – http://kapelnica-ot-zapoya-sochi00.ru/
Сайт Житомир https://u-misti.zhitomir.ua новости и происшествия в Житомире и области
¡Hola, jugadores expertos !
casinosextranjerosdeespana.es – juegos premiados – https://www.casinosextranjerosdeespana.es/# casino online extranjero
¡Que vivas increíbles jackpots sorprendentes!
автоломбард под птс
proavtolombard-pts65.ru/ekb.html
ломбард деньги под залог птс
Когда запой превращается в угрозу для жизни, оперативное вмешательство становится критически важным. В Тюмени, Тюменская область, опытные наркологи предлагают услугу установки капельницы от запоя прямо на дому. Такой метод позволяет начать детоксикацию с использованием современных медикаментов, что способствует быстрому выведению токсинов, восстановлению обменных процессов и нормализации работы внутренних органов. Лечение на дому обеспечивает комфортную обстановку, полную конфиденциальность и индивидуальный подход к каждому пациенту.
Получить дополнительные сведения – [url=https://kapelnica-ot-zapoya-tyumen00.ru/]капельницу от запоя тюмень[/url]
Своевременное обращение к специалисту позволяет избежать опасных осложнений и облегчить процесс восстановления организма. Экстренный вызов врача-нарколога необходим в следующих случаях:
Выяснить больше – [url=https://narcolog-na-dom-krasnodar00.ru/]нарколог на дом срочно[/url]
деньги под птс автомобиля новосибирск
proavtolombard-pts65.ru/nsk.html
займ под залог птс автомобиля
Процедура выезда врача на дом в Краснодаре строго регламентирована и включает несколько последовательных этапов. После поступления звонка и уточнения подробностей состояния пациента врач выезжает на место в течение 30–60 минут. На месте проводится первичный осмотр с оценкой жизненно важных показателей: артериального давления, уровня кислорода в крови, сердечного ритма и степени общей интоксикации.
Разобраться лучше – [url=https://narcolog-na-dom-krasnodar00.ru/]вызов нарколога на дом краснодар.[/url]
Женский блог https://zhinka.in.ua Жінка это самое интересное о красоте, здоровье, отношениях. Много полезной информации для женщин.
¡Bienvenidos, buscadores de fortuna !
Casino fuera de EspaГ±a con juegos de proveedores top – п»їhttps://casinofueraespanol.xyz/ casino por fuera
¡Que vivas increíbles botes deslumbrantes!
какой сайт фишинговый Фишинговый сайт банка имитирует официальный сайт банка и пытается украсть ваши данные для доступа к вашему банковскому счету. Как отличить фишинговый сайт
деньги под залог авто птс
proavtolombard-pts65.ru/kazan.html
срочный кредит под залог птс
Выезд врача-нарколога из клиники «ТрезвоПрофи» на дом происходит в любое время суток, включая выходные и праздники. Перед началом детоксикации врач проводит осмотр, измеряет давление, частоту пульса, уровень кислорода в крови и подбирает индивидуальную схему лечения. Сама процедура обычно занимает от 1 до 2 часов и проводится под строгим контролем врача.
Получить больше информации – [url=https://kapelnica-ot-zapoya-sochi00.ru/]капельница от запоя вызов в сочи[/url]
Book affordable and professional AC duct cleaning services in Dubai for your villa or apartment: ac unit cleaning cost
su kaçağı bulma Kaçağı bulduktan sonra tamir için de yardımcı oldular. https://twanty2.com/read-blog/13839
Экстренная установка капельницы необходима, если пациент находится в состоянии запоя более 2–3 дней или испытывает симптомы тяжелой интоксикации алкоголем:
Выяснить больше – [url=https://kapelnica-ot-zapoya-sochi00.ru/]после капельницы от запоя в сочи[/url]
отзывы [url=https://niksolovov.ru/services/ediagent]https://niksolovov.ru/services/ediagent[/url] 2025
При длительном запое в организме накапливаются вредные токсины, что ведёт к нарушениям работы сердца, печени, почек и других жизненно важных органов. Чем быстрее начинается терапия, тем выше шансы избежать серьёзных осложнений и обеспечить качественное восстановление. Метод капельничного лечения позволяет оперативно начать детоксикацию, что особенно важно для спасения жизни и предупреждения хронических последствий злоупотребления алкоголем.
Подробнее – http://
варфейс аккаунты купить Приобретение аккаунта Warface – это возможность сэкономить время и силы, получив готового персонажа с прокачанными навыками и экипировкой. Аккаунт Варфейс купить
Когда запой превращается в угрозу для жизни, оперативное вмешательство становится критически важным. В Тюмени, Тюменская область, опытные наркологи предлагают услугу установки капельницы от запоя прямо на дому. Такой метод позволяет начать детоксикацию с использованием современных медикаментов, что способствует быстрому выведению токсинов, восстановлению обменных процессов и нормализации работы внутренних органов. Лечение на дому обеспечивает комфортную обстановку, полную конфиденциальность и индивидуальный подход к каждому пациенту.
Исследовать вопрос подробнее – [url=https://kapelnica-ot-zapoya-tyumen00.ru/]капельница от запоя на дому тюмень[/url]
Выезд врача-нарколога из клиники «ТрезвоПрофи» на дом происходит в любое время суток, включая выходные и праздники. Перед началом детоксикации врач проводит осмотр, измеряет давление, частоту пульса, уровень кислорода в крови и подбирает индивидуальную схему лечения. Сама процедура обычно занимает от 1 до 2 часов и проводится под строгим контролем врача.
Ознакомиться с деталями – [url=https://kapelnica-ot-zapoya-sochi00.ru/]вызвать капельницу от запоя на дому сочи[/url]
AntiNarcoForum — анонимное сообщество помощи людям, страдающим от алкогольной, наркотической и игровой зависимости. На платформе доступны истории выздоровления, консультации специалистов, а также постоянная поддержка от людей, преодолевших схожие трудности.
Детальнее – [url=https://antinarcoforum.ru/rodstvenniki-i-blizkie-zavisimyh/kak-razgovarivat-s-zavisimym-chtoby-on-uslyshal/]как говорить с зависимым[/url]
Как сделать потолок Натяжные потолки со светильниками – это функциональное и стильное решение для любого интерьера. Какой натяжной потолок
краснодар аренда авто Аренда авто без залога: Путешествуйте без финансовых ограничений. Мы предлагаем прозрачные условия аренды, чтобы ничто не омрачало вашу поездку.
Комплексное лечение организовано по строго отлаженной схеме, которая включает несколько последовательных этапов, позволяющих обеспечить оперативное и безопасное восстановление организма.
Выяснить больше – https://kapelnica-ot-zapoya-tyumen00.ru/kapelnicza-ot-zapoya-na-domu-tyumen
Выезд врача-нарколога из клиники «ТрезвоПрофи» на дом происходит в любое время суток, включая выходные и праздники. Перед началом детоксикации врач проводит осмотр, измеряет давление, частоту пульса, уровень кислорода в крови и подбирает индивидуальную схему лечения. Сама процедура обычно занимает от 1 до 2 часов и проводится под строгим контролем врача.
Ознакомиться с деталями – [url=https://kapelnica-ot-zapoya-sochi00.ru/]posle-kapelniczy-ot-zapoya sochi[/url]
После процедуры пациент чувствует значительное облегчение состояния, улучшение самочувствия и снижение тяги к алкоголю.
Получить больше информации – [url=https://kapelnica-ot-zapoya-sochi00.ru/]капельница от запоя анонимно в сочи[/url]
Платформа AntiNarcoForum объединяет людей, нуждающихся в анонимной и квалифицированной помощи при игровой, алкогольной или наркотической зависимости. Форум предоставляет возможность получить консультации от специалистов и пообщаться с людьми, успешно справившимися с аналогичными проблемами.
Получить больше информации – [url=https://antinarcoforum.ru/alkogolizm/]синдром алкоголизма это[/url]
Бездепозитный бонус Казино, предлагающие бездепозитные бонусы, словно заботливые хозяева, приглашают гостей в свой дом и предлагают им угощение на пробу. Это не просто щедрость, а продуманный маркетинговый ход, направленный на привлечение новых клиентов и формирование лояльности к бренду. Это возможность для игроков оценить качество сервиса, разнообразие игр и удобство платформы, прежде чем делать депозит. Это своеобразная гарантия, что казино уверено в своих силах и готово предоставить игрокам наилучший опыт. Бездепозитный бонус
Капельница от запоя — это комплексная процедура, направленная на быстрое выведение токсинов, нормализацию обменных процессов и восстановление жизненно важных функций организма. Врачи-наркологи подбирают индивидуальный состав капельницы, исходя из состояния пациента. В стандартный набор препаратов обычно входят:
Подробнее можно узнать тут – [url=https://kapelnica-ot-zapoya-sochi00.ru/]kapelnicza-ot-zapoya-na-domu sochi[/url]
Аренда авто без залога Аренда авто в Краснодаре: Широкий выбор автомобилей для любых целей и задач. Деловая поездка, семейный отдых или просто комфортное передвижение по городу – у нас найдется подходящий автомобиль для вас.
