This document provides a detailed analysis of a security vulnerability discovered in a web application that allows for JavaScript injection through concatenated input fields. The analysis covers the severity of the vulnerability, its potential impacts on various stakeholders, technical implications, compliance risks, and proposed resolution steps. By understanding the ramifications of this issue, organizations can take proactive measures to safeguard their applications and user data.

Scenario Overview
A security vulnerability is discovered in a web application where user input fields for First Name, Middle Name, and Last Name fail to sanitize individual input values properly. As a result, malicious users can inject fragmented JavaScript code into these fields that, when concatenated, forms an executable script on the client-side.
- First Name:
<script - Middle Name:
>{maliciousCode}< - Last Name:
/script>
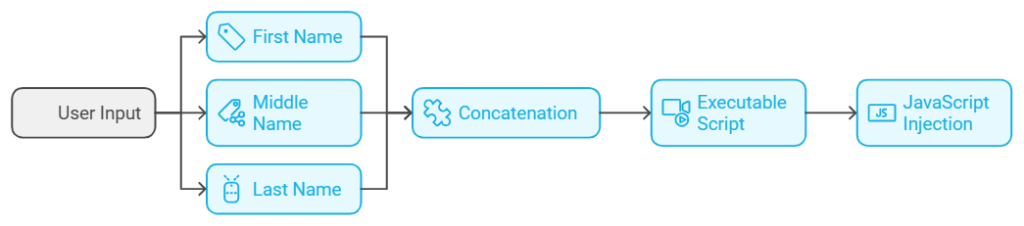
When the application concatenates these inputs, the output becomes <script>{maliciousCode}</script>, enabling a cross-site scripting (XSS) attack.
Impact Analysis
1. Severity and Exploit Potential
- Attack Vector: The vulnerability leverages input fields that are concatenated and rendered on a webpage. Attackers can inject scripts to exploit the application.
- Impact Area:
- Client-side attacks (browser hijacking).
- Theft of sensitive user data (e.g., session cookies, tokens).
- Altered UI behavior or phishing attacks.
- Reproducibility: Since the input concatenation process is consistent, the exploit is highly reproducible.
2. Impacts on Different Stakeholders
- End Users:
- Compromised accounts due to stolen session cookies.
- Exposure to phishing attempts or malicious redirections.
- Organization:
- Loss of user trust and potential legal liability under GDPR/CCPA regulations if user data is compromised.
- Negative brand reputation and possible loss of revenue.
- Increased development costs for patching and securing the system.
- Attackers:
- Opportunity to launch mass XSS campaigns.
- Gain unauthorized access to sensitive resources.

3. Technical Impact on the System
- Data Integrity: Malicious scripts can manipulate displayed data, leading to incorrect or misleading information.
- System Performance: Increased resource utilization if scripts execute additional, unintended actions (e.g., repeated API calls).
- Integration Risk: If the system interacts with third-party APIs or services, malicious scripts could propagate or trigger unexpected behavior.

4. Compliance and Legal Risks
- Violations of security standards (e.g., OWASP Top 10 – A03:2021 for XSS).
- Penalties due to failure to ensure data safety and application integrity.
Resolution Steps
Immediate Mitigation:
- Disable rendering of concatenated input temporarily.
- Deploy a hotfix to escape or sanitize all special characters (
<,>,&, etc.) within input fields. - Monitor logs for malicious activity and identify affected users.
Long-term Fixes:
- Implement proper input validation and sanitization at every point of user data handling.
- Use a security library or framework to handle input escaping (e.g., OWASP ESAPI).
- Apply Content Security Policy (CSP) headers to limit script execution.
- Integrate automated tools to detect and prevent injection vulnerabilities during the development lifecycle.
Testing & Validation:
- Conduct comprehensive security testing, including manual and automated XSS tests.
- Ensure input handling logic is robust for all combinations of fragmented or partial script tags.
- Validate edge cases for concatenated inputs.
By addressing these vulnerabilities and implementing the proposed resolution steps, organizations can significantly reduce the risk of JavaScript injection attacks and protect their users from potential harm.
More Bug Case Studies Here: https://testtales.com/category/bug-impact-analysis/