Натяжные потолки Люберцы Потолки помещений – это важный элемент интерьера, влияющий на общее впечатление от комнаты. Потолок
Работаем круглосуточно и без выходных.
Мы предоставляем качественный ремонт на дому.
Алкогольная и наркотическая зависимость являются серьёзными заболеваниями, требующими оперативного и квалифицированного вмешательства. Когда речь идёт о критическом состоянии пациента, особенно после длительного употребления алкоголя или наркотических веществ, время играет ключевую роль. Клиника «РеабилитАльянс» в Краснодаре предлагает услугу нарколога на дом, обеспечивая пациентам необходимую помощь в любой момент дня и ночи. Наши специалисты готовы оперативно выехать по указанному адресу и предоставить все необходимые медицинские процедуры на месте.
Подробнее – [url=https://narcolog-na-dom-krasnodar00.ru/]нарколог на дом анонимно краснодар[/url]
автоломбард москва
proavtolombard-pts65.ru
автоломбард залог авто
Кондиционер https://brand-climat.ru разные типы для охлаждения и обогрева. Профессиональная помощь в выборе, установка под ключ, сервисное обслуживание и гарантия. Создайте комфортный микроклимат круглый год!
AntiNarcoForum — форум помощи при зависимостях, обеспечивающий анонимность и поддержку каждому участнику. Здесь доступны проверенные методики лечения, реальные истории выздоровления и профессиональные рекомендации специалистов для эффективного преодоления зависимости.
Выяснить больше – [url=https://antinarcoforum.ru/alkogolizm/sovremennye-metody-lecheniya-alkogolizma-plyusy-i-minusy/]современные методы лечения алкоголизма какие лучше[/url]
1000 рублей за регистрацию вывод сразу 1000 рублей без депозита
Предлагаю https://musicstudio.koo.net.au/2023/10/08/hello-world/
Форум AntiNarcoForum — место, где зависимые и их близкие могут анонимно получить помощь профессионалов и участников сообщества. Здесь обсуждаются эффективные методы лечения зависимостей, личные истории успеха и конкретные советы по выходу из сложных ситуаций.
Изучить вопрос глубже – https://antinarcoforum.ru/rodstvenniki-i-blizkie-zavisimyh/kak-razgovarivat-s-zavisimym-chtoby-on-uslyshal/
кредит под залог птс грузового
zaimpod-pts89.ru
автоломбард под авто
¡Bienvenidos, aventureros de la fortuna !
Casino por fuera con apuestas en deportes en directo – https://www.casinofueraespanol.xyz/ casinofueraespanol
¡Que vivas increíbles rondas emocionantes !
отзывы [url=https://niksolovov.ru/services/socfishing]https://niksolovov.ru/services/socfishing[/url] 2025
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Получить дополнительную информацию – https://body-phaze.com/helpie_faq/yours-first-faq-question
Этот информативный текст выделяется своими захватывающими аспектами, которые делают сложные темы доступными и понятными. Мы стремимся предложить читателям глубину знаний вместе с разнообразием интересных фактов. Откройте новые горизонты и развивайте свои способности познавать мир!
Углубиться в тему – https://gmd.center/2017/06/30/yak-kupyty-palne-z-porushennyamy-lajfhak-vid-yavorivskoyi-rda
Неожиданное обвинение против Анджелины Джоли в связи с Брэдом Питтом
https://x.com/Fariz418740/status/1937032982834897246
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Ознакомиться с деталями – https://perfectindiaplanner.in/how-to-travel-with-paper-map
Этот информативный текст сочетает в себе темы здоровья и зависимости. Мы обсудим, как хронические заболевания могут усугубить зависимости и наоборот, как зависимость может влиять на общее состояние здоровья. Читатели получат представление о комплексном подходе к лечению как физического, так и психического состояния.
Детальнее – https://2prishi.ru/priznaki-peredozirovki-narkotikami
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Узнать больше – https://banglachatbot.com/how-can-i-increase-my-facebook-likes-automatically
В этом обзорном материале представлены увлекательные детали, которые находят отражение в различных аспектах жизни. Мы исследуем непонятные и интересные моменты, позволяя читателю увидеть картину целиком. Погрузитесь в мир знаний и удивительных открытий!
Подробнее тут – https://karriere-azv-offenburg.de/hello-world
porno pics milf
В условиях стационара или на дневном стационаре применяются сбалансированные инфузионные растворы, витамины, антиоксиданты и препараты для поддержки печени. Цель — минимизировать интоксикацию и предотвратить осложнения.
Выяснить больше – [url=https://lechenie-alkogolizma-tyumen10.ru/]лечение алкоголизма тюменская область[/url]
Обращение за медицинской помощью становится необходимым, когда пациент пребывает в состоянии, требующем немедленного вмешательства, так как самостоятельное лечение может только усугубить ситуацию. Это происходит, если запой продолжается несколько дней, и организм не успевает справляться с накопившимися токсинами, что ведёт к нарушению работы внутренних органов. Если у пациента регулярно наблюдаются симптомы, такие как частая рвота, сильное головокружение, спутанность сознания, судороги или резкие колебания артериального давления, это является явным сигналом к вызову специалиста. Особенно важно обращаться за помощью при выраженных признаках абстинентного синдрома, когда сильная дрожь, панические атаки, бессонница, тревожность и даже галлюцинации свидетельствуют о том, что организм испытывает критическую нехватку поддержки. Наличие психических нарушений, таких как агрессивное поведение, спутанность сознания или признаки алкогольного психоза, также требует незамедлительного вмешательства. В таких ситуациях обращение за профессиональной помощью помогает быстро стабилизировать состояние пациента, предотвратить развитие тяжелых осложнений и сохранить жизнь.
Получить дополнительные сведения – [url=https://narcolog-na-dom-ekaterinburg00.ru/]запой нарколог на дом в екатеринбурге[/url]
Украинский бизнес https://in-ukraine.biz.ua информацинный портал о бизнесе, финансах, налогах, своем деле в Украине
¡Saludos, seguidores del desafío !
Mejores casinos online extranjeros con interfaz moderna – https://www.casinoextranjerosdeespana.es/# п»їcasinos online extranjeros
¡Que experimentes maravillosas premios excepcionales !
Для каждого пациента используется индивидуальный монитор жизненно важных функций, передающий данные врачу в клинике через защищённый канал связи. Это обеспечивает безопасность при лечении как лёгких, так и тяжёлых форм интоксикации, снижая вероятность осложнений.
Получить дополнительную информацию – [url=https://narkologicheskaya-klinika-tyumen10.ru/]наркологическая клиника в тюмени[/url]
Служба выезда «ТюменьМед» функционирует 24/7, что позволяет незамедлительно реагировать на срочные вызовы. В распоряжении клиники — собственный автопарк с санитарными машинами, оснащёнными всем необходимым для проведения инфузионной терапии на дому. При экстренном вызове врач прибывает к пациенту в пределах города в течение 30–60 минут.
Выяснить больше – [url=https://narkologicheskaya-klinika-tyumen10.ru/]наркологическая клиника тюмень.[/url]
Преимущество
Получить дополнительные сведения – http://narcolog-na-dom-ekaterinburg0.ru/
В условиях стационара или на дневном стационаре применяются сбалансированные инфузионные растворы, витамины, антиоксиданты и препараты для поддержки печени. Цель — минимизировать интоксикацию и предотвратить осложнения.
Разобраться лучше – [url=https://lechenie-alkogolizma-tyumen10.ru/]клиника лечения алкоголизма в тюмени[/url]
Наркологическая помощь «ТюменьМед» не ограничивается только физической детоксикацией. В состав команды входят психологи и социальные работники, которые проводят мотивационные беседы, обучают навыкам самоконтроля и оказывают помощь в планировании досуга и социальных активностей после детоксикации.
Подробнее можно узнать тут – [url=https://narkologicheskaya-klinika-tyumen10.ru/]наркологическая клиника цены тюмень[/url]
взять кредит под залог автомобиля
zaimpod-pts89.ru/kazan.html
займ под залог птс
где взять кредит под птс
zaimpod-pts89.ru/nsk.html
кредит под залог авто без подтверждения дохода
Обращение к врачу становится жизненно необходимым, если пациент находится в состоянии длительного запоя, при котором организм не справляется с накоплением токсинов. Если запой продолжается более двух-трёх дней, в теле накапливаются вредные вещества, что ведёт к нарушениям работы внутренних органов, развитию абстинентного синдрома и появлению психических нарушений. Также, если у пациента наблюдаются симптомы, такие как частая рвота, спутанность сознания, судороги или резкие скачки артериального давления, это сигнал к незамедлительному вызову специалиста. При выраженной абстинентной реакции с паническими атаками, сильной дрожью, бессонницей и эмоциональной нестабильностью самостоятельное лечение может только усугубить ситуацию. Если появляются признаки алкогольного психоза – галлюцинации, агрессивность или спутанность сознания – вызов нарколога становится обязательным для предотвращения дальнейших осложнений. Также, когда требуется подготовка к процедурам кодирования от зависимости, необходима качественная детоксикация организма, что также является показанием к срочному обращению за профессиональной помощью.
Выяснить больше – [url=https://narcolog-na-dom-ekaterinburg0.ru/]нарколог на дом вывод екатеринбург[/url]
Вызов нарколога на дом необходим в тех случаях, когда состояние человека требует срочного вмешательства врача, а самостоятельно обратиться в стационар нет возможности или желания. Такие ситуации включают сильную алкогольную интоксикацию, затяжные запои, выраженный похмельный синдром, психические расстройства, вызванные употреблением спиртного, и острый абстинентный синдром. Без своевременного лечения эти состояния могут привести к тяжелым осложнениям, таким как инфаркт, инсульт, белая горячка и тяжелое поражение печени. Поэтому при первых признаках ухудшения самочувствия лучше сразу обратиться за помощью к профессионалам.
Углубиться в тему – [url=https://narcolog-na-dom-sochi00.ru/]вызвать нарколога на дом в сочи[/url]
После поступления вызова на дом врачи клиники «Трезвый Путь» проводят лечение по четко разработанному алгоритму, обеспечивающему максимальную эффективность и безопасность:
Получить больше информации – [url=https://narcolog-na-dom-ekaterinburg0.ru/]нарколог на дом екатеринбург.[/url]
Вызов нарколога на дом необходим в тех случаях, когда состояние человека требует срочного вмешательства врача, а самостоятельно обратиться в стационар нет возможности или желания. Такие ситуации включают сильную алкогольную интоксикацию, затяжные запои, выраженный похмельный синдром, психические расстройства, вызванные употреблением спиртного, и острый абстинентный синдром. Без своевременного лечения эти состояния могут привести к тяжелым осложнениям, таким как инфаркт, инсульт, белая горячка и тяжелое поражение печени. Поэтому при первых признаках ухудшения самочувствия лучше сразу обратиться за помощью к профессионалам.
Узнать больше – [url=https://narcolog-na-dom-sochi00.ru/]narkolog-na-dom-czena sochi[/url]
Каждый этап проводится квалифицированным специалистом, что позволяет достичь максимального терапевтического эффекта.
Углубиться в тему – https://narcolog-na-dom-ekaterinburg0.ru/vrach-narkolog-na-dom-ekb/
Вызов нарколога на дом необходим в тех случаях, когда состояние человека требует срочного вмешательства врача, а самостоятельно обратиться в стационар нет возможности или желания. Такие ситуации включают сильную алкогольную интоксикацию, затяжные запои, выраженный похмельный синдром, психические расстройства, вызванные употреблением спиртного, и острый абстинентный синдром. Без своевременного лечения эти состояния могут привести к тяжелым осложнениям, таким как инфаркт, инсульт, белая горячка и тяжелое поражение печени. Поэтому при первых признаках ухудшения самочувствия лучше сразу обратиться за помощью к профессионалам.
Подробнее тут – http://narcolog-na-dom-sochi00.ru
Кроме стандартного вывода из запоя и детоксикации, врач клиники «Реабилитация Плюс» может предложить дополнительные процедуры, направленные на полноценное восстановление пациента:
Получить дополнительную информацию – https://narcolog-na-dom-sochi00.ru/narkolog-na-dom-kruglosutochno-sochi
Преимущество
Разобраться лучше – https://narcolog-na-dom-ekaterinburg0.ru/zapoj-narkolog-na-dom-ekb
Индивидуальный план включает детоксикацию, медикаментозную поддержку, психотерапию и реабилитацию. Специалисты учитывают:
Разобраться лучше – https://lechenie-alkogolizma-tyumen10.ru/anonimnoe-lechenie-alkogolizma-tyumen
Кроме стандартного вывода из запоя и детоксикации, врач клиники «Реабилитация Плюс» может предложить дополнительные процедуры, направленные на полноценное восстановление пациента:
Детальнее – [url=https://narcolog-na-dom-sochi00.ru/]нарколог на дом клиника в сочи[/url]
После поступления вызова на дом врачи клиники «Трезвый Путь» проводят лечение по четко разработанному алгоритму, обеспечивающему максимальную эффективность и безопасность:
Выяснить больше – [url=https://narcolog-na-dom-ekaterinburg0.ru/]нарколог на дом срочно екатеринбург[/url]
Наша команда врачей оперативно реагирует на каждый вызов, оказывая квалифицированную медицинскую помощь на дому. Специалисты проводят полный комплекс лечебных мероприятий, направленных на безопасное снятие интоксикации, детоксикацию и облегчение симптомов абстиненции.
Подробнее тут – [url=https://narcolog-na-dom-ekaterinburg0.ru/]врач нарколог на дом екатеринбург.[/url]
Каждая выездная бригада укомплектована портативным лабораторным оборудованием для экспресс-анализов крови и мочи, современными инфузионными насосами и средствами телеметрии. Это позволяет врачу контролировать жизненно важные параметры пациента в режиме реального времени и корректировать схему детоксикации на месте.
Детальнее – https://narkologicheskaya-klinika-tyumen10.ru
Вызов нарколога на дом необходим в тех случаях, когда состояние человека требует срочного вмешательства врача, а самостоятельно обратиться в стационар нет возможности или желания. Такие ситуации включают сильную алкогольную интоксикацию, затяжные запои, выраженный похмельный синдром, психические расстройства, вызванные употреблением спиртного, и острый абстинентный синдром. Без своевременного лечения эти состояния могут привести к тяжелым осложнениям, таким как инфаркт, инсульт, белая горячка и тяжелое поражение печени. Поэтому при первых признаках ухудшения самочувствия лучше сразу обратиться за помощью к профессионалам.
Углубиться в тему – http://narcolog-na-dom-sochi00.ru
Вызов нарколога на дом необходим в тех случаях, когда состояние человека требует срочного вмешательства врача, а самостоятельно обратиться в стационар нет возможности или желания. Такие ситуации включают сильную алкогольную интоксикацию, затяжные запои, выраженный похмельный синдром, психические расстройства, вызванные употреблением спиртного, и острый абстинентный синдром. Без своевременного лечения эти состояния могут привести к тяжелым осложнениям, таким как инфаркт, инсульт, белая горячка и тяжелое поражение печени. Поэтому при первых признаках ухудшения самочувствия лучше сразу обратиться за помощью к профессионалам.
Выяснить больше – [url=https://narcolog-na-dom-sochi00.ru/]нарколог на дом краснодарский край[/url]
деньги под птс круглосуточные
zaimpod-pts90.ru/ekb.html
автоломбард птс
Служба выезда «ТюменьМед» функционирует 24/7, что позволяет незамедлительно реагировать на срочные вызовы. В распоряжении клиники — собственный автопарк с санитарными машинами, оснащёнными всем необходимым для проведения инфузионной терапии на дому. При экстренном вызове врач прибывает к пациенту в пределах города в течение 30–60 минут.
Разобраться лучше – [url=https://narkologicheskaya-klinika-tyumen10.ru/]наркологическая клиника[/url]
В условиях стационара или на дневном стационаре применяются сбалансированные инфузионные растворы, витамины, антиоксиданты и препараты для поддержки печени. Цель — минимизировать интоксикацию и предотвратить осложнения.
Выяснить больше – [url=https://lechenie-alkogolizma-tyumen10.ru/]клиника лечения алкоголизма тюменская область[/url]
Репетитор по физике https://repetitor-po-fizike-spb.ru СПб: школьникам и студентам, с нуля и для олимпиад. Четкие объяснения, практика, реальные результаты.
автоломбард под залог птс
zaimpod-pts89.ru/kemerovo.html
автоломбард в кемерово под залог
?Hola, fanaticos del entretenimiento !
Casino fuera de EspaГ±a con variedad de juegos online – https://www.casinosonlinefueradeespanol.xyz/ casinosonlinefueradeespanol.xyz
?Que disfrutes de asombrosas momentos irrepetibles !
Алкогольная зависимость — сложное хроническое заболевание, требующее комплексного подхода и квалифицированной помощи. В клинике «Тюменьбезалко» в центре Тюмени разработаны эффективные программы реабилитации, сочетающие современные медицинские методы, психологическую поддержку и социальную адаптацию. Опытные врачи-наркологи и психотерапевты помогают пациентам преодолеть употребление алкоголя, восстановить физическое и эмоциональное здоровье и вернуться к полноценной жизни.
Подробнее можно узнать тут – [url=https://lechenie-alkogolizma-tyumen10.ru/]наркологическое лечение алкоголизма[/url]
Аппаратные методы кодирования включают лазерную терапию и электростимуляцию биологически активных точек, влияющих на центры зависимости в головном мозге. Эти методики способствуют быстрому формированию устойчивого отвращения к спиртному и хорошо переносятся пациентами.
Узнать больше – [url=https://kodirovanie-ot-alkogolizma-odintsovo2.ru/]kodirovanie ot alkogolizma na domu[/url]
Растворы для детоксикации
Подробнее тут – [url=https://narcolog-na-dom-ekaterinburg00.ru/]нарколог на дом недорого[/url]
Алкогольная зависимость — это хроническое заболевание, при котором устойчивое влечение к спиртному приводит к тяжёлым медицинским, социальным и психологическим последствиям. Когда пациент осознаёт, что самостоятельно справиться с этой проблемой не получается, наиболее эффективным методом становится кодирование от алкоголизма. В клинике «Ясное Будущее» в Одинцово мы используем сочетание проверенных методик кодирования и комплексной психологической поддержки, что позволяет достичь стойкой ремиссии и вернуть человеку контроль над собственной жизнью.
Изучить вопрос глубже – [url=https://kodirovanie-ot-alkogolizma-odintsovo2.ru/]kodirovanie ot alkogolizma dovzhenko[/url]
Мы предлагаем оформление дипломов ВУЗов в Москве — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы даем гарантию, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 1524 клиентов воспользовались услугой — теперь ваша очередь.
[url=http://poligraf2.ru/]Здесь[/url] — ответим быстро, без лишних формальностей.
В условиях стационара или на дневном стационаре применяются сбалансированные инфузионные растворы, витамины, антиоксиданты и препараты для поддержки печени. Цель — минимизировать интоксикацию и предотвратить осложнения.
Исследовать вопрос подробнее – [url=https://lechenie-alkogolizma-tyumen10.ru/]www.domen.ru[/url]
фонтан казино бездепозитный бонус 1000 рублей за регистрацию без депозита с выводом денег Получить 1000 рублей за регистрацию с моментальным выводом, не требующим каких-либо вложений, – это мечта любого новичка онлайн-казино. Это возможность начать игру с преимуществом и испытать свою удачу без финансового риска.
Каждая выездная бригада укомплектована портативным лабораторным оборудованием для экспресс-анализов крови и мочи, современными инфузионными насосами и средствами телеметрии. Это позволяет врачу контролировать жизненно важные параметры пациента в режиме реального времени и корректировать схему детоксикации на месте.
Подробнее – [url=https://narkologicheskaya-klinika-tyumen10.ru/]наркологические клиники алкоголизм[/url]
Наркологическое лечение на дому начинается с приезда врача в течение 30-60 минут после вызова. Специалист проводит первичную диагностику состояния пациента, включая измерение артериального давления, пульса и уровня кислорода в крови, а также общую оценку тяжести интоксикации. Затем врач подбирает оптимальный состав лекарств для детоксикационной капельницы, которая эффективно очищает организм от токсинов, восстанавливает водно-солевой баланс и нормализует работу внутренних органов.
Углубиться в тему – [url=https://narcolog-na-dom-sochi00.ru/]нарколог на дом краснодарский край[/url]
Обращение к врачу становится жизненно необходимым, если пациент находится в состоянии длительного запоя, при котором организм не справляется с накоплением токсинов. Если запой продолжается более двух-трёх дней, в теле накапливаются вредные вещества, что ведёт к нарушениям работы внутренних органов, развитию абстинентного синдрома и появлению психических нарушений. Также, если у пациента наблюдаются симптомы, такие как частая рвота, спутанность сознания, судороги или резкие скачки артериального давления, это сигнал к незамедлительному вызову специалиста. При выраженной абстинентной реакции с паническими атаками, сильной дрожью, бессонницей и эмоциональной нестабильностью самостоятельное лечение может только усугубить ситуацию. Если появляются признаки алкогольного психоза – галлюцинации, агрессивность или спутанность сознания – вызов нарколога становится обязательным для предотвращения дальнейших осложнений. Также, когда требуется подготовка к процедурам кодирования от зависимости, необходима качественная детоксикация организма, что также является показанием к срочному обращению за профессиональной помощью.
Разобраться лучше – [url=https://narcolog-na-dom-ekaterinburg0.ru/]нарколог на дом анонимно[/url]
Пациенты, которые обращаются в нашу клинику за наркологической помощью, получают не просто стандартное лечение, а комплексный подход к проблеме зависимости. Наши врачи имеют большой практический опыт и высокую квалификацию, благодаря чему могут эффективно справляться даже с самыми сложными случаями. Мы используем только проверенные методики и сертифицированные препараты, гарантирующие безопасность и эффективность лечения.
Получить больше информации – [url=https://narcolog-na-dom-sochi00.ru/]вызов врача нарколога на дом[/url]
Пациенты, которые обращаются в нашу клинику за наркологической помощью, получают не просто стандартное лечение, а комплексный подход к проблеме зависимости. Наши врачи имеют большой практический опыт и высокую квалификацию, благодаря чему могут эффективно справляться даже с самыми сложными случаями. Мы используем только проверенные методики и сертифицированные препараты, гарантирующие безопасность и эффективность лечения.
Разобраться лучше – [url=https://narcolog-na-dom-sochi00.ru/]нарколог на дом вывод из запоя в сочи[/url]
1000 рублей за регистрацию вывод сразу без вложений в казино отзывы 1000 рублей без депозита
Алкогольная зависимость — сложное хроническое заболевание, требующее комплексного подхода и квалифицированной помощи. В клинике «Тюменьбезалко» в центре Тюмени разработаны эффективные программы реабилитации, сочетающие современные медицинские методы, психологическую поддержку и социальную адаптацию. Опытные врачи-наркологи и психотерапевты помогают пациентам преодолеть употребление алкоголя, восстановить физическое и эмоциональное здоровье и вернуться к полноценной жизни.
Узнать больше – [url=https://lechenie-alkogolizma-tyumen10.ru/]centr lecheniya alkogolizma tjumen'[/url]
Индивидуальный план включает детоксикацию, медикаментозную поддержку, психотерапию и реабилитацию. Специалисты учитывают:
Подробнее тут – http://lechenie-alkogolizma-tyumen10.ru/klinika-lecheniya-alkogolizma-tyumen/https://lechenie-alkogolizma-tyumen10.ru
Индивидуальный план включает детоксикацию, медикаментозную поддержку, психотерапию и реабилитацию. Специалисты учитывают:
Детальнее – [url=https://lechenie-alkogolizma-tyumen10.ru/]lechenie-alkogolizma-tyumen10.ru/[/url]
Каждый этап проводится квалифицированным специалистом, что позволяет достичь максимального терапевтического эффекта.
Подробнее можно узнать тут – [url=https://narcolog-na-dom-ekaterinburg0.ru/]запой нарколог на дом[/url]
займ под залог птс автомобиля
zaimpod-pts90.ru/kemerovo.html
кредит под залог автомобиля
Аппаратные методы кодирования включают лазерную терапию и электростимуляцию биологически активных точек, влияющих на центры зависимости в головном мозге. Эти методики способствуют быстрому формированию устойчивого отвращения к спиртному и хорошо переносятся пациентами.
Выяснить больше – https://kodirovanie-ot-alkogolizma-odintsovo2.ru/kodirovanie-ot-alkogolizma-na-domu/
?Hola, participantes de juegos emocionantes !
casino fuera de EspaГ±a con tragamonedas exclusivas – https://www.casinosonlinefueradeespanol.xyz/ casino online fuera de espaГ±a
?Que disfrutes de asombrosas exitos sobresalientes !
Обращение за медицинской помощью становится необходимым, когда пациент пребывает в состоянии, требующем немедленного вмешательства, так как самостоятельное лечение может только усугубить ситуацию. Это происходит, если запой продолжается несколько дней, и организм не успевает справляться с накопившимися токсинами, что ведёт к нарушению работы внутренних органов. Если у пациента регулярно наблюдаются симптомы, такие как частая рвота, сильное головокружение, спутанность сознания, судороги или резкие колебания артериального давления, это является явным сигналом к вызову специалиста. Особенно важно обращаться за помощью при выраженных признаках абстинентного синдрома, когда сильная дрожь, панические атаки, бессонница, тревожность и даже галлюцинации свидетельствуют о том, что организм испытывает критическую нехватку поддержки. Наличие психических нарушений, таких как агрессивное поведение, спутанность сознания или признаки алкогольного психоза, также требует незамедлительного вмешательства. В таких ситуациях обращение за профессиональной помощью помогает быстро стабилизировать состояние пациента, предотвратить развитие тяжелых осложнений и сохранить жизнь.
Выяснить больше – http://narcolog-na-dom-ekaterinburg00.ru/zapoj-narkolog-na-dom-ekb/https://narcolog-na-dom-ekaterinburg00.ru
Перед началом терапии врач собирает анамнез, оценивает состояние органов-мишеней (печень, почки, сердце), проводит лабораторные тесты на уровень электролитов и маркёры цирроза. Результаты обследования играют ключевую роль при выборе схемы инфузий и психотерапевтических методик.
Выяснить больше – [url=https://lechenie-alkogolizma-tyumen10.ru/]центр лечения алкоголизма тюменская область[/url]
кредит под залог грузового авто
zaimpod-pts90.ru
деньги под залог авто остается у вас
Оформиление дипломов ВУЗов в Москве — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы даем гарантию, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 4614 клиентов воспользовались услугой — теперь ваша очередь.
[url=http://poligraf2.ru/]Сайт компании[/url] — ответим быстро, без лишних формальностей.
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Получить дополнительную информацию – https://worldmindsetmag.com/7-second-coffee-trick
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Подробнее тут – http://tagami.com/?p=57
Этот информационный материал привлекает внимание множеством интересных деталей и необычных ракурсов. Мы предлагаем уникальные взгляды на привычные вещи и рассматриваем вопросы, которые волнуют общество. Будьте в курсе актуальных тем и расширяйте свои знания!
Выяснить больше – https://contentengine.ai/showcase-esports/content-engine/overwatch/08/13/2019/overwatch-league-season-10-schedule-is-out
В этом обзорном материале представлены увлекательные детали, которые находят отражение в различных аспектах жизни. Мы исследуем непонятные и интересные моменты, позволяя читателю увидеть картину целиком. Погрузитесь в мир знаний и удивительных открытий!
Получить дополнительную информацию – https://statuscaptions.com/what-are-the-symptoms-of-wormer-in-a-puppy.html
Понимание того, какие учреждения действительно способны помочь, позволяет избежать ошибок и не тратить время на неэффективные попытки лечения. Ключевыми признаками являются наличие медицинской лицензии, опытные специалисты, прозрачные условия и отзывы пациентов.
Получить больше информации – http://narkologicheskaya-pomoshh-arkhangelsk0.ru
Процесс терапии в клинике построен по поэтапной схеме, включающей:
Подробнее можно узнать тут – [url=https://lechenie-alkogolizma-arkhangelsk0.ru/]центр лечения алкоголизма архангельск.[/url]
Понимание того, какие учреждения действительно способны помочь, позволяет избежать ошибок и не тратить время на неэффективные попытки лечения. Ключевыми признаками являются наличие медицинской лицензии, опытные специалисты, прозрачные условия и отзывы пациентов.
Получить дополнительные сведения – http://narkologicheskaya-pomoshh-arkhangelsk0.ru
недорогие угловые маленькие кухни фото [url=https://uglovyye-kukhni-na-zakaz-1.ru]недорогие угловые маленькие кухни фото[/url] .
Процесс терапии в клинике построен по поэтапной схеме, включающей:
Разобраться лучше – [url=https://lechenie-alkogolizma-arkhangelsk0.ru/]анонимное лечение алкоголизма[/url]
Процесс терапии в клинике построен по поэтапной схеме, включающей:
Выяснить больше – [url=https://lechenie-alkogolizma-arkhangelsk0.ru/]наркология лечение алкоголизма[/url]
Анонимность — один из ключевых принципов работы клиники «Северная Звезда». Все обращения регистрируются под кодовым номером, без упоминания фамилии и контактных данных в базе данных, доступ к которой имеют только прямые исполнители процедур. Круглосуточная линия позволяет связаться со специалистом в любой момент: ночью, в праздники или выходные. Вызов врача на дом возможен в любой час, без предварительной записи, а при необходимости пациент может быть госпитализирован в отдельное крыло клиники с минимальным контактом с другими посетителями.
Узнать больше – [url=https://lechenie-alkogolizma-arkhangelsk0.ru/]анонимное лечение алкоголизма в архангельске[/url]
Автоматизированные насосы строго регулируют скорость введения препаратов. Такой подход снижает нагрузку на сердечно-сосудистую систему и минимизирует побочные эффекты.
Детальнее – http://lechenie-alkogolizma-arkhangelsk0.ru
Хотите собрать данные о человеке ? Этот бот поможет полный профиль в режиме реального времени .
Воспользуйтесь продвинутые инструменты для анализа цифровых следов в открытых источниках.
Узнайте место работы или интересы через систему мониторинга с гарантией точности .
глаз бога телеграмм официальный
Система функционирует с соблюдением GDPR, используя только открытые данные .
Закажите расширенный отчет с историей аккаунтов и графиками активности .
Доверьтесь надежному помощнику для digital-расследований — точность гарантирована!
Анонимность — один из ключевых принципов работы клиники «Северная Звезда». Все обращения регистрируются под кодовым номером, без упоминания фамилии и контактных данных в базе данных, доступ к которой имеют только прямые исполнители процедур. Круглосуточная линия позволяет связаться со специалистом в любой момент: ночью, в праздники или выходные. Вызов врача на дом возможен в любой час, без предварительной записи, а при необходимости пациент может быть госпитализирован в отдельное крыло клиники с минимальным контактом с другими посетителями.
Подробнее можно узнать тут – https://lechenie-alkogolizma-arkhangelsk0.ru/lechenie-khronicheskogo-alkogolizma-arkhangelsk
На первом приёме нарколог собирает полную клиническую картину: продолжительность зависимости, количество и частоту приёмов спиртного, наличие соматических и психических осложнений. Одновременно выполняются лабораторные тесты: общий анализ крови, биохимия (показатели работы печени и почек), электролиты. При необходимости подключаются ЭКГ и УЗИ внутренних органов, чтобы выявить скрытые патологии, влияющие на выбор терапевтической схемы.
Ознакомиться с деталями – [url=https://lechenie-alkogolizma-arkhangelsk0.ru/]lechenie-alkogolizma-arkhangelsk0.ru/[/url]
Понимание того, какие учреждения действительно способны помочь, позволяет избежать ошибок и не тратить время на неэффективные попытки лечения. Ключевыми признаками являются наличие медицинской лицензии, опытные специалисты, прозрачные условия и отзывы пациентов.
Подробнее тут – [url=https://narkologicheskaya-pomoshh-arkhangelsk0.ru/]наркологическая помощь архангельск.[/url]
Чтобы обеспечить безопасное выведение психоактивных веществ и восстановление организма, применяется детоксикация под контролем врача-нарколога и анестезиолога-реаниматолога.
Выяснить больше – [url=https://lechenie-narkomanii-arkhangelsk0.ru/]лечение наркомании и алкоголизма архангельск.[/url]
Чтобы обеспечить безопасное выведение психоактивных веществ и восстановление организма, применяется детоксикация под контролем врача-нарколога и анестезиолога-реаниматолога.
Получить дополнительную информацию – http://lechenie-narkomanii-arkhangelsk0.ru/czentr-lecheniya-narkomanii-arkhangelsk/
займы которые одобряют всем [url=https://vc.ru/dariazah/2060827-gde-poluchit-zajm-top-17-mfo] займы которые одобряют всем [/url].
“Selam forum ahalisi!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://www.rolleto.club/]rolleto[/url]”
Алкогольная зависимость — хроническое заболевание, требующее своевременного вмешательства специалистов. В условиях нашего города круглосуточная анонимная помощь позволяет начать лечение без откладываний и в привычной обстановке. Клиника «Северная Звезда» предлагает комплексный подход: вызов врача на дом или стационарное пребывание в условиях полной конфиденциальности. Профессиональная команда обеспечивает детоксикацию, психологическую реабилитацию и последующую поддержку, помогая пациенту сделать первый шаг к новой, свободной от алкоголя жизни.
Разобраться лучше – [url=https://lechenie-alkogolizma-arkhangelsk0.ru/]клиника лечения алкоголизма[/url]
Нужно собрать информацию о пользователе? Наш сервис поможет полный профиль в режиме реального времени .
Используйте уникальные алгоритмы для анализа публичных записей в открытых источниках.
Выясните место работы или активность через систему мониторинга с гарантией точности .
глаз бога сайт
Система функционирует в рамках закона , обрабатывая общедоступную информацию.
Закажите детализированную выжимку с историей аккаунтов и графиками активности .
Доверьтесь проверенному решению для исследований — точность гарантирована!
Hello champions of vitality !
Best Air Filter for Smoke – High Performance – http://bestairpurifierforcigarettesmoke.guru/# best purifier for smoke
May you experience remarkable purified harmony!
«Кодирование — это не магическое решение, а важный этап в комплексной программе лечения, — поясняет ведущий нарколог клиники «Ясное Будущее» Марина Иванова. — Главное — сочетание фармакологического воздействия и последующей работы с психологом для формирования устойчивой мотивации к трезвости».
Разобраться лучше – [url=https://kodirovanie-ot-alkogolizma-odintsovo2.ru/]https://kodirovanie-ot-alkogolizma-odintsovo2.ru[/url]
Процесс терапии в клинике построен по поэтапной схеме, включающей:
Выяснить больше – [url=https://lechenie-alkogolizma-arkhangelsk0.ru/]lechenie alkogolizma arhangel’sk[/url]
Lightweight target for all people on this web-site https://easygrawvf52.com/
Алкогольная зависимость — хроническое заболевание, требующее своевременного вмешательства специалистов. В условиях нашего города круглосуточная анонимная помощь позволяет начать лечение без откладываний и в привычной обстановке. Клиника «Северная Звезда» предлагает комплексный подход: вызов врача на дом или стационарное пребывание в условиях полной конфиденциальности. Профессиональная команда обеспечивает детоксикацию, психологическую реабилитацию и последующую поддержку, помогая пациенту сделать первый шаг к новой, свободной от алкоголя жизни.
Исследовать вопрос подробнее – [url=https://lechenie-alkogolizma-arkhangelsk0.ru/]lechenie alkogolizma arhangel’sk[/url]
«Кодирование — это не магическое решение, а важный этап в комплексной программе лечения, — поясняет ведущий нарколог клиники «Ясное Будущее» Марина Иванова. — Главное — сочетание фармакологического воздействия и последующей работы с психологом для формирования устойчивой мотивации к трезвости».
Подробнее тут – [url=https://kodirovanie-ot-alkogolizma-odintsovo2.ru/]кодирование от алкоголизма на дому[/url]
Выбор наркологической клиники — ответственное решение, от которого зависит не только эффективность терапии, но и общее физическое и психоэмоциональное состояние пациента. Квалифицированная помощь должна быть своевременной, организованной и соответствующей медицинским стандартам. Как указывает Минздрав РФ, медицинские учреждения, предоставляющие помощь при зависимостях, обязаны иметь лицензию, профессиональный персонал и комплексный подход к лечению.
Получить больше информации – [url=https://narkologicheskaya-klinika-murmansk0.ru/]наркологическая клиника в мурманске[/url]
Нередко пациенту требуется не только медикаментозная поддержка, но и психологическое сопровождение. Консультации с психотерапевтом позволяют выявить причины зависимости, снизить уровень тревожности и подготовить человека к реабилитации.
Выяснить больше – [url=https://narkologicheskaya-pomoshh-arkhangelsk0.ru/]вызов наркологической помощи в архангельске[/url]
автоломбард кредит под залог птс
zaimpod-pts90.ru/nsk.html
займ под птс без авто
На территории Мурманска работает множество клиник с разным уровнем сервиса и направленностью. Однако не каждая из них может обеспечить надёжную и безопасную помощь. Многие пациенты сталкиваются с формальным лечением, не включающим индивидуальный подход или постреабилитационную поддержку. Поэтому крайне важно заранее ознакомиться с основными признаками хорошей клиники и задать правильные вопросы при первичном обращении.
Подробнее – [url=https://narkologicheskaya-klinika-murmansk0.ru/]наркологическая клиника цены мурманск[/url]
В зависимости от состояния пациента, помощь может быть оказана в домашних условиях или в стационаре. Вызов нарколога на дом особенно актуален при абстинентном синдроме или тяжелом алкогольном опьянении. Как отмечается в материалах НМИЦ психиатрии и наркологии, в таких ситуациях крайне важно избежать самолечения и довериться врачам, способным правильно подобрать препараты и дозировки.
Углубиться в тему – [url=https://narkologicheskaya-pomoshh-arkhangelsk0.ru/]скорая наркологическая помощь архангельская область[/url]
Перевод документов https://medicaltranslate.ru на немецкий язык для лечения за границей и с немецкого после лечения: высокая скорость, безупречность, 24/7
деньги под птс без отказа
zaimpod-pts90.ru/ekb.html
деньги залог птс авто
Онлайн-тренинги https://communication-school.ru и курсы для личного роста, карьеры и новых навыков. Учитесь в удобное время из любой точки мира.
1С без сложностей https://1s-legko.ru объясняем простыми словами. Как работать в программах 1С, решать типовые задачи, настраивать учёт и избегать ошибок.
На первом этапе пациент проходит лабораторные обследования (общий и биохимический анализ крови, ЭКГ, УЗИ печени и почек). На их основе разрабатывается схема инфузионной терапии, включающая корректировку водно-электролитного баланса, поддержку жизненно важных функций и назначение симптоматических препаратов для снятия абстинентного синдрома.
Исследовать вопрос подробнее – http://lechenie-narkomanii-arkhangelsk0.ru/lechenie-narkomanii-anonimno-arkhangelsk
На первом приёме нарколог собирает полную клиническую картину: продолжительность зависимости, количество и частоту приёмов спиртного, наличие соматических и психических осложнений. Одновременно выполняются лабораторные тесты: общий анализ крови, биохимия (показатели работы печени и почек), электролиты. При необходимости подключаются ЭКГ и УЗИ внутренних органов, чтобы выявить скрытые патологии, влияющие на выбор терапевтической схемы.
Ознакомиться с деталями – [url=https://lechenie-alkogolizma-arkhangelsk0.ru/]лечение алкоголизма архангельск.[/url]
деньги под залог машины екатеринбург
zaimpod-pts91.ru/ekb.html
кредит под птс автомобиля
Нередко пациенту требуется не только медикаментозная поддержка, но и психологическое сопровождение. Консультации с психотерапевтом позволяют выявить причины зависимости, снизить уровень тревожности и подготовить человека к реабилитации.
Подробнее – [url=https://narkologicheskaya-pomoshh-arkhangelsk0.ru/]круглосуточная наркологическая помощь[/url]
Покупка дипломов ВУЗов по всей России и СНГ — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы даем гарантию, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 2436 клиентов воспользовались услугой — теперь ваша очередь.
[url=http://poligraf2.ru/]http://poligraf2.ru/[/url] — ответим быстро, без лишних формальностей.
Кодирование создаёт стойкое отвращение к этилированному спирту за счёт фармакологического или психотерапевтического воздействия, а дальнейшая работа с психологом помогает сформировать новую модель поведения и мотивацию к сохранению трезвости. Современные технологии в сочетании с индивидуальным подходом делают процедуру безопасной и максимально комфортной для пациента.
Подробнее тут – [url=https://kodirovanie-ot-alkogolizma-odintsovo2.ru/]кодирование от алкоголизма одинцово[/url]
центр наркологии наркологическая клиника телефон
частный пансионат для пожилых людей пансионат для пожилых
Выбор наркологической клиники — ответственное решение, от которого зависит не только эффективность терапии, но и общее физическое и психоэмоциональное состояние пациента. Квалифицированная помощь должна быть своевременной, организованной и соответствующей медицинским стандартам. Как указывает Минздрав РФ, медицинские учреждения, предоставляющие помощь при зависимостях, обязаны иметь лицензию, профессиональный персонал и комплексный подход к лечению.
Подробнее тут – [url=https://narkologicheskaya-klinika-murmansk0.ru/]наркологическая клиника[/url]
Этот обзорный материал предоставляет информационно насыщенные данные, касающиеся актуальных тем. Мы стремимся сделать информацию доступной и структурированной, чтобы читатели могли легко ориентироваться в наших выводах. Познайте новое с нашим обзором!
Подробнее – http://kendrasmiley.com/cropped-042-jpg/?thc-month=202110
Этот обзорный материал предоставляет информационно насыщенные данные, касающиеся актуальных тем. Мы стремимся сделать информацию доступной и структурированной, чтобы читатели могли легко ориентироваться в наших выводах. Познайте новое с нашим обзором!
Подробнее тут – https://kendrasmiley.com/cropped-042-jpg/?thc-month=201512
“Merhaba forum ahalisi!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://xturka.shop/]hemen kat?l[/url]
Slot turnuvas? yuksek oranl?.
VPN’siz erisim, tek t?kla kay?t > 10 saniyede haz?r.
Bol sans!”
авто под залог
zaimpod-pts90.ru
кредит залог птс наличные
Эта статья для ознакомления предлагает читателям общее представление об актуальной теме. Мы стремимся представить ключевые факты и идеи, которые помогут читателям получить представление о предмете и решить, стоит ли углубляться в изучение.
Детальнее – https://www.tzuchichinese.ca/index.php/2021/04/03/richmond-1
¡Hola, entusiastas del triunfo !
Casino sin licencia en EspaГ±a con jackpots progresivos – https://casinosinlicenciaespana.xyz/# mejores casinos sin licencia en espaГ±a
¡Que vivas increíbles victorias memorables !
Hello keepers of pristine spaces !
Best Air Filter for Smoke – Allergy Relief – http://bestairpurifierforcigarettesmoke.guru/# air purifier smoke
May you experience remarkable magnificent freshness !
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
Разобраться лучше – https://statuscaptions.com/12-ways-a-good-organizational-chart-helps-your-business.html
Дополнительно, если у пациента отмечаются психические нарушения — галлюцинации, агрессия или спутанность сознания, это является прямым сигналом к срочному вмешательству. В этом случае своевременное лечение помогает предотвратить риск инсульта, инфаркта или других серьезных заболеваний.
Разобраться лучше – http://vyvod-iz-zapoya-krasnodar00.ru
кредит под залог авто без отказа
zaimpod-pts90.ru/nsk.html
автоломбард займ птс
Растворы для детоксикации
Исследовать вопрос подробнее – [url=https://narcolog-na-dom-ekaterinburg00.ru/]врач нарколог на дом[/url]
Оформиление дипломов ВУЗов в Москве — с печатями, подписями, приложением и возможностью архивной записи (по запросу).
Документ максимально приближен к оригиналу и проходит визуальную проверку.
Мы даем гарантию, что в случае проверки документа, подозрений не возникнет.
– Конфиденциально
– Доставка 3–7 дней
– Любая специальность
Уже более 2526 клиентов воспользовались услугой — теперь ваша очередь.
[url=http://poligraf2.ru/]Здесь[/url] — ответим быстро, без лишних формальностей.
Обращение за медицинской помощью становится необходимым, когда пациент пребывает в состоянии, требующем немедленного вмешательства, так как самостоятельное лечение может только усугубить ситуацию. Это происходит, если запой продолжается несколько дней, и организм не успевает справляться с накопившимися токсинами, что ведёт к нарушению работы внутренних органов. Если у пациента регулярно наблюдаются симптомы, такие как частая рвота, сильное головокружение, спутанность сознания, судороги или резкие колебания артериального давления, это является явным сигналом к вызову специалиста. Особенно важно обращаться за помощью при выраженных признаках абстинентного синдрома, когда сильная дрожь, панические атаки, бессонница, тревожность и даже галлюцинации свидетельствуют о том, что организм испытывает критическую нехватку поддержки. Наличие психических нарушений, таких как агрессивное поведение, спутанность сознания или признаки алкогольного психоза, также требует незамедлительного вмешательства. В таких ситуациях обращение за профессиональной помощью помогает быстро стабилизировать состояние пациента, предотвратить развитие тяжелых осложнений и сохранить жизнь.
Подробнее тут – [url=https://narcolog-na-dom-ekaterinburg00.ru/]narcolog-na-dom-ekaterinburg00.ru/[/url]
В клинике «Нарколог-Профи» используются только проверенные и сертифицированные медикаменты, подбираемые индивидуально для каждого пациента. Ниже представлена таблица с основными группами препаратов и их функциями:
Исследовать вопрос подробнее – [url=https://narcolog-na-dom-ekaterinburg00.ru/]вызов врача нарколога на дом[/url]
Обращение за медицинской помощью становится необходимым, когда пациент пребывает в состоянии, требующем немедленного вмешательства, так как самостоятельное лечение может только усугубить ситуацию. Это происходит, если запой продолжается несколько дней, и организм не успевает справляться с накопившимися токсинами, что ведёт к нарушению работы внутренних органов. Если у пациента регулярно наблюдаются симптомы, такие как частая рвота, сильное головокружение, спутанность сознания, судороги или резкие колебания артериального давления, это является явным сигналом к вызову специалиста. Особенно важно обращаться за помощью при выраженных признаках абстинентного синдрома, когда сильная дрожь, панические атаки, бессонница, тревожность и даже галлюцинации свидетельствуют о том, что организм испытывает критическую нехватку поддержки. Наличие психических нарушений, таких как агрессивное поведение, спутанность сознания или признаки алкогольного психоза, также требует незамедлительного вмешательства. В таких ситуациях обращение за профессиональной помощью помогает быстро стабилизировать состояние пациента, предотвратить развитие тяжелых осложнений и сохранить жизнь.
Детальнее – [url=https://narcolog-na-dom-ekaterinburg00.ru/]нарколог на дом анонимно екатеринбург[/url]
Группа препаратов
Выяснить больше – [url=https://narcolog-na-dom-ekaterinburg00.ru/]вызов нарколога на дом свердловская область[/url]
Растворы для детоксикации
Подробнее – [url=https://narcolog-na-dom-ekaterinburg00.ru/]vyzvat-narkologa-na-dom ekaterinburg[/url]
Обращение за медицинской помощью становится необходимым, когда пациент пребывает в состоянии, требующем немедленного вмешательства, так как самостоятельное лечение может только усугубить ситуацию. Это происходит, если запой продолжается несколько дней, и организм не успевает справляться с накопившимися токсинами, что ведёт к нарушению работы внутренних органов. Если у пациента регулярно наблюдаются симптомы, такие как частая рвота, сильное головокружение, спутанность сознания, судороги или резкие колебания артериального давления, это является явным сигналом к вызову специалиста. Особенно важно обращаться за помощью при выраженных признаках абстинентного синдрома, когда сильная дрожь, панические атаки, бессонница, тревожность и даже галлюцинации свидетельствуют о том, что организм испытывает критическую нехватку поддержки. Наличие психических нарушений, таких как агрессивное поведение, спутанность сознания или признаки алкогольного психоза, также требует незамедлительного вмешательства. В таких ситуациях обращение за профессиональной помощью помогает быстро стабилизировать состояние пациента, предотвратить развитие тяжелых осложнений и сохранить жизнь.
Получить дополнительную информацию – [url=https://narcolog-na-dom-ekaterinburg00.ru/]нарколог на дом круглосуточно[/url]
Мы понимаем, что каждая минута имеет решающее значение, поэтому наши специалисты готовы выехать на дом в кратчайшие сроки и провести все необходимые процедуры по детоксикации организма. Наша цель — помочь пациенту вернуться к нормальной жизни без лишних стрессов и рискованных попыток самостоятельного лечения.
Получить дополнительную информацию – [url=https://vyvod-iz-zapoya-krasnodar00.ru/]вывод из запоя на дому цена в краснодаре[/url]
Чем раньше нарколог окажет помощь, тем выше шансы избежать осложнений и восстановиться без последствий для здоровья.
Подробнее можно узнать тут – [url=https://narcolog-na-dom-sochi0.ru/]врач нарколог на дом сочи[/url]
В клинике «Нарколог-Профи» используются только проверенные и сертифицированные медикаменты, подбираемые индивидуально для каждого пациента. Ниже представлена таблица с основными группами препаратов и их функциями:
Исследовать вопрос подробнее – [url=https://narcolog-na-dom-ekaterinburg00.ru/]вызвать нарколога на дом[/url]
Вызов нарколога на дом становится необходимым при любых состояниях, когда отказ от алкоголя сопровождается выраженными симптомами интоксикации и абстиненции. Основные ситуации, в которых срочно требуется профессиональная помощь врача:
Подробнее – [url=https://narcolog-na-dom-sochi0.ru/]вызвать нарколога на дом[/url]
“Selam forum ahalisi!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://XturkaOnline.com/]Xturka guvenilir mi[/url]
Rulet masas? 24/7 ac?k.
VPN’siz erisim, tek t?kla kay?t > 15 saniyede haz?r.
Sans?n? art?r!”
Клиника «Нарколог-Профи» предлагает круглосуточную помощь на дому в Екатеринбурге и Свердловской области. Наши опытные специалисты готовы оперативно приехать по вашему вызову и оказать экстренную медицинскую поддержку при алкогольной или наркотической зависимости. Мы проводим детоксикацию организма, купируем абстинентный синдром и стабилизируем состояние пациента, обеспечивая при этом полную конфиденциальность и комфорт в домашних условиях.
Выяснить больше – [url=https://narcolog-na-dom-ekaterinburg00.ru/]www.domen.ru[/url]
Клиника «Нарколог-Профи» предлагает круглосуточную помощь на дому в Екатеринбурге и Свердловской области. Наши опытные специалисты готовы оперативно приехать по вашему вызову и оказать экстренную медицинскую поддержку при алкогольной или наркотической зависимости. Мы проводим детоксикацию организма, купируем абстинентный синдром и стабилизируем состояние пациента, обеспечивая при этом полную конфиденциальность и комфорт в домашних условиях.
Ознакомиться с деталями – [url=https://narcolog-na-dom-ekaterinburg00.ru/]нарколог на дом вывод из запоя в екатеринбурге[/url]
кредит наличными под залог автомобиля
zaimpod-pts92.ru/kazan.html
кредит под птс авто
Южнокорейский сериал о смертельных играх на выживание ради огромного денежного приза. Сотни отчаявшихся людей участвуют в детских играх, где проигрыш означает смерть. Сериал исследует темы социального неравенства, морального выбора и человеческой природы в экстремальных условиях: игра в кальмара 3 сезон бесплатно
Алкогольная зависимость — это хроническое заболевание, при котором устойчивое влечение к спиртному приводит к тяжёлым медицинским, социальным и психологическим последствиям. Когда пациент осознаёт, что самостоятельно справиться с этой проблемой не получается, наиболее эффективным методом становится кодирование от алкоголизма. В клинике «Ясное Будущее» в Одинцово мы используем сочетание проверенных методик кодирования и комплексной психологической поддержки, что позволяет достичь стойкой ремиссии и вернуть человеку контроль над собственной жизнью.
Ознакомиться с деталями – [url=https://kodirovanie-ot-alkogolizma-odintsovo2.ru/]centr kodirovaniya ot alkogolizma[/url]
Дополнительно, если у пациента отмечаются психические нарушения — галлюцинации, агрессия или спутанность сознания, это является прямым сигналом к срочному вмешательству. В этом случае своевременное лечение помогает предотвратить риск инсульта, инфаркта или других серьезных заболеваний.
Получить дополнительную информацию – http://vyvod-iz-zapoya-krasnodar00.ru/vyvod-iz-zapoya-czena-krasnodar/
Кодирование создаёт стойкое отвращение к этилированному спирту за счёт фармакологического или психотерапевтического воздействия, а дальнейшая работа с психологом помогает сформировать новую модель поведения и мотивацию к сохранению трезвости. Современные технологии в сочетании с индивидуальным подходом делают процедуру безопасной и максимально комфортной для пациента.
Ознакомиться с деталями – [url=https://kodirovanie-ot-alkogolizma-odintsovo2.ru/]кодирование от алкоголизма довженко[/url]
Длительный запой способен нанести непоправимый вред организму, привести к тяжелым нарушениям работы внутренних органов и поставить под угрозу жизнь пациента. В таких случаях необходимо срочное медицинское вмешательство, которое позволяет быстро стабилизировать состояние, вывести токсины и предотвратить развитие опасных осложнений. Клиника «ЗдоровьеНорм» в Краснодаре предлагает профессиональный вывод из запоя на дому, обеспечивая комплексное лечение с максимальной оперативностью и полной конфиденциальностью.
Углубиться в тему – https://vyvod-iz-zapoya-krasnodar00.ru/vyvod-iz-zapoya-na-domu-krasnodar/
юридическая помощь нужен сайт адвоката
קדימה! אל תהססו. מזוקן ניגש עם מכנסיו למטה והתחיל לעבוד על הזין בישבן שלי. הסתובבתי.: – רק עובד. שלושתם אני אתה ולנה. אתה מוכן, יש לך רצון, אתה עומד, ועומד היטב. אם אתה מטפס עלי, או The most charming Jerusalem escorts girls make men happy
Дополнительно, если у пациента отмечаются психические нарушения — галлюцинации, агрессия или спутанность сознания, это является прямым сигналом к срочному вмешательству. В этом случае своевременное лечение помогает предотвратить риск инсульта, инфаркта или других серьезных заболеваний.
Изучить вопрос глубже – [url=https://vyvod-iz-zapoya-krasnodar00.ru/]вывод из запоя клиника в краснодаре[/url]
Растворы для детоксикации
Выяснить больше – [url=https://narcolog-na-dom-ekaterinburg00.ru/]выезд нарколога на дом[/url]
деньги под залог машины
zaimpod-pts91.ru/kazan.html
деньги под залог авто птс
Дополнительно, если у пациента отмечаются психические нарушения — галлюцинации, агрессия или спутанность сознания, это является прямым сигналом к срочному вмешательству. В этом случае своевременное лечение помогает предотвратить риск инсульта, инфаркта или других серьезных заболеваний.
Детальнее – http://vyvod-iz-zapoya-krasnodar00.ru
Вызов нарколога на дом становится необходимым при любых состояниях, когда отказ от алкоголя сопровождается выраженными симптомами интоксикации и абстиненции. Основные ситуации, в которых срочно требуется профессиональная помощь врача:
Выяснить больше – [url=https://narcolog-na-dom-sochi0.ru/]нарколог на дом срочно в сочи[/url]
В нашей клинике применяются различные техники кодирования, которые подбираются с учётом медицинских показаний, психологического состояния и пожеланий пациента.
Получить дополнительные сведения – http://kodirovanie-ot-alkogolizma-odintsovo2.ru/
займ под залог птс авто в москве
zaimpod-pts92.ru
взять кредит под птс автомобиля
Мы понимаем, что каждая минута имеет решающее значение, поэтому наши специалисты готовы выехать на дом в кратчайшие сроки и провести все необходимые процедуры по детоксикации организма. Наша цель — помочь пациенту вернуться к нормальной жизни без лишних стрессов и рискованных попыток самостоятельного лечения.
Разобраться лучше – [url=https://vyvod-iz-zapoya-krasnodar00.ru/]вывод из запоя круглосуточно краснодар[/url]
Мы понимаем, что каждая минута имеет решающее значение, поэтому наши специалисты готовы выехать на дом в кратчайшие сроки и провести все необходимые процедуры по детоксикации организма. Наша цель — помочь пациенту вернуться к нормальной жизни без лишних стрессов и рискованных попыток самостоятельного лечения.
Подробнее – [url=https://vyvod-iz-zapoya-krasnodar00.ru/]вывод из запоя на дому цена краснодар[/url]
Мы понимаем, что каждая минута имеет решающее значение, поэтому наши специалисты готовы выехать на дом в кратчайшие сроки и провести все необходимые процедуры по детоксикации организма. Наша цель — помочь пациенту вернуться к нормальной жизни без лишних стрессов и рискованных попыток самостоятельного лечения.
Получить больше информации – [url=https://vyvod-iz-zapoya-krasnodar00.ru/]www.domen.ru[/url]
“Hey bahisseverler!
?? %300 Hosgeldin Bonusu + %50 Crypto Deposit + %20 Cashback sizi bekliyor.
Yeni adres > [url=https://BetturkeyGiris2025.net/]bol sans[/url]
Canl? bahis yuksek oranl?.
VPN’siz erisim, tek t?kla kay?t > 20 saniyede haz?r.
Sans?n? art?r!”
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Ознакомиться с деталями – https://glengarryvet.ca/hello-world
типография заказать типография цены
типография печать типография спб дешево
металлические значки на заказ металлические значки москва
אותה והכוס שלי היה מתוח. אה, והנה זה, זרם האורגזמה המיוחל. גופי רעד, ובפנים הכל התחיל השפיך שלי, היא דחפה אותו החוצה. נוזל לבן התפשט על שפתיה, סנטרה, צווארה וציצי היופי. היא זרחה סקס דירות דיסקרטיות
мфо 2025 с 18 лет [url=https://vc.ru/tg-raiting/2060767-mfo-zajmy-s-18-let-kruglosutochno] мфо 2025 с 18 лет [/url].